03 From Threat to Defense: Building a Quantum-Safe Future 🌐
Ikhtear Bhuyan explores the rapid advancements in quantum computing and how organizations can prepare for a secure, quantum-resistant digital world.

BSides Toronto
26 views • Oct 12, 2025
About this video
Ikhtear Bhuyan presents on the global acceleration in quantum computing research and development presents a fundamental shift in the threat landscape for cybersecurity. For decades, organizations have relied on classical cryptographic algorithms—such as RSA, ECC, and Diffie-Hellman—to secure sensitive data, protect identities, and ensure the confidentiality and integrity of communications. However, the advent of cryptographically relevant quantum computers (CRQCs) poses an existential threat to these algorithms. With quantum algorithms like Shor’s and Grover’s, adversaries will be able to break widely used encryption and signature schemes at scale, rendering current protections obsolete.
This evolving risk makes the transition to quantum-safe cryptography not just advisable, but essential. The process of securing environments against future quantum threats—known as Quantum-Safe Discovery and Remediation—is a structured approach that involves identifying vulnerable cryptographic assets, assessing business impact, and migrating to NIST-approved post-quantum cryptographic (PQC) algorithms such as CRYSTALS-Kyber and Dilithium.
In this session, we explore the technical and strategic foundations required for quantum resilience. Participants will gain insights into:
• Cryptographic asset discovery and classification across legacy and hybrid IT environments
• Risk assessment methodologies that prioritize high-value data and systems
• Crypto-agility strategies that enable flexible algorithm replacement without significant architectural redesign
• Implementation of hybrid cryptographic models that combine classical and PQC algorithms during transition
• Integration with regulatory frameworks and compliance standards (e.g., NIST SP 800-208, ISO/IEC 23837)
We also address key operational considerations such as key management, lifecycle automation, performance benchmarking, and vendor interoperability. This session is designed for security architects, IT leaders, and compliance professionals seeking to understand the technical steps necessary to protect digital infrastructure from quantum-enabled threats.
By adopting a phased and proactive approach, organizations can future-proof their cryptographic posture, ensure business continuity, and preserve digital trust in the face of quantum disruption.
The accelerated development of quantum computing presents a direct threat to classical cryptographic primitives such as RSA, ECC, and DH. These algorithms, long relied upon to secure critical data and communications, are vulnerable to quantum attacks—most notably Shor’s algorithm, which enables efficient factorization and discrete logarithm resolution on a sufficiently powerful quantum computer.
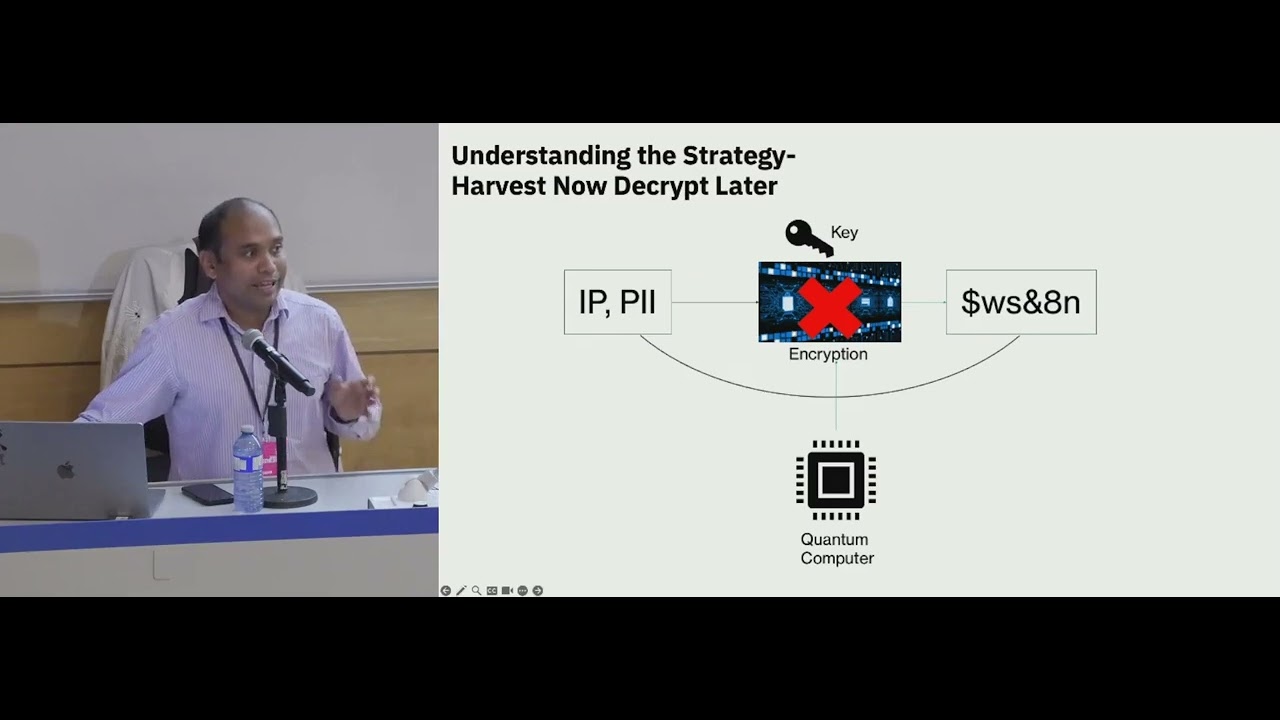
This shift introduces the risk of cryptographic collapse: adversaries will be able to retroactively decrypt intercepted data ("harvest now, decrypt later"), manipulate digital signatures, and break authentication mechanisms—potentially within hours of a quantum breakthrough.
To mitigate this, organizations must proactively conduct Quantum-Safe Discovery and Remediation. This involves identifying cryptographic assets across the environment, evaluating risk exposure, and migrating to quantum-resistant algorithms as standardized by NIST (e.g., CRYSTALS-Kyber, Dilithium).
This evolving risk makes the transition to quantum-safe cryptography not just advisable, but essential. The process of securing environments against future quantum threats—known as Quantum-Safe Discovery and Remediation—is a structured approach that involves identifying vulnerable cryptographic assets, assessing business impact, and migrating to NIST-approved post-quantum cryptographic (PQC) algorithms such as CRYSTALS-Kyber and Dilithium.
In this session, we explore the technical and strategic foundations required for quantum resilience. Participants will gain insights into:
• Cryptographic asset discovery and classification across legacy and hybrid IT environments
• Risk assessment methodologies that prioritize high-value data and systems
• Crypto-agility strategies that enable flexible algorithm replacement without significant architectural redesign
• Implementation of hybrid cryptographic models that combine classical and PQC algorithms during transition
• Integration with regulatory frameworks and compliance standards (e.g., NIST SP 800-208, ISO/IEC 23837)
We also address key operational considerations such as key management, lifecycle automation, performance benchmarking, and vendor interoperability. This session is designed for security architects, IT leaders, and compliance professionals seeking to understand the technical steps necessary to protect digital infrastructure from quantum-enabled threats.
By adopting a phased and proactive approach, organizations can future-proof their cryptographic posture, ensure business continuity, and preserve digital trust in the face of quantum disruption.
The accelerated development of quantum computing presents a direct threat to classical cryptographic primitives such as RSA, ECC, and DH. These algorithms, long relied upon to secure critical data and communications, are vulnerable to quantum attacks—most notably Shor’s algorithm, which enables efficient factorization and discrete logarithm resolution on a sufficiently powerful quantum computer.
This shift introduces the risk of cryptographic collapse: adversaries will be able to retroactively decrypt intercepted data ("harvest now, decrypt later"), manipulate digital signatures, and break authentication mechanisms—potentially within hours of a quantum breakthrough.
To mitigate this, organizations must proactively conduct Quantum-Safe Discovery and Remediation. This involves identifying cryptographic assets across the environment, evaluating risk exposure, and migrating to quantum-resistant algorithms as standardized by NIST (e.g., CRYSTALS-Kyber, Dilithium).
Video Information
Views
26
Likes
1
Duration
28:05
Published
Oct 12, 2025
Related Trending Topics
LIVE TRENDSRelated trending topics. Click any trend to explore more videos.