Discover the Powerful Cryptographic Benefits of Blake-3 Hashing Algorithm 🔐
Learn how Blake-3 offers enhanced security and performance advantages over other hashing algorithms in cryptography. Explore its key features and why it’s a game-changer.

Stephen Blum
761 views • Dec 21, 2023
About this video
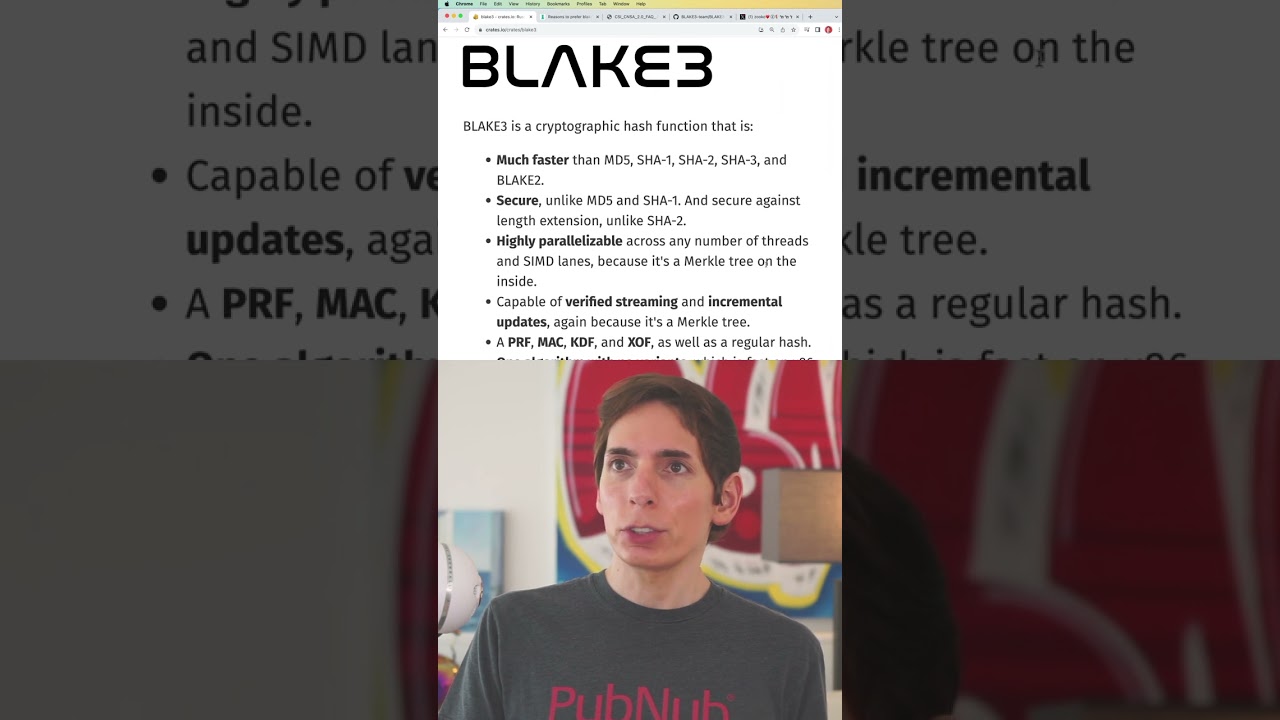
Blake-3 is a cryptographic hashing algorithm with benefits over some other hashing methods. There are several things to think about in a cryptographic hashing algorithm. The most crucial thing is, how secure is it?
Can we easily break it? Can a lot of computing power crack it? Those are not good signs.
We need to look at how much computation is needed to create a hash from the data it's working with. We then compare this to other algorithms to see how well it does. The first thing I looked for with Blake-3 was how often it has collisions.
When we need to store key data like a password, we don't hold the actual text. Instead, we sign it cryptographically and save that signature in a storage system. This stops anyone else from using the password.
Even the people who save that data won't know what the password is. That's why this is so important. The only person with the password is you.
For collisions, you wouldn't want another different password to give the same result, right? It's like one person's password is 'apple,' while yours is 'orange'. A cryptographic function could take both of these and output the same result, and that would be a collision.
This is bad because it means that an attacker could use 'orange' even if your password is 'apple'. With Blake-3, I didn't see anything about collisions. Clearly, that's a huge part of how secure it is.
We'll still look at what is mentioned to see if there are any situations where it might be more secure to use Blake-3 than SHA-256.
Can we easily break it? Can a lot of computing power crack it? Those are not good signs.
We need to look at how much computation is needed to create a hash from the data it's working with. We then compare this to other algorithms to see how well it does. The first thing I looked for with Blake-3 was how often it has collisions.
When we need to store key data like a password, we don't hold the actual text. Instead, we sign it cryptographically and save that signature in a storage system. This stops anyone else from using the password.
Even the people who save that data won't know what the password is. That's why this is so important. The only person with the password is you.
For collisions, you wouldn't want another different password to give the same result, right? It's like one person's password is 'apple,' while yours is 'orange'. A cryptographic function could take both of these and output the same result, and that would be a collision.
This is bad because it means that an attacker could use 'orange' even if your password is 'apple'. With Blake-3, I didn't see anything about collisions. Clearly, that's a huge part of how secure it is.
We'll still look at what is mentioned to see if there are any situations where it might be more secure to use Blake-3 than SHA-256.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
761
Likes
12
Duration
1:00
Published
Dec 21, 2023
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.