Cryptographic Hash Functions Explained 🔐 | Blockchain Tutorial Series
Discover the fundamentals of cryptographic hash functions and their role in blockchain technology. Perfect for beginners looking to understand blockchain security in this comprehensive tutorial series.

FAME WORLD EDUCATIONAL HUB
83 views • Aug 28, 2023
About this video
Cryptographic Hash Function | Blockchian Tutorial Series @FAMEWORLDEDUCATIONALHUB
Key Highlights:
00:00 - introduction
00:10 - channel intro
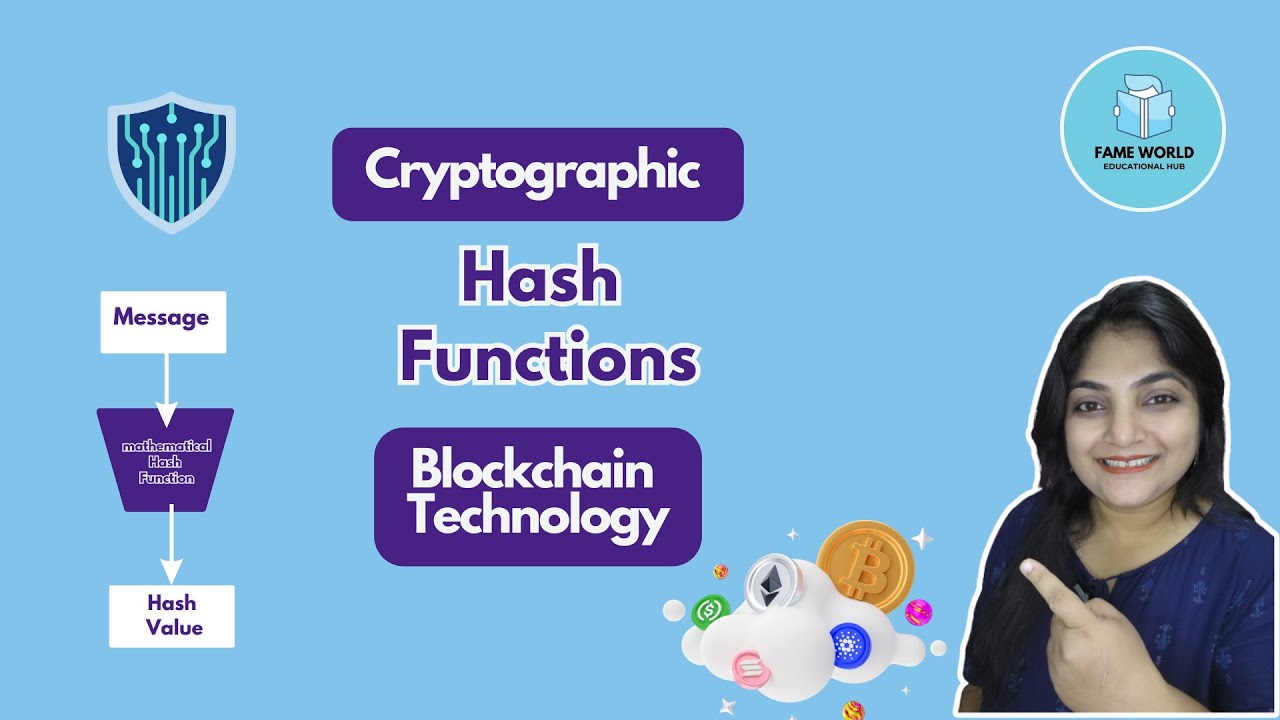
00:18 - cryptographic hash functions
00:47 - how cryptographic hash functions work
01:19 hash functions add security features
01:22 - properties
01:27 - collision free
01:35 - hidden
01:43 - puzzle friendly
01:56 - Conclusion
Title: Demystifying Cryptographic Hash Functions: Security Essentials Explained
Description: 🔒 Dive into the world of cryptographic hash functions with our comprehensive guide! 🚀 Whether you're a cybersecurity enthusiast, a developer, or simply curious about digital security, this video is your gateway to understanding the fundamental concepts of cryptographic hash functions.
🔐 What exactly is a cryptographic hash function? How does it work? Why is it crucial for data integrity and security in the digital realm? In this illuminating video, we break down the complex concepts into easy-to-understand explanations, providing you with a solid foundation to grasp the significance of hash functions in modern technology.
Key Highlights:
- 🌐 Understanding the role of hash functions in cybersecurity and data protection.
- 🔄 How hash functions convert variable-length input into fixed-length hash values.
- 🔍 Exploring the one-way nature of hash functions and its importance in password storage.
- ✅ Verifying data integrity through hash values and digital signatures.
- 🛡️ Protection against tampering and unauthorized changes using hash functions.
- 💡 Real-world applications: blockchain, digital forensics, secure communications, and more.
Whether you're aiming to enhance your technical knowledge or just seeking a clear explanation of cryptographic hash functions, this video has you covered. Join us in unraveling the mysteries behind these essential tools that underpin modern cybersecurity. Don't miss out – hit the play button and level up your security awareness today!
🔗 Additional Tags: Cryptography, Hash Functions Explained, Data Security, Cybersecurity Basics, Digital Signatures, Encryption, Information Protection, Technology Explained.
👍 If you found this video helpful or intriguing, don't forget to give it a thumbs up, share it with your fellow digital explorers, and subscribe to our channel for more insightful content on technology and security! 📡🔒
Key Highlights:
00:00 - introduction
00:10 - channel intro
00:18 - cryptographic hash functions
00:47 - how cryptographic hash functions work
01:19 hash functions add security features
01:22 - properties
01:27 - collision free
01:35 - hidden
01:43 - puzzle friendly
01:56 - Conclusion
Title: Demystifying Cryptographic Hash Functions: Security Essentials Explained
Description: 🔒 Dive into the world of cryptographic hash functions with our comprehensive guide! 🚀 Whether you're a cybersecurity enthusiast, a developer, or simply curious about digital security, this video is your gateway to understanding the fundamental concepts of cryptographic hash functions.
🔐 What exactly is a cryptographic hash function? How does it work? Why is it crucial for data integrity and security in the digital realm? In this illuminating video, we break down the complex concepts into easy-to-understand explanations, providing you with a solid foundation to grasp the significance of hash functions in modern technology.
Key Highlights:
- 🌐 Understanding the role of hash functions in cybersecurity and data protection.
- 🔄 How hash functions convert variable-length input into fixed-length hash values.
- 🔍 Exploring the one-way nature of hash functions and its importance in password storage.
- ✅ Verifying data integrity through hash values and digital signatures.
- 🛡️ Protection against tampering and unauthorized changes using hash functions.
- 💡 Real-world applications: blockchain, digital forensics, secure communications, and more.
Whether you're aiming to enhance your technical knowledge or just seeking a clear explanation of cryptographic hash functions, this video has you covered. Join us in unraveling the mysteries behind these essential tools that underpin modern cybersecurity. Don't miss out – hit the play button and level up your security awareness today!
🔗 Additional Tags: Cryptography, Hash Functions Explained, Data Security, Cybersecurity Basics, Digital Signatures, Encryption, Information Protection, Technology Explained.
👍 If you found this video helpful or intriguing, don't forget to give it a thumbs up, share it with your fellow digital explorers, and subscribe to our channel for more insightful content on technology and security! 📡🔒
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
83
Likes
1
Duration
2:23
Published
Aug 28, 2023