Understanding Authentication & Public Key Cryptography 🔐 (ITS335 Lecture 5, 2013)
Explore MACs, hash functions, and the fundamentals of public key cryptography in this comprehensive lecture from ITS335 IT Security. Perfect for strengthening your cybersecurity knowledge!
Steven Gordon
1.3K views • Nov 26, 2013

About this video
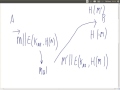
MAC and hash functions for authentication; Introduction to public key cryptography. Lecture 5 of ITS335 IT Security at Sirindhorn International Institute of Technology, Thammasat University. Given on 26 November 2013 at Bangkadi, Pathumthani, Thailand by Steven Gordon. Course material via: http://sandilands.info/sgordon/teaching
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
1.3K
Likes
4
Duration
01:18:04
Published
Nov 26, 2013
User Reviews
3.9
(1) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.