Breaking PrintCIPHER: A Cryptanalysis Breakthrough 🔓
Discover how researchers from DTU uncovered vulnerabilities in PrintCIPHER, revealing critical insights into its security. Learn about the latest cryptanalysis techniques and their implications for cryptographic security.

IACR
838 views • Oct 10, 2011
About this video
Gregor Leander, Mohamed Ahmed Abdelraheem, Hoda AlKhzaimi, and Erik Zenner
Technical University of Denmark, Lyngby, Denmark
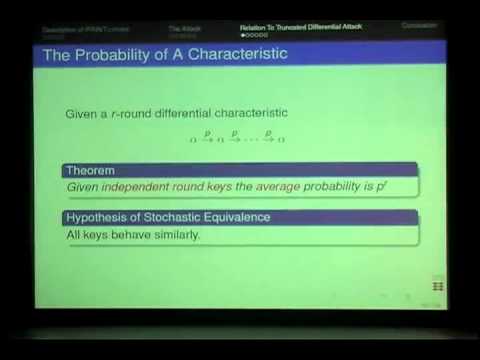
Abstract. At CHES 2010, the new block cipher PRINTcipher was presented as a light-weight encryption solution for printable circuits [15]. The best attack to date is a differential attack [1] that breaks less than half of the rounds. In this paper, we will present a new attack called invariant subspace attack that breaks the full cipher for a significant fraction of its keys. This attack can be seen as a weak-key variant of a statistical saturation attack. For such weak keys, a chosen plaintext distinguishing attack can be mounted in unit time. In addition to breaking PRINTcipher, the new attack also gives us new insights into other, more well-established attacks. We derive a truncated differential characteristic with a round-independent but highly key-dependent probability. In addition, we also show that for weak keys, strongly biased linear approximations exists for any number of rounds. In this sense, PRINTcipher behaves very differently to what is usually -- often implicitly -- assumed.
Technical University of Denmark, Lyngby, Denmark
Abstract. At CHES 2010, the new block cipher PRINTcipher was presented as a light-weight encryption solution for printable circuits [15]. The best attack to date is a differential attack [1] that breaks less than half of the rounds. In this paper, we will present a new attack called invariant subspace attack that breaks the full cipher for a significant fraction of its keys. This attack can be seen as a weak-key variant of a statistical saturation attack. For such weak keys, a chosen plaintext distinguishing attack can be mounted in unit time. In addition to breaking PRINTcipher, the new attack also gives us new insights into other, more well-established attacks. We derive a truncated differential characteristic with a round-independent but highly key-dependent probability. In addition, we also show that for weak keys, strongly biased linear approximations exists for any number of rounds. In this sense, PRINTcipher behaves very differently to what is usually -- often implicitly -- assumed.
Video Information
Views
838
Likes
3
Duration
17:39
Published
Oct 10, 2011