Cryptography 101: Hashing, Encoding & Encryption Explained 🔐
Dive into Lecture 2 of our cryptography course to understand hashing, encoding, and both symmetric and asymmetric encryption. Access virtual labs, quizzes, and challenges to boost your skills!

Level Effect
382 views • Oct 16, 2023
About this video
1️⃣ Gain access to the virtual machines, quizzes, and challenges by accessing the course here: https://training.leveleffect.com
2️⃣ Check out the syllabus for all three Fundamentals courses here including the CDA Program they are pre-requisites for: https://docs.google.com/spreadsheets/d/1QJb5mMOe_DIcXujxo1nBf9o0Pcl_AhLA7PH8hlgGwxk/edit#gid=1747231724
3️⃣ For more information check out our CDA Program in depth: https://www.leveleffect.com/cyber-defense-analyst
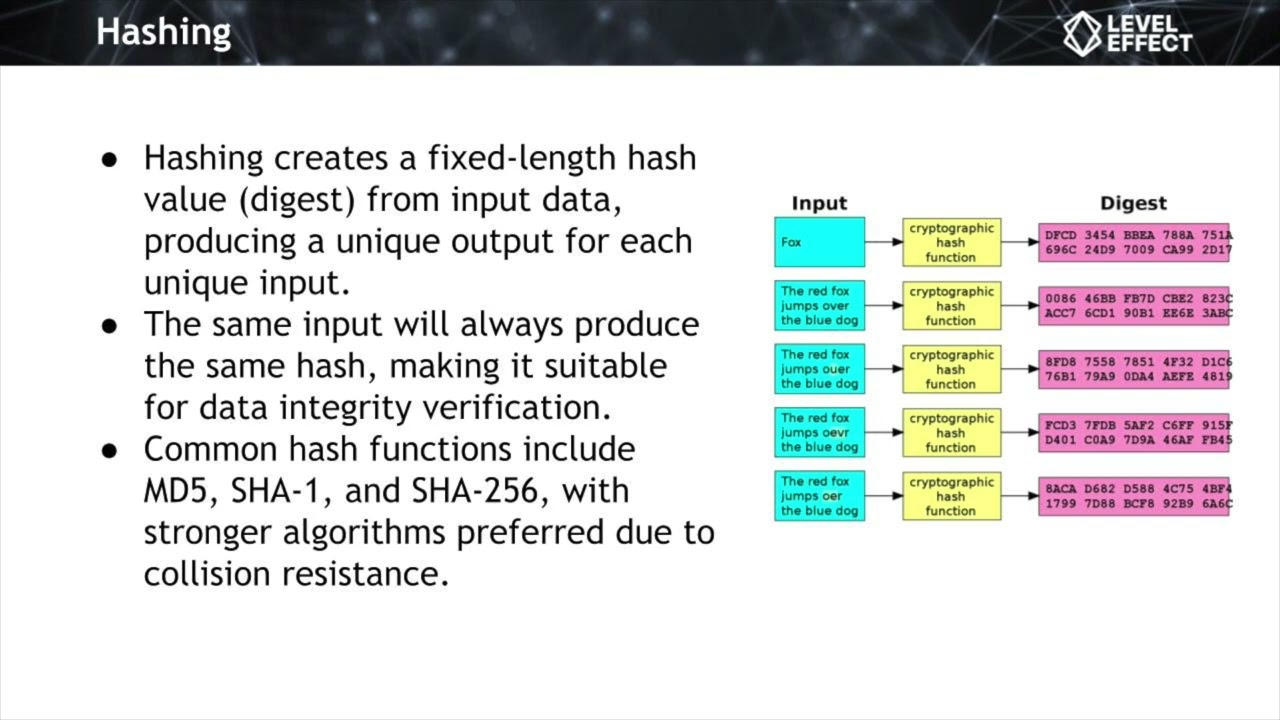
Learn the vital concepts of cryptographic hashing and encoding to ensure data integrity and secure data representation. Understand the inner workings of symmetric encryption algorithms and how they safeguard data confidentiality. Dive into the principles of asymmetric encryption, including the use of public and private key pairs. Acquire essential skills in deploying digital signatures for authentication and non-repudiation.
#datasecurity #encryption #techskills #cybersecurity #cybersecuritytrainingforbeginners #cryptography #digitalsignatures
2️⃣ Check out the syllabus for all three Fundamentals courses here including the CDA Program they are pre-requisites for: https://docs.google.com/spreadsheets/d/1QJb5mMOe_DIcXujxo1nBf9o0Pcl_AhLA7PH8hlgGwxk/edit#gid=1747231724
3️⃣ For more information check out our CDA Program in depth: https://www.leveleffect.com/cyber-defense-analyst
Learn the vital concepts of cryptographic hashing and encoding to ensure data integrity and secure data representation. Understand the inner workings of symmetric encryption algorithms and how they safeguard data confidentiality. Dive into the principles of asymmetric encryption, including the use of public and private key pairs. Acquire essential skills in deploying digital signatures for authentication and non-repudiation.
#datasecurity #encryption #techskills #cybersecurity #cybersecuritytrainingforbeginners #cryptography #digitalsignatures
Video Information
Views
382
Likes
6
Duration
11:16
Published
Oct 16, 2023
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now