Cryptography Explained: Symmetric vs. Asymmetric Keys with Practical Linux Examples 🔐
Discover the fundamentals of cryptography, including clear examples of symmetric and asymmetric key encryption in Linux. Perfect for beginners wanting to understand secure data protection!

HowToOps
675 views • Aug 5, 2018
About this video
This video covers both symmetric or asymmetric key cryptography with 100% practical example in Linux.
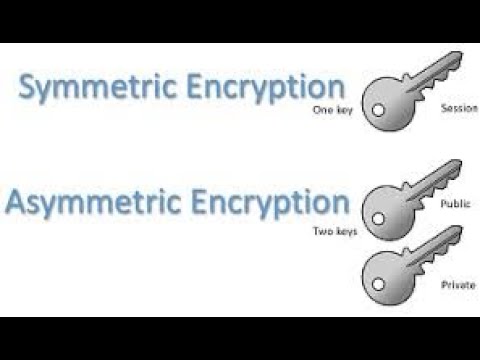
Q. What is symmetric key cryptography ?
Ans. Symmetric key cryptography (or symmetric encryption) is a type of encryption scheme in which the same key is used both to encrypt and decrypt messages. Such a method of encoding information has been largely used in the past decades to facilitate secret communication between governments and militaries. Nowadays, symmetric key algorithms are widely applied in various types of computer systems to enhance data security.
Q. What is asymmetric key cryptography ?
Ans. Asymmetric cryptography, also known as public-key cryptography, is a process that uses a pair of related keys -- one public key and one private key -- to encrypt and decrypt a message and protect it from unauthorized access or use. A public key is a cryptographic key that can be used by any person to encrypt a message so that it can only be deciphered by the intended recipient with their private key. A private key -- also known as a secret key -- is shared only with key's initiator.
----------------MUST WATCH-----------------
AWS TUTORIAL: HOW TO SECURE WEBSITE SERVED BY AWS S3 BUCKET
link ---- https://youtu.be/6gd6CEDDmrk
EMAIL SPOOFING ATTACK: [SEND EMAIl WITH FAKE EMAIL ADDRESS] :USING KALI LINUX
link -------- https://youtu.be/43runXHGbIc
HOW TO HOST WEBSITE ON DEEP WEB / DARK NET / TOR
link ------ -- https://youtu.be/hlkoTnn3GS8
HOW TO HIDE YOUR PUBLIC IP : [ STAY ANONYMOUS ]
link ----------- https://youtu.be/KXgnCNHm_2s
HOW TO:CONFIGURE HA-PROXY SERVER (LOAD BALANCER)
link --------------- https://youtu.be/TkiGgUkn_PI
Data recovery using kali linux [Recover formatted data]
link ------------- https://youtu.be/lHjM2_ol6_0
Q. What is symmetric key cryptography ?
Ans. Symmetric key cryptography (or symmetric encryption) is a type of encryption scheme in which the same key is used both to encrypt and decrypt messages. Such a method of encoding information has been largely used in the past decades to facilitate secret communication between governments and militaries. Nowadays, symmetric key algorithms are widely applied in various types of computer systems to enhance data security.
Q. What is asymmetric key cryptography ?
Ans. Asymmetric cryptography, also known as public-key cryptography, is a process that uses a pair of related keys -- one public key and one private key -- to encrypt and decrypt a message and protect it from unauthorized access or use. A public key is a cryptographic key that can be used by any person to encrypt a message so that it can only be deciphered by the intended recipient with their private key. A private key -- also known as a secret key -- is shared only with key's initiator.
----------------MUST WATCH-----------------
AWS TUTORIAL: HOW TO SECURE WEBSITE SERVED BY AWS S3 BUCKET
link ---- https://youtu.be/6gd6CEDDmrk
EMAIL SPOOFING ATTACK: [SEND EMAIl WITH FAKE EMAIL ADDRESS] :USING KALI LINUX
link -------- https://youtu.be/43runXHGbIc
HOW TO HOST WEBSITE ON DEEP WEB / DARK NET / TOR
link ------ -- https://youtu.be/hlkoTnn3GS8
HOW TO HIDE YOUR PUBLIC IP : [ STAY ANONYMOUS ]
link ----------- https://youtu.be/KXgnCNHm_2s
HOW TO:CONFIGURE HA-PROXY SERVER (LOAD BALANCER)
link --------------- https://youtu.be/TkiGgUkn_PI
Data recovery using kali linux [Recover formatted data]
link ------------- https://youtu.be/lHjM2_ol6_0
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
675
Likes
10
Duration
12:39
Published
Aug 5, 2018
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now