Comprehensive Guide to Cryptographic Attacks & Testing Methods 🔐
Explore key cryptographic attack techniques including Kasiski Examination for private keys, Common Modulus Attack for public keys, and Pollard's rho for primality testing. Boost your cybersecurity knowledge today!
Shreya Gupta
8 views • Mar 30, 2024
About this video
Cryptographic Attack Analysis
1. Private Key: Kasiski Examination
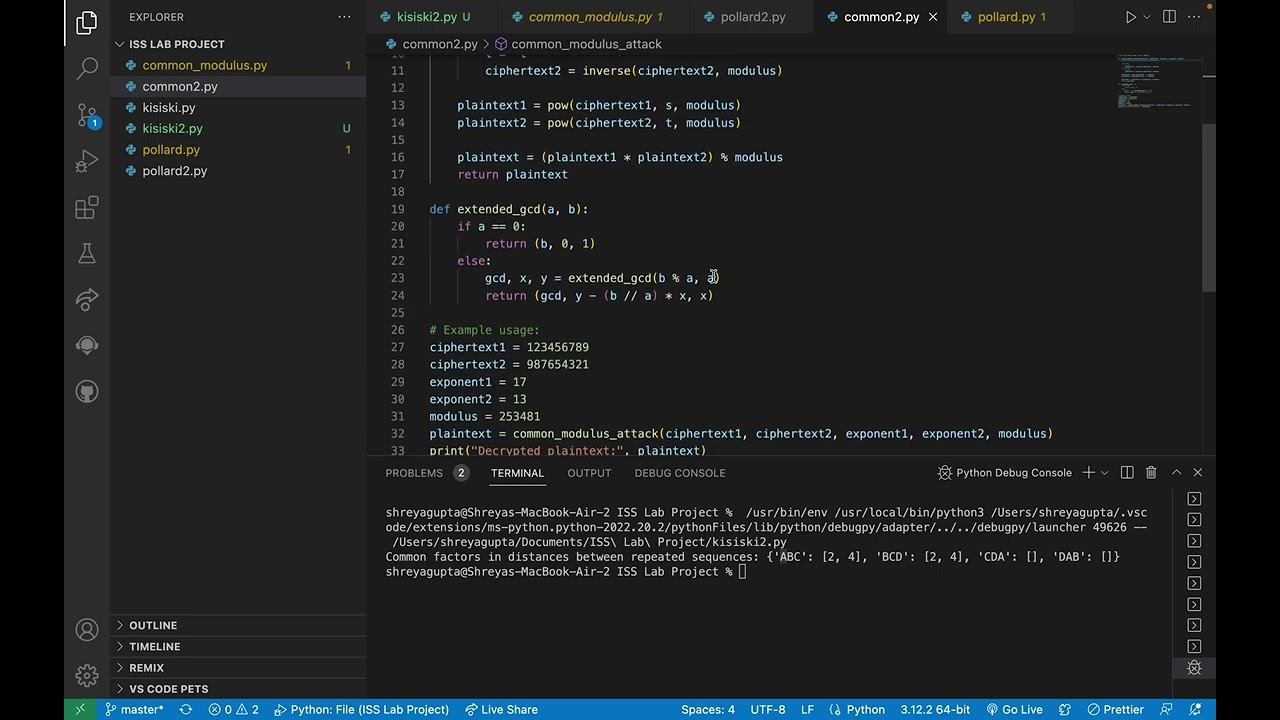
2. Public Key: Common Modulus Attack:
3. Primality Testing: Pollard's rho Algorithm for Factorization
1. Private Key: Kasiski Examination
2. Public Key: Common Modulus Attack:
3. Primality Testing: Pollard's rho Algorithm for Factorization
Video Information
Views
8
Duration
8:14
Published
Mar 30, 2024
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.