Search Results for "ssh user authentication protocol"
Find videos related to your search query. Browse through our collection of videos matching "ssh user authentication protocol". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "ssh user authentication protocol"
51 results found

25:33
SSH | SSH Protocol Stack | SSH Protocols explain with animation | Why SSH? | Secure Shell (SSH)
Chirag Bhalodia
22.9K views

5:06
Telnet vs SSH Protocol | Why SSH is More Secure than Telnet!
Md. Mosarraf Hossain
148 views

8:37
SSH (Secure shell) protocol in Hindi | Secure shell protocol in Network Security
Abhishek Sharma
84.3K views

20:53
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Chirag Bhalodia
33.5K views

11:49
Authentication functions and 3 ways to produce authentication | Message authentication
Abhishek Sharma
263.4K views

47:26
SSH Public Key Fingerprints, Windows SSH Servers and Linux Key Pair Exchange - Hak5
Hak5
4 views
10:58
SSH (1/11) - Mehrwert von SSH & asymmetrische Verschlüsselung einfach erklärt - LF 4,11,12
Lehrer Go
1.4K views
19:49
Learn SSH in one video | Symmetric and Asymmetric cryptography basics | SSH tutorial in hindi
Deepu Singh
444 views

2:06
Virtual Protocol Latest News Today In Hindi | Virtual Protocol Crypto | Virtual Protocol News | BTC
MR KRYPTO
42 views

0:30
Rangers protocol vvip protocol Punjab pakistan | Rangers | protocol vvip | Ghouri4u Official
Ghouri4u official
18 views
2:38
How To setup VPS with Public Key Authentication (Bitvise ssh)
panduanvps
3 views

58:48
Proxies, Linux SSH Servers, Windows Clients and Public Key Authentication - Hak5
Hak5
4 views

13:16
Public Key vs Private Key | SSH Authentication | DevOps Realtime Interview Questions
DevOps and Cloud with Siva
12.4K views

17:02
9 - Cryptography Basics - SSH Protocol Explained
CBTVid
43.1K views

0:21
IRCTC User Id & password kaise banaye Hindi #How to create IRCTC user is & password
BIKASH 4888
3.1M views

8:22
How to input data from keyboard in python | keyboard input in python | read data from keyboard | python practically | easy way of python programming | python basics | read data from user | input from user in python | input function in python
ALL IN ONE
8 views

14:01
VB.NET Creating Login with Admin & User (User Level)
Codinger Tutorial
14 views

5:39
How to input data from keyboard in python | keyboard input in python | read data from keyboard | python practically | easy way of python programming | python basics | read data from user | input from user in python | input function in python
ALL IN ONE
1 views

19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views

2:46
USER AUTHENTICATION USING CRYPTOGRAPHY AND STEGANOGRAPHY FOR WEB APPLICATIONS
Gagan Suneja
214 views

13:49
Remote User Authentication using Asymmetric Encryption in Network Security | Woo and Lam Proposal
Chirag Bhalodia
30.0K views

21:42
Remote User Authentication: Principles & Techniques | Cryptography- #21is71 #cryptography #vtupadhai
VTU padhai
4.0K views

0:30
About For Books Mechanics of User Identification and Authentication: Fundamentals of Identity
dm_09d226e7605f9f5a1a3a6425e52120d4
0 views

4:27
Introduction to User Authentication - CompTIA Network+ N10-005: 5.3
Professor Messer
15.0K views

8:37
Remote user authentication using symmetric encryption
Anand Pashupatimath
4.6K views
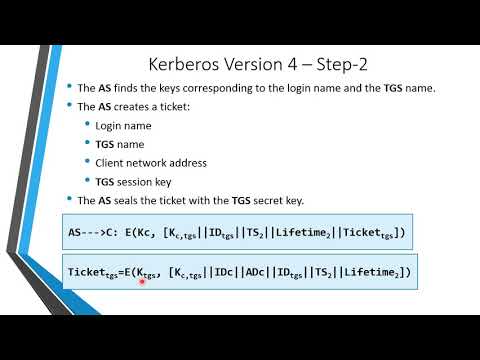
20:25
INS: Unit-9 Remote User-Authentication (Kerberos)
Twinkal Patel
423 views

1:09:38
CSE571-11-15B: User Authentication Protocols (Part 2 of 3)
Raj Jain
1.8K views

0:40
Why Continuous User Authentication Matters
CyberGuard
1 views

0:27
Unlocking the Secrets of User Authentication
CyberGuard
0 views

58:47
Kerberos Version 4 & 5 and Remote User Authentication with Asymmetric Encryption -#21is71 VTU 7thsem
VTU padhai
2.3K views
13:31
Build Node.js User Authentication - Password Login
Web Dev Simplified
565.0K views

2:30
Briefly describe on characteristics of the UDP(User datagram protocol)
Informative Tutorials
159 views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

13:38
Cryptography (18CS744) Mutual authentication, one way authentication, kerberos and kerberos diff
1VA19CS061 YASHAS HM
106 views

7:01
#40 Kerberos - Authentication Protocol, Working with diagram|CNS|
Trouble- Free
304.6K views

6:43
Kerberos Authentication Protocol 🔥🔥
Perfect Computer Engineer
198.5K views
6:08
Kerberos - authentication protocol
Sunny Classroom
506.1K views

13:18
Authentication protocol | Cryptography and Network Security
Ekeeda
2.0K views

0:31
Visual OTP: The Visual One Time Password Authentication Protocol
Visual OTP
462 views

4:49
Kerberos Authentication Protocol | Cryptography and System Security
Ekeeda
56 views

39:35
19-Learn Kerberos in Network Security 🔐 | How Kerberos Works? | Authentication Protocol Made Simple
Sundeep Saradhi Kanthety
184.1K views
14:24
The Kerberos Authentication Protocol Explained
Suckless Programmer
306 views

13:37
Kerberos - Network Authentication Protocol
Cyber Security Entertainment
604 views

6:35
Kerberos - Network Authentication Protocol explained in hindi || Working ,History ,AS ,TGS and AP
Unbeaten Learning
112.9K views

9:11
TCP/IP Model | Internet protocol suite | Protocol and services of TCP/IP Model
Chirag Bhalodia
1.5K views

3:22
Alpha Protocol - Alpha Protocol - Developers Diary
Games2C_INT
9 views

2:05
Ed Protocol Ingredients || Erectile Dysfunction Protocol
Helenaghv
8 views

9:59
Alpha Protocol Walkthrough - Infiltrate Alpha Protocol ...
MahaloGames
1 views

1:32
Massive protocol PM Abbasi Protocol in Karachi
MTV
49 views

0:38
Bluesky Gains Over 5 Million New Users Since Election Surge As Users Exit Elon Musk's X
Benzinga
1.1K views
Page 1 Next