DEF CON 19: Adam Baldwin Reveals How to Exploit and Profit from DVCS Repositories 🚀
Discover insights from Adam Baldwin's DEF CON 19 presentation on how to analyze and leverage distributed version control systems for security research and potential profit. Learn the techniques and implications behind DVCS exploitation.

DEFCONConference
383 views • Nov 2, 2013
About this video
Adam Baldwin - Pillaging DVCS Repos For Fun And Profit
https://www.defcon.org/images/defcon-19/dc-19-presentations/Baldwin/DEFCON-19-Baldwin-DVCS.pdf
White Paper Here: https://www.defcon.org/images/defcon-19/dc-19-presentations/Baldwin/DEFCON-19-Baldwin-DVCS-WP.pdf
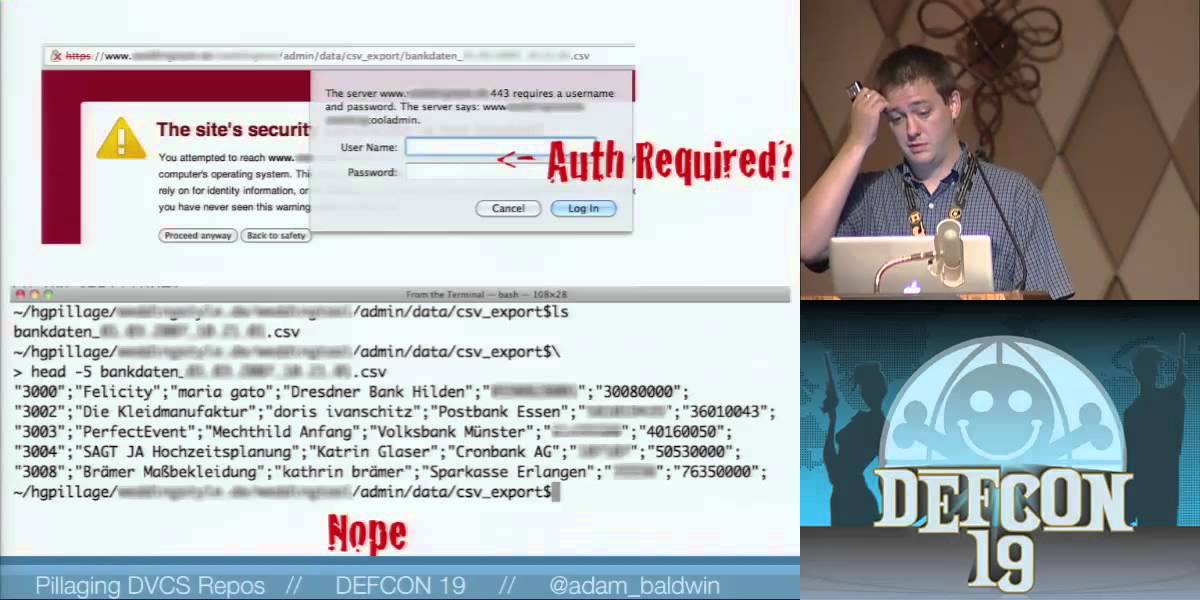
Distributed Version Control Systems, like git are becoming an increasingly popular way to deploy web applications and web related resources. Our research shows these repositories commonly contain information very useful to an attacker. This talk, which was part of my small contribution to the Penetration Testing Execution Standard (PTES) will demonstrate how to identify these repositories and techniques to pillage just as much information as possible from them. Lastly there will be release of a toolkit to automate the the discussed techniques supporting git, hg and bzr repositories!
Adam Baldwin has over 10+ years of mostly self taught computer security experience and currently is the co-founder and Chief Pwning Officer at nGenuity focusing on security of web applications. He at one time possessed a GCIA and if his CPE's are up to date should still have a CISSP. Prior to starting nGenuity Adam worked for Symantec. Adam is a minor contributor to the W3AF project and has previously spoke at Toorcamp, Djangcon 2010, and JSconf 2011.
https://www.defcon.org/images/defcon-19/dc-19-presentations/Baldwin/DEFCON-19-Baldwin-DVCS.pdf
White Paper Here: https://www.defcon.org/images/defcon-19/dc-19-presentations/Baldwin/DEFCON-19-Baldwin-DVCS-WP.pdf
Distributed Version Control Systems, like git are becoming an increasingly popular way to deploy web applications and web related resources. Our research shows these repositories commonly contain information very useful to an attacker. This talk, which was part of my small contribution to the Penetration Testing Execution Standard (PTES) will demonstrate how to identify these repositories and techniques to pillage just as much information as possible from them. Lastly there will be release of a toolkit to automate the the discussed techniques supporting git, hg and bzr repositories!
Adam Baldwin has over 10+ years of mostly self taught computer security experience and currently is the co-founder and Chief Pwning Officer at nGenuity focusing on security of web applications. He at one time possessed a GCIA and if his CPE's are up to date should still have a CISSP. Prior to starting nGenuity Adam worked for Symantec. Adam is a minor contributor to the W3AF project and has previously spoke at Toorcamp, Djangcon 2010, and JSconf 2011.
Video Information
Views
383
Likes
2
Duration
16:21
Published
Nov 2, 2013
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.