CMAC Explained: How Cipher-Based Authentication Secures Your Data 🔐
Discover the fundamentals of CMAC, a vital cryptographic protocol that ensures data integrity and authenticity. Perfect for beginners and security enthusiasts alike!

Network Technician
6 views • Oct 25, 2025
About this video
Delve into the core principles of modern cryptography with this comprehensive presentation on the CMAC (Cipher-based Message Authentication Code) protocol. This presentation breaks down how CMAC provides the essential security guarantees of data integrity and authenticity, ensuring that digital messages are safe from tampering and come from a trusted source.
Whether you're a cybersecurity student, a network engineer, or a developer, this guide offers a clear and detailed walkthrough of this important algorithm.
In this presentation, you will learn:
The Fundamentals: Understand what a Message Authentication Code (MAC) is and the critical role it plays in secure communications.
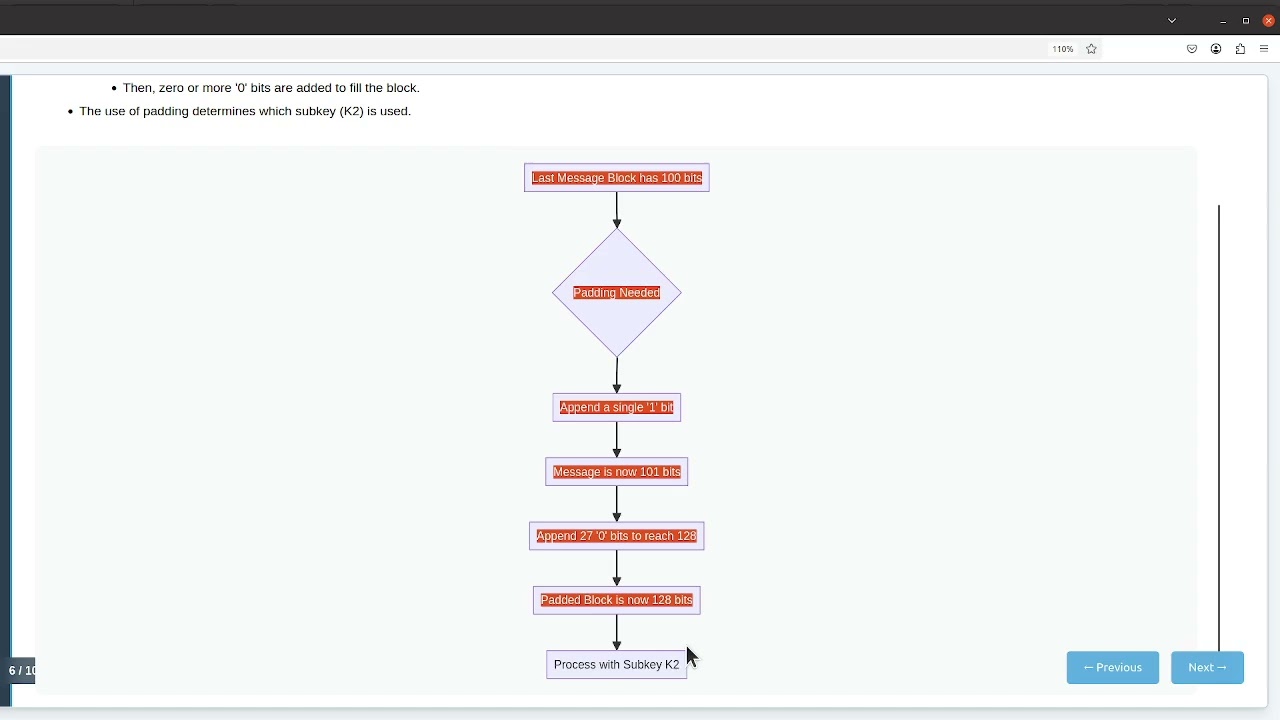
The Inner Workings of CMAC: Explore the step-by-step process, including its reliance on block ciphers like AES, the CBC-like chaining mechanism, and the crucial subkey generation that underpins its security.
CMAC vs. HMAC: Get a clear comparison between the two leading MAC algorithms to understand their different strengths and use cases.
Real-World Applications: Discover where CMAC is used every day, from securing your Wi-Fi and Bluetooth connections to authenticating financial transactions.
Key Advantages: Learn why CMAC is a highly efficient, secure, and standardized choice for resource-constrained environments like IoT and embedded systems.
Whether you're a cybersecurity student, a network engineer, or a developer, this guide offers a clear and detailed walkthrough of this important algorithm.
In this presentation, you will learn:
The Fundamentals: Understand what a Message Authentication Code (MAC) is and the critical role it plays in secure communications.
The Inner Workings of CMAC: Explore the step-by-step process, including its reliance on block ciphers like AES, the CBC-like chaining mechanism, and the crucial subkey generation that underpins its security.
CMAC vs. HMAC: Get a clear comparison between the two leading MAC algorithms to understand their different strengths and use cases.
Real-World Applications: Discover where CMAC is used every day, from securing your Wi-Fi and Bluetooth connections to authenticating financial transactions.
Key Advantages: Learn why CMAC is a highly efficient, secure, and standardized choice for resource-constrained environments like IoT and embedded systems.
Video Information
Views
6
Duration
12:56
Published
Oct 25, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.
Trending Now