Search Results for "verifiable credentials saml"
Find videos related to your search query. Browse through our collection of videos matching "verifiable credentials saml". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "verifiable credentials saml"
20 results found

15:03
Verifiable Credentials Using Blockchain | Digital Identity | Microsoft Ignite 2020
Microsoft Mechanics
25.3K views

15:42
CCT 059: SAML, OAuth, OPENID - CISSP Exam Questions (Domain 5) #shongerber
CISSP Cyber Training - Shon Gerber
284 views
![Revisiting Keyed-Verification Credentials [CAW 2025]](/image/i.ytimg.com/vi/n66D5Q4cVvo/xhqdefault.jpg.pagespeed.ic.aPRQo6OmbB.jpg)
38:53
Revisiting Keyed-Verification Credentials [CAW 2025]
Miro Haller
10 views

7:17
Security Academy Practical Ethical Hacking - Gathering Breached Credentials with Breach-Parse
Tutorials Arena
419 views

13:30
Encrypt & Decrypt user credentials | Crypto-JS | Playwright Tutorial - Part 89
LetCode with Koushik
31.9K views
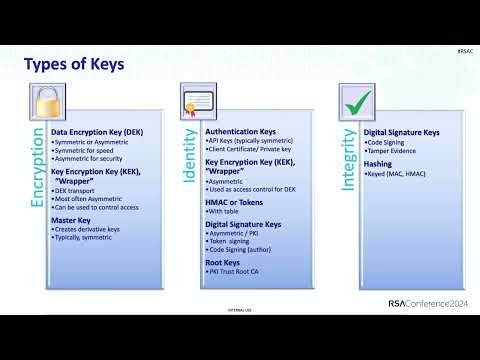
50:59
Key Management 101: DEKs, KEKs, and Credentials Living Together, Oh My!
RSA Conference
989 views

2:03
How to SIGN INTO Your Microsoft Office 365 Account Using Your Credentials | New
ComputerScienceVideos
261 views

1:24
How to SIGN OUT of Your Microsoft Office 365 Account Using Your Credentials | New
ComputerScienceVideos
2.2K views

51:27
The 6th BIU Winter School: Intoducion and Overview of Verifiable Computation - Michel Walfish
The BIU Research Center on Applied Cryptography and Cyber Security
1.2K views
![Advanced KEM Concepts: (Hybrid) Obfuscation and Verifiable Decapsulation [CAW 2025]](/image/i.ytimg.com/vi/CBax2CSl1dQ/hqdefault.jpg)
30:11
Advanced KEM Concepts: (Hybrid) Obfuscation and Verifiable Decapsulation [CAW 2025]
Miro Haller
27 views

16:22
Geppetto: Versatile Verifiable Computation
IEEE Symposium on Security and Privacy
1.4K views
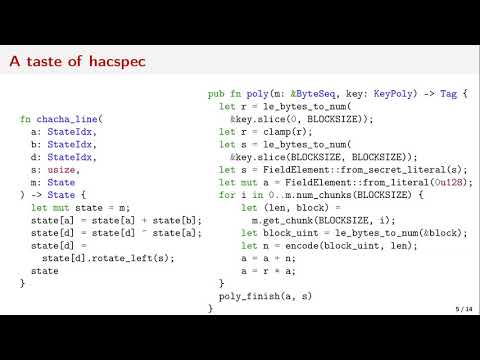
25:32
hacspec: succinct, executable, verifiable specifications for high-assurance cryptography
Rust
591 views

10:44
Are Theories Verifiable? (Contrastive Underdetermination)
Carneades.org
4.9K views

0:17
Verifiable Summit 2024! The Biggest Cryptography Event of the Year!
Verifiable Summit
15 views

0:54
Attribute-Based Encryption With Verifiable Outsourced Decryption
JPInfo
1 views
0:44
Circuit Ciphertext-policy Attribute-based Hybrid Encryption with Verifiable Delegation in Cloud
career explorer
47 views

1:21
Circuit Cipher text-policy Attribute-based Hybrid Encryption with Verifiable Delegation
LansaInformatics
134 views

13:05
Circuit Ciphertext policy Attribute based Hybrid Encryption with Verifiable Delegation in Cloud Comp
Cloud Technologies
570 views

4:06
Circuit Ciphertext-policy Attribute-based Hybrid Encryption with Verifiable Delegation
MICANS IEEE PROJECTS 2015 PPT VIDEOS
990 views
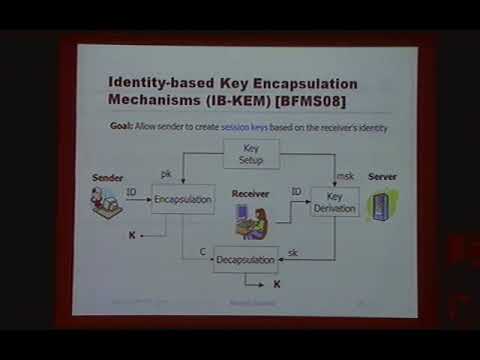
53:38
Verifiable Random Functions and Their Relation to Identity-Based Encryption -1
Mathnet Korea
355 views
Page 1