Cryptosystem Full Walkthrough 2025: Cracking Flawed RSA Step-by-Step 🔓
Discover how a simple vulnerability can compromise RSA encryption in this comprehensive TryHackMe walkthrough. Perfect for enthusiasts eager to master cryptography challenges!

Djalil Ayed
418 views • Jul 5, 2025
About this video
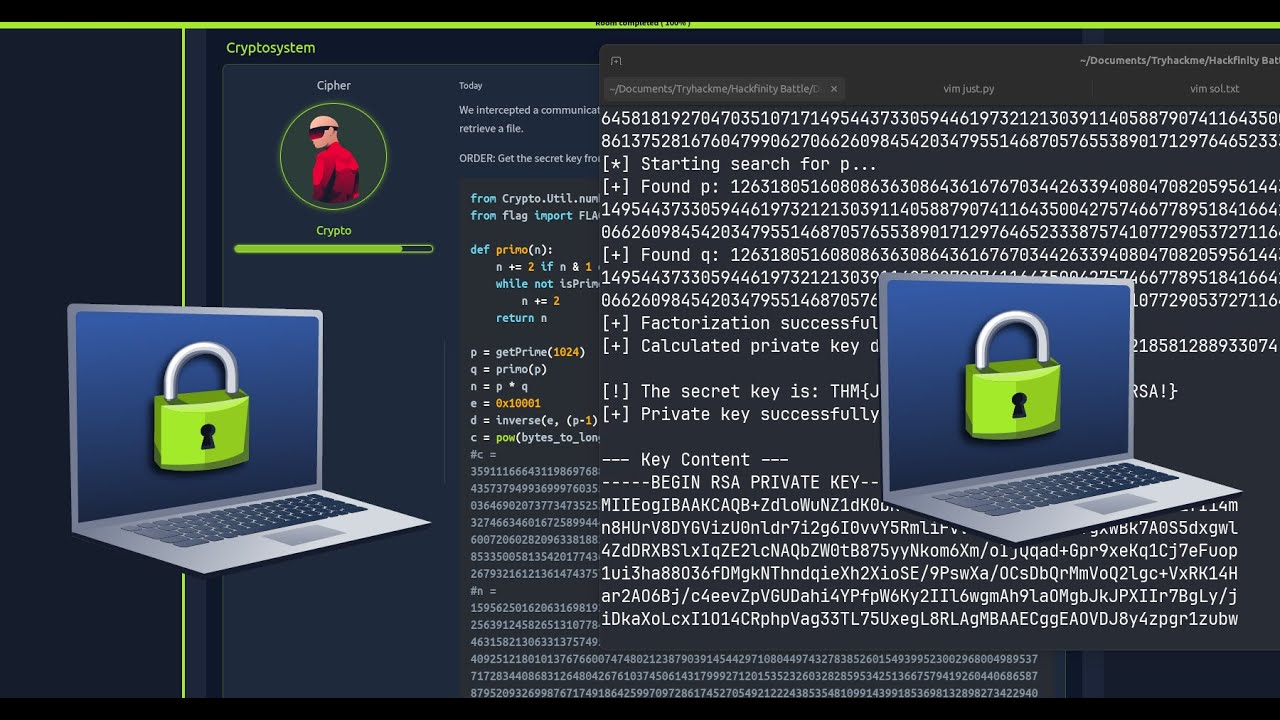
🎯Have you ever wondered how a tiny mistake can bring down a powerful cryptographic system like RSA? In this video, we dive into a Capture The Flag (CTF) challenge where a flawed key generation process leaves RSA wide open to attack!
🎯We'll analyze a Python script that generates an RSA key pair with two primes, p and q, that are dangerously close to each other. This is a classic vulnerability that allows us to bypass the security of RSA by using Fermat's Factorization Method to find the private key.
🎯Join me as we walk through the entire process, from analyzing the vulnerable code to recovering the secret flag.
This guide is perfect for anyone interested in ethical hacking, cryptography, cybersecurity, or CTF competitions.
🔗 **Room:** https://tryhackme.com/room/hfb1cryptosystem
🔗🎯🏷️ ** Script Used in the room https://github.com/djalilayed/tryhackme/blob/f83ddefa3dea53d15b4c4c324b4355fa44f182f6/Hackfinity%20Battle/Cryptosystem/decrypt.py
🏷️🏷️Resources:
🏷️CyberChef: https://gchq.github.io/CyberChef
🏷️Python pycryptodome library
If you enjoyed this video and learned something new, please hit the like button, leave a comment with your thoughts, and subscribe for more cybersecurity content!
#RSA #Cryptography #CTF #CyberSecurity #Hacking #Python #ethicalhacking
🔔🔔 **Disclaimer:** This video is for educational purposes only. The techniques and challenges shown are performed in a controlled and legal environment (TryHackMe). Hacking without permission is illegal.
🎯We'll analyze a Python script that generates an RSA key pair with two primes, p and q, that are dangerously close to each other. This is a classic vulnerability that allows us to bypass the security of RSA by using Fermat's Factorization Method to find the private key.
🎯Join me as we walk through the entire process, from analyzing the vulnerable code to recovering the secret flag.
This guide is perfect for anyone interested in ethical hacking, cryptography, cybersecurity, or CTF competitions.
🔗 **Room:** https://tryhackme.com/room/hfb1cryptosystem
🔗🎯🏷️ ** Script Used in the room https://github.com/djalilayed/tryhackme/blob/f83ddefa3dea53d15b4c4c324b4355fa44f182f6/Hackfinity%20Battle/Cryptosystem/decrypt.py
🏷️🏷️Resources:
🏷️CyberChef: https://gchq.github.io/CyberChef
🏷️Python pycryptodome library
If you enjoyed this video and learned something new, please hit the like button, leave a comment with your thoughts, and subscribe for more cybersecurity content!
#RSA #Cryptography #CTF #CyberSecurity #Hacking #Python #ethicalhacking
🔔🔔 **Disclaimer:** This video is for educational purposes only. The techniques and challenges shown are performed in a controlled and legal environment (TryHackMe). Hacking without permission is illegal.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
418
Likes
7
Duration
15:53
Published
Jul 5, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.