Search Results for "uses"
Find videos related to your search query. Browse through our collection of videos matching "uses". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "uses"
50 results found
0:47
Tryptomer 10 mg uses in hindi. Amitriptyline uses in hindi. #Amitriptyline #tryptomer #shorts
Dr. Mayank Agrawal
173.1K views
0:30
Uses of C Language #clanguage #uses
Coding Version
43 views

0:20
Uses of JavaScript - JavaScript - Uses of Javascript
Coding Version
12 views

6:47
uses of computer for kids, uses of computer for class 1, use of computer in school @TeachWithAnchal
Amritanchal Study
55 views

2:09
Longtail Keyword Research Software Uses Google Autosuggest-win Or Mac | Longtail Keyword Research Software Uses Google Autosuggest-win Or Mac
DarinGaskell
5 views

3:01
276 Historical Uses of Symmetric Cryptography GÇö Running Key and Concealment
Rezky Wulandari
1.8K views

0:12
Asymmetric encryption uses two keys
Next Gen Synthetix
64 views

0:49
5 Mind Bending Uses of Quantum Computers!
FACTS2AMAZE
917 views

8:26
Cryptography and its Uses Today
YoungWonks
3.7K views
![[বাংলা] Beginner To Advance CTF #Day-20 - Uses of Steganography Tools | Steganography Crash Course](/image/i.ytimg.com/vi/1GNHdscTTLY/xhqdefault.jpg.pagespeed.ic.msbQzmUgBz.jpg)
22:17
[বাংলা] Beginner To Advance CTF #Day-20 - Uses of Steganography Tools | Steganography Crash Course
InfoSec BD
3.2K views

0:30
New Malware 'Koske' Uses Steganography to Hide in Images: Protect Your Linux System
Hacked dAily
850 views

28:38
#ክሪፕቶግራፊ How Blockchain Uses SHA-256 for Cryptographic Hashing | Simplified in Amharic
Self Programmers
268 views

23:28
How the CIA uses animals to spy
fern
1.9M views
0:43
Quantum computing developer uses python (+ reveals his favorite framework)
Clever Programmer
32.4K views

6:13
How blockchain uses hashing technology
Programming w/ Professor Sluiter
3.3K views
0:17
When a programmer uses a LIGHT THEME 🤦♂️ #code #programming #technology #tech #software #developer
Coding with Lewis
2.9M views

26:51
GOLD DIGGER USES Overweight Date For DINNER | Dhar Mann Bonus!
Dhar Mann Bonus
1.5M views

0:16
Good Health Capsule Uses in Hindi | Liv 52 ds Tablet #liv52dstablet #liv52 #goodhealthcap
Seva Creator
767.1K views
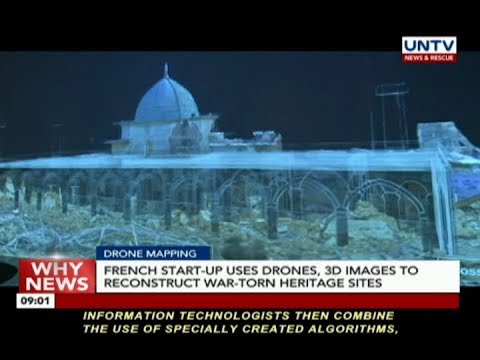
2:12
French start-up uses drones, 3D images to reconstruct war-torn heritage sites
UNTV News and Rescue
538 views

0:34
Instead of creating complex rigs, this subtle scene only uses Moho's point animation
Moho Animation Software
34.4K views

13:21
SUBLIME TEXT 3 (PART-II) INSTALLATION, PACKAGE CONTROL & IT'S PACKAGES INSTALLATION WITH ITS USES
Sticky Code
211 views

0:50
Encryption Basics: Types, Uses, and Benefits | Abc Hack Tech
Abc Hack Tech
176 views

0:45
Top 3 Uses of Quantum Mechanics | Physics Facts | Science | #shortvideo #shorts #science #technology
5MinuteScience
181 views

3:07
What is Cryptography in Mathematics? | Examples | Importance | Uses | Urdu/Hindi
Watch And Learn
576 views

27:46
CYSAT 2025 – Post-Quantum Cryptography: Key challenges and uses for embedded systems and satellites.
CYSAT
157 views

6:37
How AI uses our drinking water - BBC World Service
BBC World Service
449.8K views
0:41
How WhatsApp uses end-to-end encryption to keep your messages secure #shorts #programming #coding
Tom Shaw
7.0K views

1:01
How Your Key Fob Uses Radio Waves and Cryptography #howitworks #facts #mindblown
How it Works?
102 views

1:52
6 Alternative Uses For Hand Sanitizer You Need To Know Now | Hand Sanitizer Tips Hacks And Tricks
let's do a recap
5.1K views
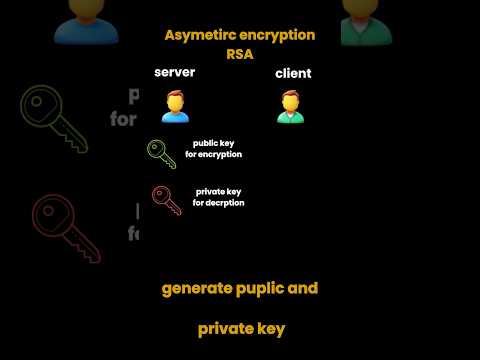
0:56
“Asymmetric encryption 🔐 uses a pair of keys—public 🗝️ and private 🔑 #coding #linuxcommands
gst_software
68 views

0:55
The Mind-Blowing History and Uses of Cryptography 🔐
Libertas
585 views

5:46
Cryptography|| Linear Algebra #@ _||adjoint|| inverse matrix multiplication || uses of cryptography
Engr. Narendher Kumar Khokhar
295 views
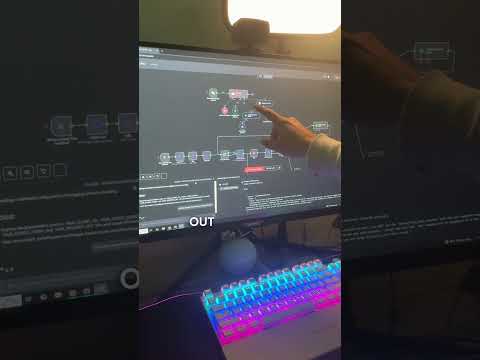
0:44
This n8n workflow literally builds other AI agents for you. It uses a Retrieval-Augmented Generatio
Bennett Spooner
21.0K views

0:47
Why Encryption System uses Prime Numbers? #shorts #primenumbers #encryption
DrTOMMY
160 views

2:23
Potential Uses for Quantum Computers - Charles Bennett
Institute for Quantum Computing
3.1K views

0:14
Frisk uses mercy (Undertale Animation)
JaydenAnimationz
8.9M views

2:28
How IBM uses Software Analytics to "Shift Left" and Enhance Traditional Development & Testing Tools
CAST
370 views

0:57
A man uses 69 IQ | Movie Recap #shorts #movierecap
Arax Summarise
1.3M views

19:54
RSA Algorithm | Cryptography | Uses of Prime Numbers | Explanation with example in Tamil.
Shar Edu
1.4K views

21:51
Cryptography Fundamentals: Algorithms, Uses & Limitations Explained | Module 3
Joseph H.Schuessler
102 views
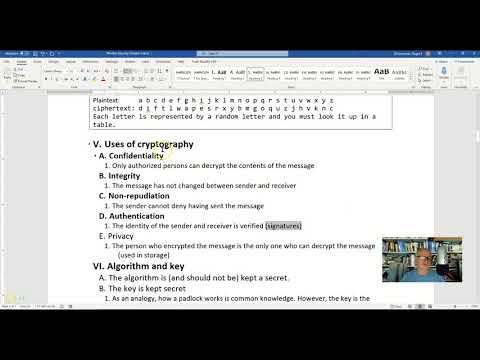
2:14
Uses of cryptography
Roger Zimmerman
550 views

7:44
What is Cryptography? uses of Cryptography {IN TELUGU}
Hackin4min [Telugu Hacking]
629 views

0:31
Which encryption type uses a SHARED key?
InfoTechSite
117 views

9:15
Cryptography क्या है ? |- Symmetric vs Asymmetric cryptography -| Uses of cryptography -|
StudyWithEngineers
655 views

1:12:27
【Eng Dub】Girl uses tuition to help homeless, CEO witnesses and falls in love!
Manman Drama English
692.0K views

10:56
When Player Uses Speed To Humiliate 2025
SportsHD
585.0K views

6:55
Java Cryptography Uses in the Wild
ESEM 2021
52 views

9:46
The A to Z Uses & Abuses Of Python In The Hacking World.
Chill Circuit
1.3K views

0:28
Sabalenka uses Djokovic for TARGET practice! 🤣
US Open Tennis Championships
17.8M views

9:50
Modular Athematic | uses in Classical Encryption Techniques | Cryptography | Chapter 2 | Lecture 14
Koncept Recall
6 views