Comparative Analysis of Cryptographic Algorithms for Different File Formats
This study explores various cryptographic algorithms and their effectiveness in securing different file formats. Authored by M. Meena and A. Komathi, the paper delves into the techniques used to protect message content from unauthorized access.

International Journal of Science and Research (IJSR)
218 views • Nov 28, 2021
About this video
Authors: M. Meena, A. Komathi
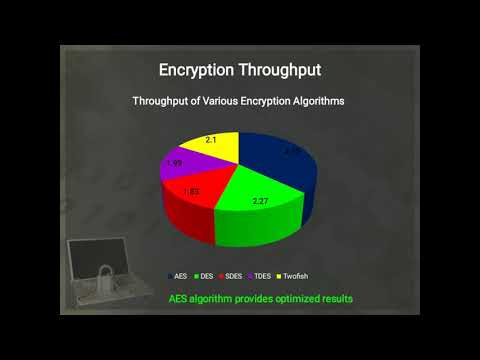
Abstract: #Cryptography #algorithm is the technique used for concealing the content of a message from all users except the sender and the receiver and to authenticate the correctness of the message to the recipient. Information #security could be implemented with many known security algorithms. The most common of these are encryption algorithms. This paper provides a fair comparison between the five most common symmetric key cryptography algorithms #DES, #SDES, #TripleDES, #AES, and #TwoFish. Since the main concern here is the performance of algorithms under different settings, the presented comparison takes into consideration the behavior and the performance of the algorithm when different data loads are used. The comparison is made on the basis of encryption, decryption, and throughput time with the variation of various file features like different data types, data sizes, and key sizes.
Keywords: Cryptography, #Symmetric, #Encryption, #Decryption, #Throughput, Data size
URL: https://www.ijsr.net/get_abstract.php?paper_id=ART2016990
Abstract: #Cryptography #algorithm is the technique used for concealing the content of a message from all users except the sender and the receiver and to authenticate the correctness of the message to the recipient. Information #security could be implemented with many known security algorithms. The most common of these are encryption algorithms. This paper provides a fair comparison between the five most common symmetric key cryptography algorithms #DES, #SDES, #TripleDES, #AES, and #TwoFish. Since the main concern here is the performance of algorithms under different settings, the presented comparison takes into consideration the behavior and the performance of the algorithm when different data loads are used. The comparison is made on the basis of encryption, decryption, and throughput time with the variation of various file features like different data types, data sizes, and key sizes.
Keywords: Cryptography, #Symmetric, #Encryption, #Decryption, #Throughput, Data size
URL: https://www.ijsr.net/get_abstract.php?paper_id=ART2016990
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
218
Likes
2
Duration
6:34
Published
Nov 28, 2021
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.