Criptografia e Segurança de Rede Unidade 1 - Parte 5: Modelos de Segurança de Rede
Discussão sobre modelos de segurança em redes.

TN55 RLE
442 views • Aug 8, 2020
About this video
In this video, I have discussed about model of network security and model of network access security.
Explanation or Description
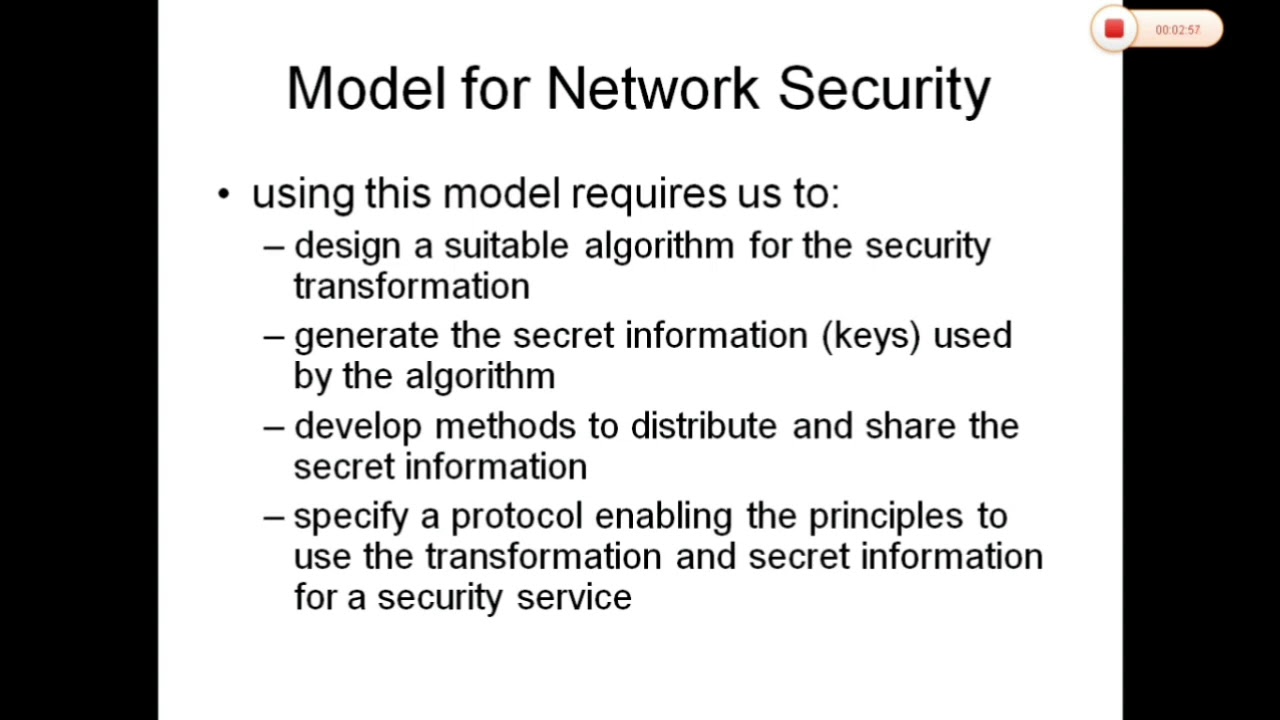
In considering the place of encryption, its useful to use the following two models. The first models information flowing over an insecure communications channel, in the presence of possible opponents. Hence an appropriate security transform (encryption algorithm) can be used, with suitable keys, possibly negotiated using the presence of a trusted third party.
The second model is concerned with controlled access to information or resources on a computer system, in the presence of possible opponents. Here appropriate controls are needed on the access and within the system, to provide suitable security. Some cryptographic techniques are useful here also.
Trusted system can also be seen as level base security system where protection is provided and handled according to different levels.
Follow on Instagram - https://www.instagram.com/the_kanagu/
Follow on Facebook - https://www.facebook.com/kanagaraj.narayanasamy (if you are need to be added as friend then send me as short message about you and send the request- thank you!)
Subscribe our channel - https://www.facebook.com/kanagaraj.narayanasamy
Explanation or Description
In considering the place of encryption, its useful to use the following two models. The first models information flowing over an insecure communications channel, in the presence of possible opponents. Hence an appropriate security transform (encryption algorithm) can be used, with suitable keys, possibly negotiated using the presence of a trusted third party.
The second model is concerned with controlled access to information or resources on a computer system, in the presence of possible opponents. Here appropriate controls are needed on the access and within the system, to provide suitable security. Some cryptographic techniques are useful here also.
Trusted system can also be seen as level base security system where protection is provided and handled according to different levels.
Follow on Instagram - https://www.instagram.com/the_kanagu/
Follow on Facebook - https://www.facebook.com/kanagaraj.narayanasamy (if you are need to be added as friend then send me as short message about you and send the request- thank you!)
Subscribe our channel - https://www.facebook.com/kanagaraj.narayanasamy
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
442
Likes
18
Duration
8:25
Published
Aug 8, 2020
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now