Complete Guide to Encryption & Decryption: Understand Cryptanalysis with Notes 🔐
Learn the fundamentals of encryption and decryption, along with detailed notes on cryptanalysis. Perfect for beginners and students seeking a clear explanation!

sawji gyaan
73 views • Jun 1, 2024
About this video
hello dosto mera naam hai suraj kumar or aapka sawagat sawji gyan channel mein
### Encryption
- **Definition**: Encryption is the process of converting plaintext (readable data) into ciphertext (unreadable data) using an algorithm and a key.
- **Purpose**: To protect the confidentiality of data by making it unreadable to unauthorized users.
- **Types**:
- **Symmetric Encryption**: Uses the same key for both encryption and decryption (e.g., AES, DES).
- **Asymmetric Encryption**: Uses a pair of keys – a public key for encryption and a private key for decryption (e.g., RSA, ECC).
- **Process**:
1. **Plaintext**: Original readable data.
2. **Encryption Algorithm**: The method used to transform the plaintext.
3. **Key**: A value used by the algorithm to encrypt the data.
4. **Ciphertext**: Encrypted data.
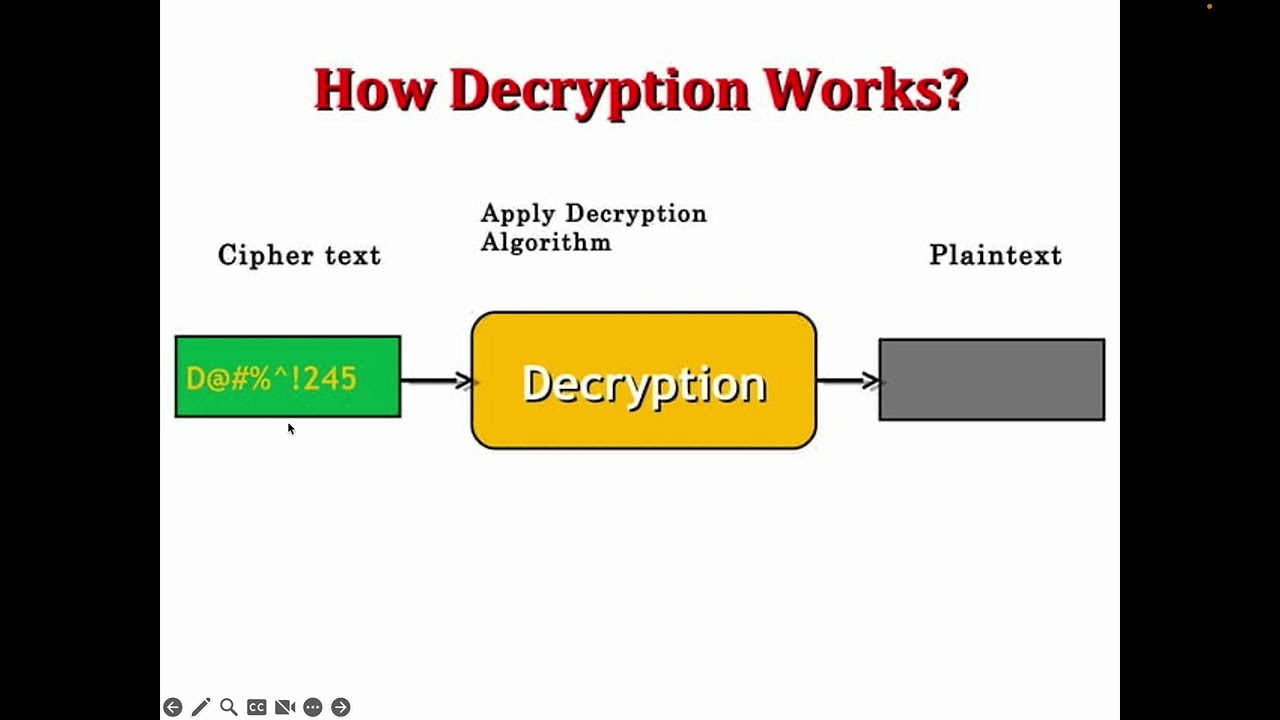
### Decryption
- **Definition**: Decryption is the process of converting ciphertext back into plaintext using an algorithm and a key.
- **Purpose**: To restore the original readable data from its encrypted form.
- **Process**:
1. **Ciphertext**: Encrypted data.
2. **Decryption Algorithm**: The method used to transform the ciphertext back into plaintext.
3. **Key**: A value used by the algorithm to decrypt the data.
4. **Plaintext**: Original readable data restored.
### Cryptanalysis
- **Definition**: Cryptanalysis is the study and practice of analyzing information systems to understand hidden aspects of the systems.
- **Purpose**: To find weaknesses or vulnerabilities in cryptographic algorithms and protocols, potentially allowing for the breaking of encryption.
- **Methods**:
- **Brute Force Attack**: Trying all possible keys until the correct one is found.
- **Ciphertext-only Attack**: The attacker has only ciphertext and tries to deduce the plaintext or key.
- **Known-plaintext Attack**: The attacker has access to both plaintext and its corresponding ciphertext.
- **Chosen-plaintext Attack**: The attacker can encrypt plaintexts of their choice to study the ciphertext.
- **Chosen-ciphertext Attack**: The attacker can decrypt ciphertexts of their choice to study the plaintext.
- **Side-channel Attack**: Exploiting physical implementations (e.g., timing information, power consumption) rather than theoretical weaknesses.
- **Objectives**:
- **Breaking Encryption**: Successfully decrypting ciphertext without access to the key.
- **Finding Weaknesses**: Identifying flaws in cryptographic algorithms or protocols.
- **Improving Security**: Enhancing cryptographic methods by addressing identified weaknesses.
### Summary
- **Encryption**: Protects data by converting it into an unreadable format using algorithms and keys.
- **Decryption**: Restores encrypted data to its original readable format using algorithms and keys.
- **Cryptanalysis**: Analyzes and attempts to break encryption methods to find weaknesses and improve security.
### Encryption
- **Definition**: Encryption is the process of converting plaintext (readable data) into ciphertext (unreadable data) using an algorithm and a key.
- **Purpose**: To protect the confidentiality of data by making it unreadable to unauthorized users.
- **Types**:
- **Symmetric Encryption**: Uses the same key for both encryption and decryption (e.g., AES, DES).
- **Asymmetric Encryption**: Uses a pair of keys – a public key for encryption and a private key for decryption (e.g., RSA, ECC).
- **Process**:
1. **Plaintext**: Original readable data.
2. **Encryption Algorithm**: The method used to transform the plaintext.
3. **Key**: A value used by the algorithm to encrypt the data.
4. **Ciphertext**: Encrypted data.
### Decryption
- **Definition**: Decryption is the process of converting ciphertext back into plaintext using an algorithm and a key.
- **Purpose**: To restore the original readable data from its encrypted form.
- **Process**:
1. **Ciphertext**: Encrypted data.
2. **Decryption Algorithm**: The method used to transform the ciphertext back into plaintext.
3. **Key**: A value used by the algorithm to decrypt the data.
4. **Plaintext**: Original readable data restored.
### Cryptanalysis
- **Definition**: Cryptanalysis is the study and practice of analyzing information systems to understand hidden aspects of the systems.
- **Purpose**: To find weaknesses or vulnerabilities in cryptographic algorithms and protocols, potentially allowing for the breaking of encryption.
- **Methods**:
- **Brute Force Attack**: Trying all possible keys until the correct one is found.
- **Ciphertext-only Attack**: The attacker has only ciphertext and tries to deduce the plaintext or key.
- **Known-plaintext Attack**: The attacker has access to both plaintext and its corresponding ciphertext.
- **Chosen-plaintext Attack**: The attacker can encrypt plaintexts of their choice to study the ciphertext.
- **Chosen-ciphertext Attack**: The attacker can decrypt ciphertexts of their choice to study the plaintext.
- **Side-channel Attack**: Exploiting physical implementations (e.g., timing information, power consumption) rather than theoretical weaknesses.
- **Objectives**:
- **Breaking Encryption**: Successfully decrypting ciphertext without access to the key.
- **Finding Weaknesses**: Identifying flaws in cryptographic algorithms or protocols.
- **Improving Security**: Enhancing cryptographic methods by addressing identified weaknesses.
### Summary
- **Encryption**: Protects data by converting it into an unreadable format using algorithms and keys.
- **Decryption**: Restores encrypted data to its original readable format using algorithms and keys.
- **Cryptanalysis**: Analyzes and attempts to break encryption methods to find weaknesses and improve security.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
73
Likes
1
Duration
10:12
Published
Jun 1, 2024
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.