Applied Cryptography: 3. Hash functions and HMAC
Lecture 3: Cryptographic hash function and its properties, brute-force attack and security level, security of server-side password hashing, commitment scheme...

Applied Cryptography by University of Tartu
635 views • May 22, 2024
About this video
Lecture 3: Cryptographic hash function and its properties, brute-force attack and security level, security of server-side password hashing, commitment scheme, hash-based PRNG, hash chain, hash tree (Merkle tree), Hash-based Message Authentication Code (HMAC)
00:00 Introduction
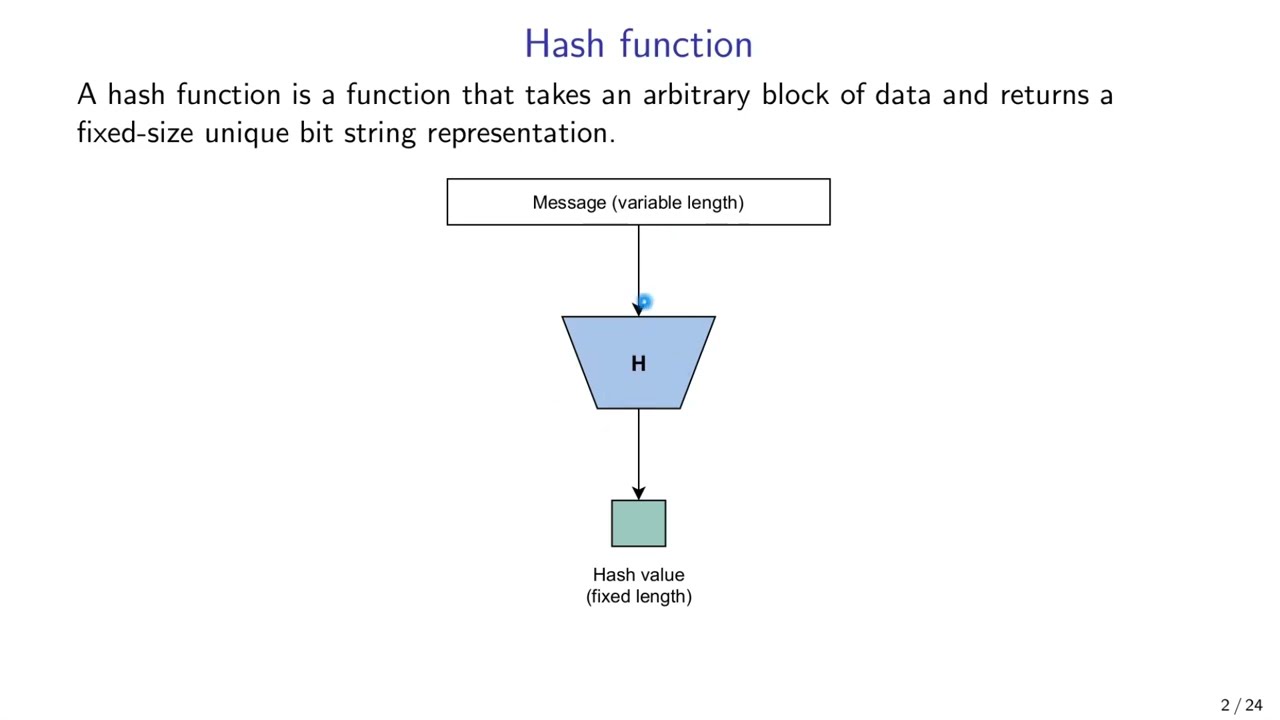
00:12 Hash function
03:09 Cryptographic hash function
07:02 Security Level
11:08 Cryptographic hash functions
14:56 Data identification and integrity verification
19:29 Server-side password storage
30:57 Commitment scheme
36:13 Coin flipping over phone
38:20 Hash-based PRNG
41:05 Hash chain
44:06 Hash tree (Merkle tree)
47:01 HMAC: Hash-based Message Authentication Code
50:49 Questions
50:56 Task: HMAC
52:19 DigestInfo
53:18 Task: HMAC
55:06 Task: Test cases
56:01 pyasn1 library for decoding DER
University of Tartu, MTAT.07.017 Applied Cryptography, Spring 2024
Instructor: Arnis Parsovs
View the complete course: https://courses.cs.ut.ee/2024/appcrypto/spring
00:00 Introduction
00:12 Hash function
03:09 Cryptographic hash function
07:02 Security Level
11:08 Cryptographic hash functions
14:56 Data identification and integrity verification
19:29 Server-side password storage
30:57 Commitment scheme
36:13 Coin flipping over phone
38:20 Hash-based PRNG
41:05 Hash chain
44:06 Hash tree (Merkle tree)
47:01 HMAC: Hash-based Message Authentication Code
50:49 Questions
50:56 Task: HMAC
52:19 DigestInfo
53:18 Task: HMAC
55:06 Task: Test cases
56:01 pyasn1 library for decoding DER
University of Tartu, MTAT.07.017 Applied Cryptography, Spring 2024
Instructor: Arnis Parsovs
View the complete course: https://courses.cs.ut.ee/2024/appcrypto/spring
Video Information
Views
635
Likes
10
Duration
57:46
Published
May 22, 2024