Comprehensive Network Security Syllabus: OSI Model, Cryptography & Defense Strategies 🔐
Explore essential concepts in network security, including OSI model layers, security principles, common attacks, and cryptography techniques to protect your network effectively.

My Education
4 views • May 21, 2023
About this video
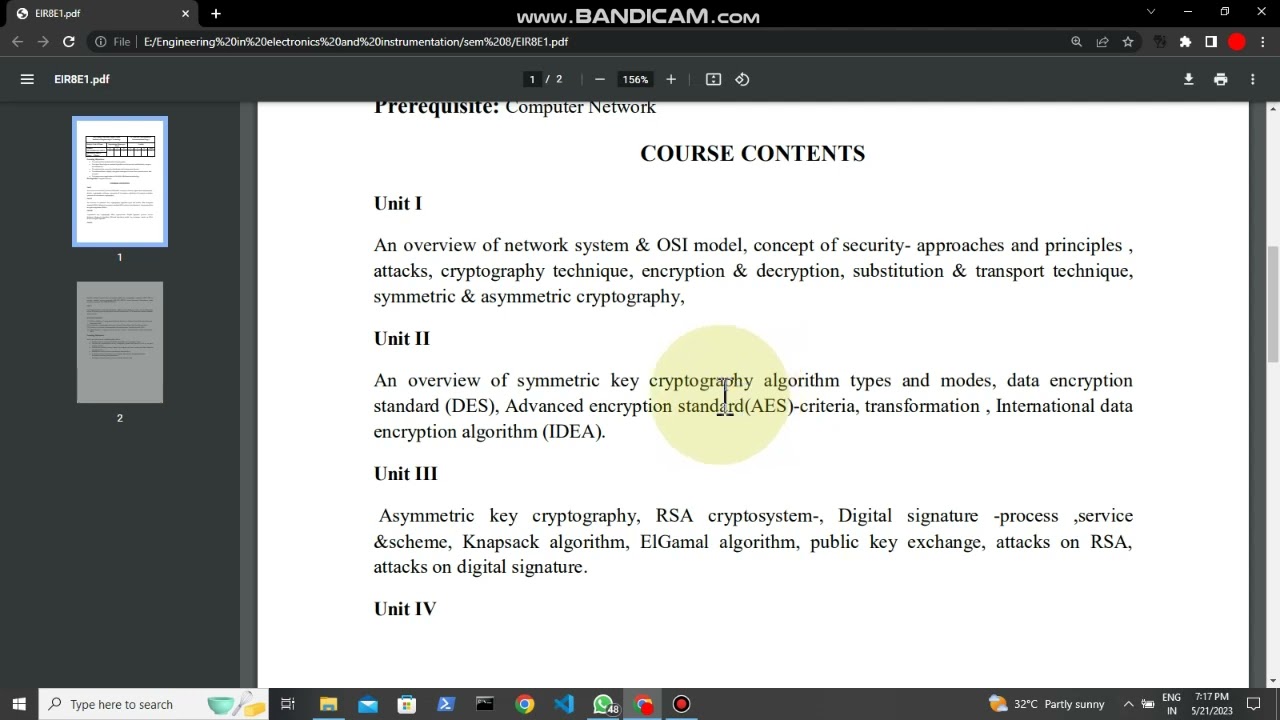
An overview of network system
OSI model
concept of security
approaches and principles
attacks
cryptography technique
encryption
decryption
substitution
transport technique
symmetric cryptography
asymmetric cryptography,
An overview of symmetric key cryptography
cryptography algorithm types
cryptography modes
data encryption standard (DES)
Advanced encryption standard(AES)
AES criteria
AES transformation
International data encryption algorithm (IDEA).
Asymmetric key cryptography
RSA cryptosystem
Digital signature process
Digital signature service
Digital signature scheme
Knapsack algorithm
ElGamal algorithm
public key exchange
attacks on RSA,
attacks on digital signature.
Digital certificates
private key management
public key cryptography standards
XML
PKI
security
internet security protocols
SSL
TSL
SHTTP
secure electronic Transaction
email security
security in 3G
security in GSM
IEEE802.11
User authentication mechanism
Biometric authentication
Kerberos
Password
Authentication tokens
IP security overview & policy
Firewall characteristic
VPN
Malicious software
Intruder
Email security.
OSI model
concept of security
approaches and principles
attacks
cryptography technique
encryption
decryption
substitution
transport technique
symmetric cryptography
asymmetric cryptography,
An overview of symmetric key cryptography
cryptography algorithm types
cryptography modes
data encryption standard (DES)
Advanced encryption standard(AES)
AES criteria
AES transformation
International data encryption algorithm (IDEA).
Asymmetric key cryptography
RSA cryptosystem
Digital signature process
Digital signature service
Digital signature scheme
Knapsack algorithm
ElGamal algorithm
public key exchange
attacks on RSA,
attacks on digital signature.
Digital certificates
private key management
public key cryptography standards
XML
PKI
security
internet security protocols
SSL
TSL
SHTTP
secure electronic Transaction
email security
security in 3G
security in GSM
IEEE802.11
User authentication mechanism
Biometric authentication
Kerberos
Password
Authentication tokens
IP security overview & policy
Firewall characteristic
VPN
Malicious software
Intruder
Email security.
Video Information
Views
4
Duration
3:09
Published
May 21, 2023
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.