Cryptography 101: Master Symmetric & Asymmetric Encryption + Spot Security Flaws 🔐
Learn the fundamentals of symmetric and asymmetric cryptography, and discover how to identify common security vulnerabilities. Boost your cybersecurity skills today! 🚀

Petrina Corine
25 views • Nov 7, 2020
About this video
Link to this course:
https://click.linksynergy.com/deeplink?id=Gw/ETjJoU9M&mid=40328&murl=https%3A%2F%2Fwww.coursera.org%2Flearn%2Fidentifying-security-vulnerabilities
Cryptography Basics: Symmetric and Asymmetric Cryptography - Identifying Security Vulnerabilities
Secure Coding Practices Specialization
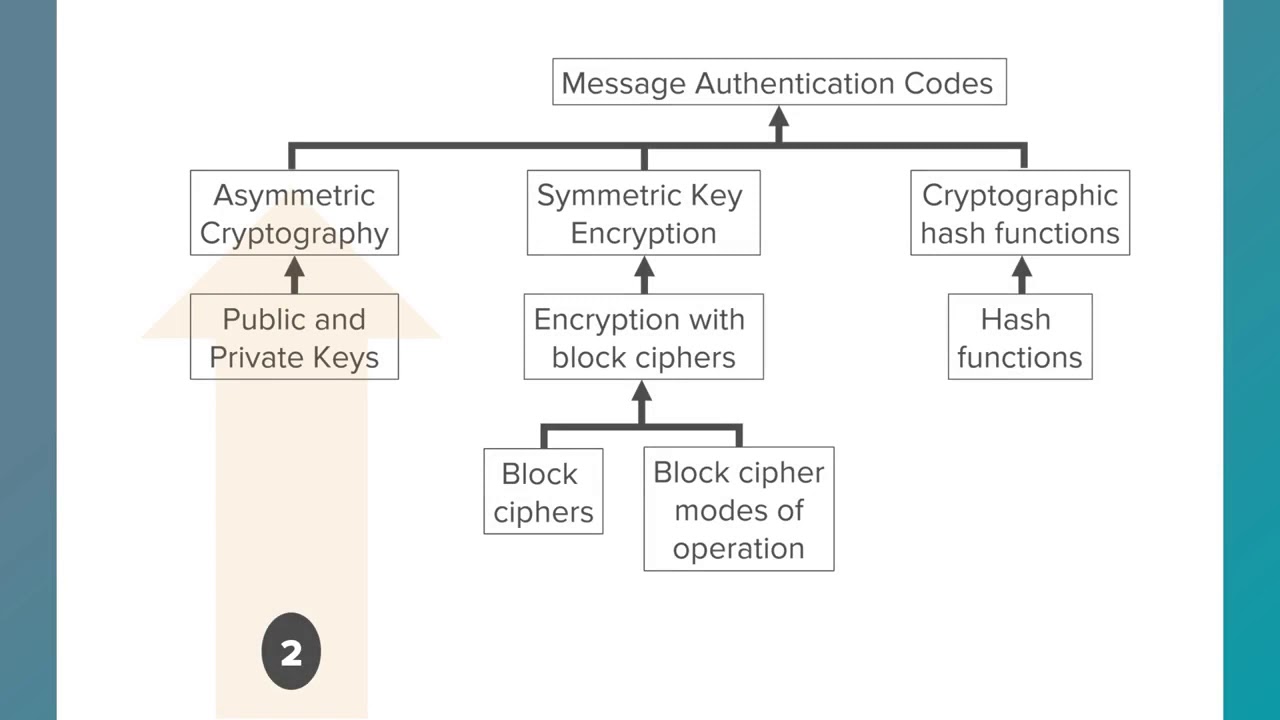
This course will help you build a foundation of some of the fundamental concepts in secure programming. We will learn about the concepts of threat modeling and cryptography and you'll be able to start to create threat models, and think critically about the threat models created by other people. We'll learn the basics of applying cryptography, such as encryption and secure hashing. We'll learn how attackers can exploit application vulnerabilities through the improper handling user-controlled data. We'll gain a fundamental understanding of injection problems in web applications, including the three most common types of injection problems: SQL injection, cross-site scripting, and command injection.
We'll also cover application authentication and session management where authentication is a major component of a secure web application and session management is the other side of the same coin, since the authenticated state of user requests need to be properly handled and run as one session. We'll learn about sensitive data exposure issues and how you can help protect your customer's data. We'll cover how to effectively store password-related information, and not to store the actual plaintext passwords. We'll participate in coding assignment that will help you to better understand the mechanisms for effectively storing password-related information.
Along the way, we’ll discuss ways of watching out for and mitigating these issues and be able have some fun and exploit two different vulnerabilities in a web application that was designed to be vulnerable, called WebGoat.
Cryptography, Authentication Methods, secure programming
Threat Modeling and Week 4 code submission was very fruitful. Overall good content to learn for developers and Application Engineers.,This class was awesome, it was challenging, and caused me to grow toward my goal of being in Cyber security! Thanks!
In this module, you will gain exposure to the ideas of threat modeling and applied cryptography. By the end of the module, you will be able to start to create threat models, and think critically about the threat models created by other people. You will be able to apply the STRIDE Method to your threat model and distinguish the trust boundaries in a given system. You will also gain a basic understanding of applied cryptography, such as encryption and secure hashing.
Cryptography Basics: Symmetric and Asymmetric Cryptography - Identifying Security Vulnerabilities
Copyright Disclaimer under Section 107 of the copyright act 1976, allowance is made for fair use for purposes such as criticism, comment, news reporting, scholarship, and research. Fair use is a use permitted by copyright statute that might otherwise be infringing. Non-profit, educational or personal use tips the balance in favour of fair use.
https://click.linksynergy.com/deeplink?id=Gw/ETjJoU9M&mid=40328&murl=https%3A%2F%2Fwww.coursera.org%2Flearn%2Fidentifying-security-vulnerabilities
Cryptography Basics: Symmetric and Asymmetric Cryptography - Identifying Security Vulnerabilities
Secure Coding Practices Specialization
This course will help you build a foundation of some of the fundamental concepts in secure programming. We will learn about the concepts of threat modeling and cryptography and you'll be able to start to create threat models, and think critically about the threat models created by other people. We'll learn the basics of applying cryptography, such as encryption and secure hashing. We'll learn how attackers can exploit application vulnerabilities through the improper handling user-controlled data. We'll gain a fundamental understanding of injection problems in web applications, including the three most common types of injection problems: SQL injection, cross-site scripting, and command injection.
We'll also cover application authentication and session management where authentication is a major component of a secure web application and session management is the other side of the same coin, since the authenticated state of user requests need to be properly handled and run as one session. We'll learn about sensitive data exposure issues and how you can help protect your customer's data. We'll cover how to effectively store password-related information, and not to store the actual plaintext passwords. We'll participate in coding assignment that will help you to better understand the mechanisms for effectively storing password-related information.
Along the way, we’ll discuss ways of watching out for and mitigating these issues and be able have some fun and exploit two different vulnerabilities in a web application that was designed to be vulnerable, called WebGoat.
Cryptography, Authentication Methods, secure programming
Threat Modeling and Week 4 code submission was very fruitful. Overall good content to learn for developers and Application Engineers.,This class was awesome, it was challenging, and caused me to grow toward my goal of being in Cyber security! Thanks!
In this module, you will gain exposure to the ideas of threat modeling and applied cryptography. By the end of the module, you will be able to start to create threat models, and think critically about the threat models created by other people. You will be able to apply the STRIDE Method to your threat model and distinguish the trust boundaries in a given system. You will also gain a basic understanding of applied cryptography, such as encryption and secure hashing.
Cryptography Basics: Symmetric and Asymmetric Cryptography - Identifying Security Vulnerabilities
Copyright Disclaimer under Section 107 of the copyright act 1976, allowance is made for fair use for purposes such as criticism, comment, news reporting, scholarship, and research. Fair use is a use permitted by copyright statute that might otherwise be infringing. Non-profit, educational or personal use tips the balance in favour of fair use.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
25
Duration
5:35
Published
Nov 7, 2020
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.