ARP Spoofing Explained: Protect Your Network from Hidden Threats 🔒
Discover how ARP Spoofing can compromise your network security, learn to identify the signs, and explore effective methods to prevent this cyber threat.

Ekeeda
98 views • Jul 21, 2023
About this video
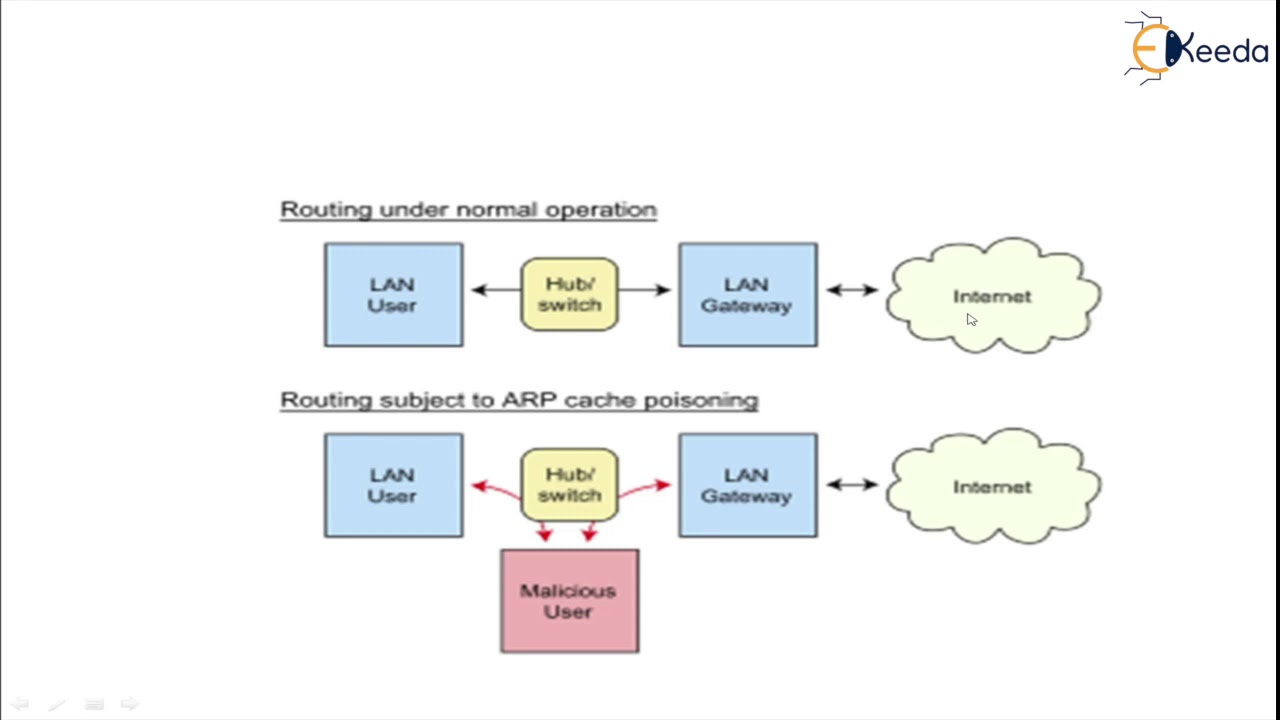
Join us as we uncover the potential threats posed by Address Resolution Protocol (ARP) Spoofing, understand how it compromises network security, and learn essential strategies to protect your systems against this malicious technique.
🚀 Key Topics Explored:
🔒 Understanding ARP Spoofing Attacks
🔑 Implications for Network Security
💡 Strategies for Detection and Prevention
🌐 Real-world Examples and Case Studies
🔗 Best Practices for Enhancing System Security
👉 Download Ekeeda Application & Learn from the best professors with 10+ years of experience.
Subscribe to a Course or Start a Free Trial of Package.
✤ Download the Ekeeda - Learning App for Engineering Courses App here:
➤ Android & iOS: https://ekeeda.com/download.html
Access the Complete Playlist of Subject GATE Algorithms - https://www.youtube.com/playlist?list=PLO4TWepMw7ggN22wYVdfE7KmOcMjNHh4m
✤ For More Such Classes Get Subscription Advantage:
👉 GATE Algorithms (GATE Computer Science and Information Technology): https://ekeeda.com/gate/gate-computer-science-and-information-technology/algorithms
👉 GATE Computer Science and Information Technology: https://ekeeda.com/gate/gate-computer-science-and-information-technology
👉 Explore our Courses - https://ekeeda.com/catalog
Like us on Facebook: https://www.facebook.com/Ekeeda
Follow us on Instagram: https://www.instagram.com/ekeeda_official/
Follow us on Twitter: https://twitter.com/ekeeda_official
Follow us on LinkedIn: https://www.linkedin.com/company/ekeeda.com
Visit Our Website: https://ekeeda.com/
Subscribe to Ekeeda Channel to access more videos: https://www.youtube.com/c/Ekeeda?sub_confirmation=1
🚀 Key Topics Explored:
🔒 Understanding ARP Spoofing Attacks
🔑 Implications for Network Security
💡 Strategies for Detection and Prevention
🌐 Real-world Examples and Case Studies
🔗 Best Practices for Enhancing System Security
👉 Download Ekeeda Application & Learn from the best professors with 10+ years of experience.
Subscribe to a Course or Start a Free Trial of Package.
✤ Download the Ekeeda - Learning App for Engineering Courses App here:
➤ Android & iOS: https://ekeeda.com/download.html
Access the Complete Playlist of Subject GATE Algorithms - https://www.youtube.com/playlist?list=PLO4TWepMw7ggN22wYVdfE7KmOcMjNHh4m
✤ For More Such Classes Get Subscription Advantage:
👉 GATE Algorithms (GATE Computer Science and Information Technology): https://ekeeda.com/gate/gate-computer-science-and-information-technology/algorithms
👉 GATE Computer Science and Information Technology: https://ekeeda.com/gate/gate-computer-science-and-information-technology
👉 Explore our Courses - https://ekeeda.com/catalog
Like us on Facebook: https://www.facebook.com/Ekeeda
Follow us on Instagram: https://www.instagram.com/ekeeda_official/
Follow us on Twitter: https://twitter.com/ekeeda_official
Follow us on LinkedIn: https://www.linkedin.com/company/ekeeda.com
Visit Our Website: https://ekeeda.com/
Subscribe to Ekeeda Channel to access more videos: https://www.youtube.com/c/Ekeeda?sub_confirmation=1
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
98
Duration
2:08
Published
Jul 21, 2023
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.