BlueHat IL 2017: Debunking Myths & Facts About Securing Data-In-Use in the Cloud 🔐
Explore key insights from Prof. Yehuda Lindell at BlueHat IL 2017 on how to effectively protect data during processing in the cloud, and separate myths from facts for safer cloud adoption.
Microsoft Israel R&D Center
445 views • Feb 6, 2017
About this video
Securing Data-In-Use in the Cloud - Myths and Facts
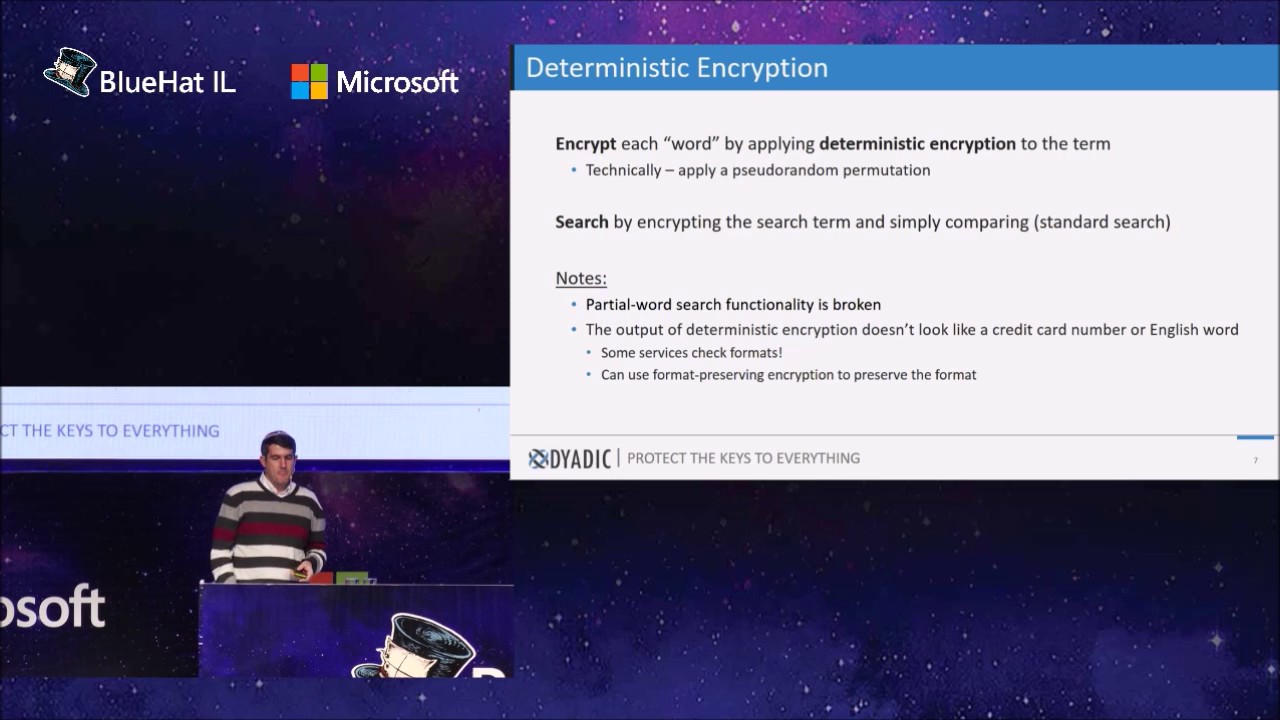
One of the greatest challenges facing companies who wish to move to the cloud is the potential theft of confidential and private data. There exist strong encryption solutions that enable the protection of data at rest, but they are actually more problematic than they look (in many of the offered solutions, you do not own your key). In addition, the power of the cloud is in data processing and this leaves data unprotected and vulnerable. There has therefore been much interest in new format-preserving and order-preserving encryption schemes that enable a cloud service to process data without ever decrypting it. At first sight, this solves the problem since the data always remains encrypted, and the cloud provider is never given the decryption key.
In this presentation, we will discuss the problems that arise when attempting to encrypt in the cloud. We will begin by discussing why key ownership is a big issue and problem, and what other alternatives exist. Next, we will show that format and order preserving encryption methods provide a very low level of security. We will describe concrete attacks on realistic use cases for these methods. Finally, we will propose a new paradigm for solving the problem of protecting data in use based on secure multiparty computation. This is a technology which has only recently become practical and can now be used to compute on data without ever revealing it. We will describe how multiparty computation techniques (combined with other advanced cryptographic methods) can be used to process data in the cloud without ever revealing it.
New technologies and solutions for processing encrypted data are appearing now in products and there is much interest in adopting them. In this talk, we will demystify these solutions and provide a deep understanding that is necessary for analyzing their security. Attacks will be presented that show that strong security claims often attributed to some solutions do not hold up.
One of the greatest challenges facing companies who wish to move to the cloud is the potential theft of confidential and private data. There exist strong encryption solutions that enable the protection of data at rest, but they are actually more problematic than they look (in many of the offered solutions, you do not own your key). In addition, the power of the cloud is in data processing and this leaves data unprotected and vulnerable. There has therefore been much interest in new format-preserving and order-preserving encryption schemes that enable a cloud service to process data without ever decrypting it. At first sight, this solves the problem since the data always remains encrypted, and the cloud provider is never given the decryption key.
In this presentation, we will discuss the problems that arise when attempting to encrypt in the cloud. We will begin by discussing why key ownership is a big issue and problem, and what other alternatives exist. Next, we will show that format and order preserving encryption methods provide a very low level of security. We will describe concrete attacks on realistic use cases for these methods. Finally, we will propose a new paradigm for solving the problem of protecting data in use based on secure multiparty computation. This is a technology which has only recently become practical and can now be used to compute on data without ever revealing it. We will describe how multiparty computation techniques (combined with other advanced cryptographic methods) can be used to process data in the cloud without ever revealing it.
New technologies and solutions for processing encrypted data are appearing now in products and there is much interest in adopting them. In this talk, we will demystify these solutions and provide a deep understanding that is necessary for analyzing their security. Attacks will be presented that show that strong security claims often attributed to some solutions do not hold up.
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
445
Likes
4
Duration
44:24
Published
Feb 6, 2017
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.