AES Round Transformation in Network Security
This document discusses the various transformations involved in the AES encryption and decryption process for each round, including key concepts and methodologies.

Neso Academy
144.4K views • Aug 27, 2023
About this video
Network Security: AES Round Transformation
Topics discussed:
1. Various Transformations in AES Encryption and Decryption process in every round.
2. How Confusion and Diffusion properties are added to AES.
3. Substitute Bytes AES Transformation Function with an example.
4. Shift Rows AES Transformation Function with an example.
5. Mix Columns AES Transformation Function with an example.
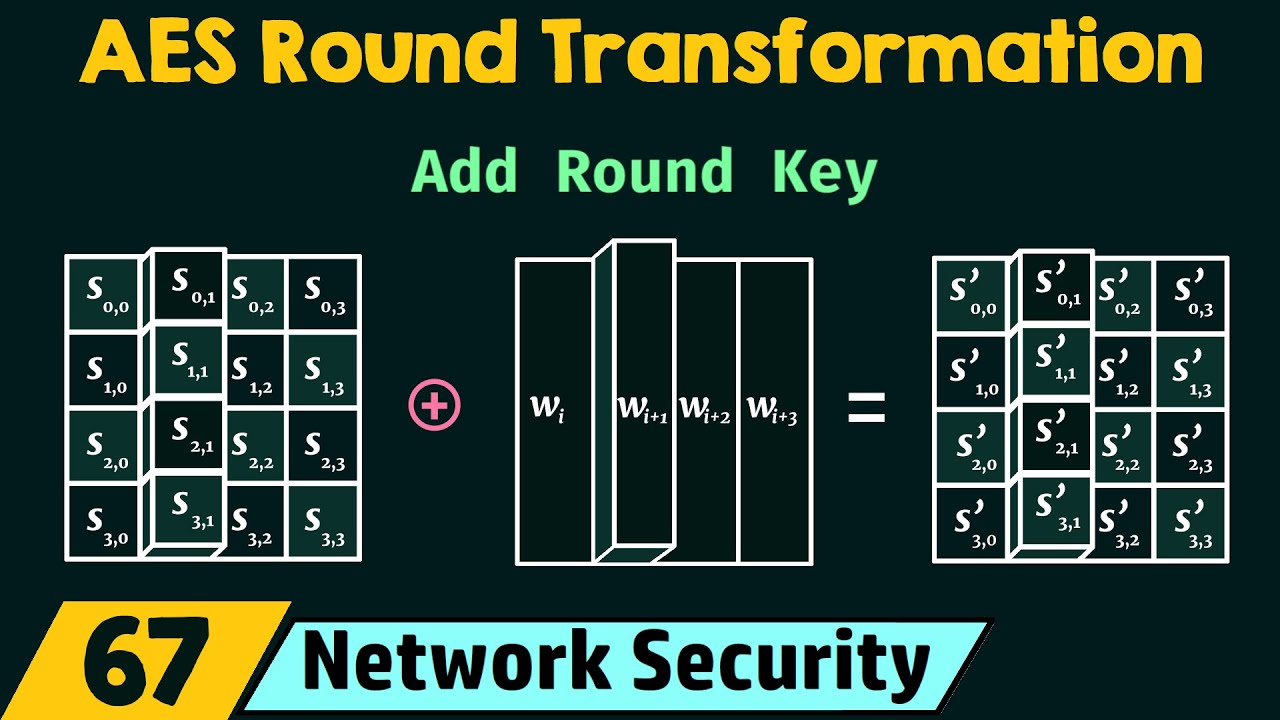
6. Add Round Key AES Transformation function with an example.
Follow Neso Academy on Instagram: @nesoacademy (https://bit.ly/2XP63OE)
Contribute: http://bit.ly/3EpZgBD
Memberships: https://bit.ly/2U7YSPI
Discord: https://bit.ly/3HiGtJr
WhatsApp: https://whatsapp.com/channel/0029Va9B1Bq4tRru0nqgtx3h
Books: https://bit.ly/4cZYQil
Website ► https://www.nesoacademy.org/
App ► https://play.google.com/store/apps/details?id=org.nesoacademy
Facebook ► https://www.facebook.com/nesoacademy
Twitter [X] ► https://x.com/nesoacademy
Music:
Axol x Alex Skrindo - You [NCS Release]
#NetworkSecurityByNeso #Cryptography #AdvancedEncryptionStandard
Topics discussed:
1. Various Transformations in AES Encryption and Decryption process in every round.
2. How Confusion and Diffusion properties are added to AES.
3. Substitute Bytes AES Transformation Function with an example.
4. Shift Rows AES Transformation Function with an example.
5. Mix Columns AES Transformation Function with an example.
6. Add Round Key AES Transformation function with an example.
Follow Neso Academy on Instagram: @nesoacademy (https://bit.ly/2XP63OE)
Contribute: http://bit.ly/3EpZgBD
Memberships: https://bit.ly/2U7YSPI
Discord: https://bit.ly/3HiGtJr
WhatsApp: https://whatsapp.com/channel/0029Va9B1Bq4tRru0nqgtx3h
Books: https://bit.ly/4cZYQil
Website ► https://www.nesoacademy.org/
App ► https://play.google.com/store/apps/details?id=org.nesoacademy
Facebook ► https://www.facebook.com/nesoacademy
Twitter [X] ► https://x.com/nesoacademy
Music:
Axol x Alex Skrindo - You [NCS Release]
#NetworkSecurityByNeso #Cryptography #AdvancedEncryptionStandard
Tags and Topics
Browse our collection to discover more content in these categories.
Video Information
Views
144.4K
Likes
1.8K
Duration
11:04
Published
Aug 27, 2023
User Reviews
4.5
(28) Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.