Search Results for "ssh authentication protocol"
Find videos related to your search query. Browse through our collection of videos matching "ssh authentication protocol". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "ssh authentication protocol"
50 results found

25:33
SSH | SSH Protocol Stack | SSH Protocols explain with animation | Why SSH? | Secure Shell (SSH)
Chirag Bhalodia
22.9K views

5:06
Telnet vs SSH Protocol | Why SSH is More Secure than Telnet!
Md. Mosarraf Hossain
148 views

8:37
SSH (Secure shell) protocol in Hindi | Secure shell protocol in Network Security
Abhishek Sharma
84.3K views

11:49
Authentication functions and 3 ways to produce authentication | Message authentication
Abhishek Sharma
263.4K views
19:49
Learn SSH in one video | Symmetric and Asymmetric cryptography basics | SSH tutorial in hindi
Deepu Singh
444 views
10:58
SSH (1/11) - Mehrwert von SSH & asymmetrische Verschlüsselung einfach erklärt - LF 4,11,12
Lehrer Go
1.4K views

47:26
SSH Public Key Fingerprints, Windows SSH Servers and Linux Key Pair Exchange - Hak5
Hak5
4 views

2:06
Virtual Protocol Latest News Today In Hindi | Virtual Protocol Crypto | Virtual Protocol News | BTC
MR KRYPTO
42 views

0:30
Rangers protocol vvip protocol Punjab pakistan | Rangers | protocol vvip | Ghouri4u Official
Ghouri4u official
18 views

13:16
Public Key vs Private Key | SSH Authentication | DevOps Realtime Interview Questions
DevOps and Cloud with Siva
12.4K views
2:38
How To setup VPS with Public Key Authentication (Bitvise ssh)
panduanvps
3 views

58:48
Proxies, Linux SSH Servers, Windows Clients and Public Key Authentication - Hak5
Hak5
4 views
17:02
9 - Cryptography Basics - SSH Protocol Explained
CBTVid
43.1K views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

13:38
Cryptography (18CS744) Mutual authentication, one way authentication, kerberos and kerberos diff
1VA19CS061 YASHAS HM
106 views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

7:01
#40 Kerberos - Authentication Protocol, Working with diagram|CNS|
Trouble- Free
304.6K views

4:49
Kerberos Authentication Protocol | Cryptography and System Security
Ekeeda
56 views
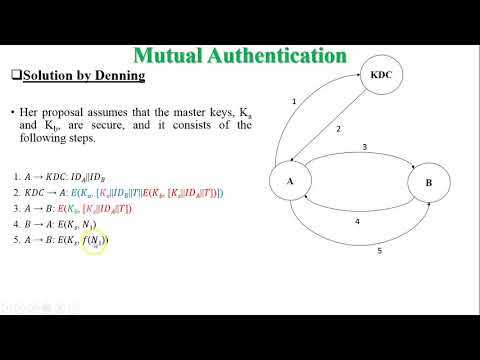
20:53
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Chirag Bhalodia
33.5K views

6:35
Kerberos - Network Authentication Protocol explained in hindi || Working ,History ,AS ,TGS and AP
Unbeaten Learning
112.9K views
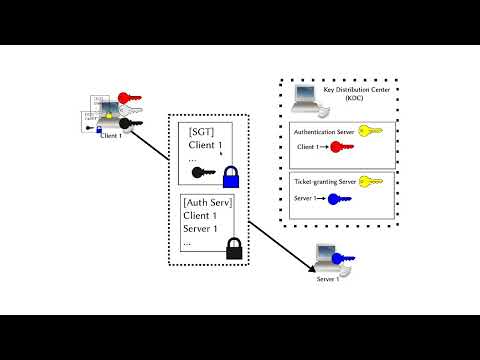
14:24
The Kerberos Authentication Protocol Explained
Suckless Programmer
306 views

6:43
Kerberos Authentication Protocol 🔥🔥
Perfect Computer Engineer
198.5K views

39:35
19-Learn Kerberos in Network Security 🔐 | How Kerberos Works? | Authentication Protocol Made Simple
Sundeep Saradhi Kanthety
184.1K views

13:18
Authentication protocol | Cryptography and Network Security
Ekeeda
2.0K views

13:37
Kerberos - Network Authentication Protocol
Cyber Security Entertainment
604 views
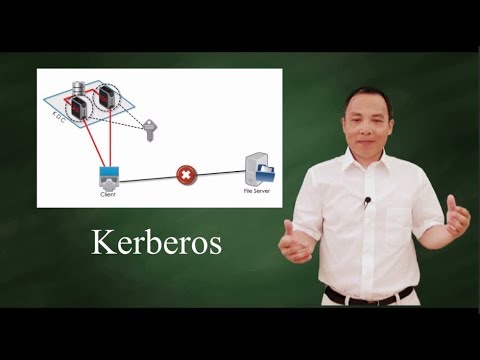
6:08
Kerberos - authentication protocol
Sunny Classroom
506.1K views
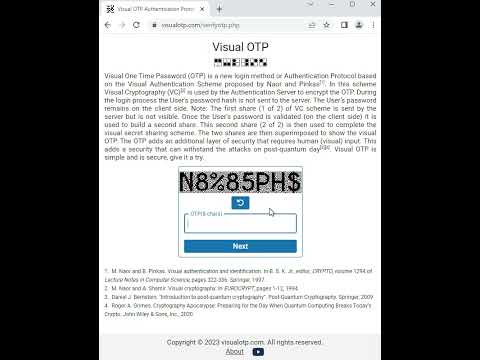
0:31
Visual OTP: The Visual One Time Password Authentication Protocol
Visual OTP
462 views
0:06
Encryption Protocol. #cybersecurity #cyberpunk #viral #protocol #sslcertificate
Infintysec
179 views

9:11
TCP/IP Model | Internet protocol suite | Protocol and services of TCP/IP Model
Chirag Bhalodia
1.5K views

11:00
Web and HTTP protocol tutorial | Hypertext Transfer Protocol explained | World Wide Web | TechTerms
TechTerms
65.6K views

1:45
erase herpes protocol review - erase herpes protocol
Get rid of hives
24 views

2:05
Ed Protocol Ingredients || Erectile Dysfunction Protocol
Helenaghv
8 views

2:33
Ed Protocol Review || Erectile Dysfunction Protocol Review
Vernitaw0z
1 views
1:27
people Bushing Sharif Brothers Because of protocol In jinah hospital because of protocol
harpal.pk
16 views

1:24
IMAM E KABA PROTOCOL IN PAKISTANIMAM E KABA PROTOCOL IN PAKISTAN
All In one
1 views

1:32
Massive protocol PM Abbasi Protocol in Karachi
MTV
49 views
5:18
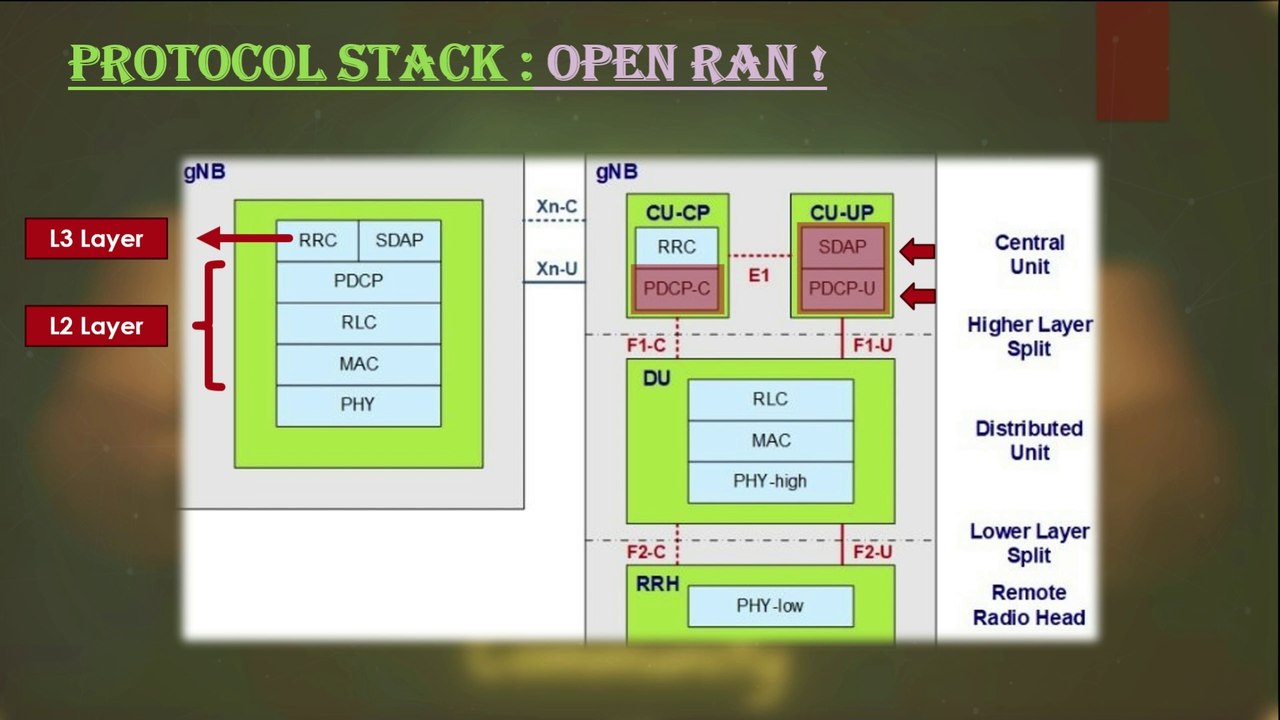
Session 11 : Open RAN Protocol Stack | PDCP Protocol and SDAP Layer
Learn And Grow Community
10 views

9:59
Alpha Protocol Walkthrough - Infiltrate Alpha Protocol ...
MahaloGames
1 views

14:31
Network Protocol Explained | Types Of Network Protocol | Fundamentals Of Networking | Simplilearn
Simplilearn
1.4K views

3:22
Alpha Protocol - Alpha Protocol - Developers Diary
Games2C_INT
9 views

8:54
How SSH Works
Mental Outlaw
725.6K views

33:11
CNS UNIT - 4|Secure Socket Layer,Transport Layer Security,HTTPS,SSH, IEEE 802.11 i | JNTUH #r18 #r22
One Day Batting
8.5K views

10:31
Como Funciona o SSH: Segurança Digital e Criptografia Descomplicadas
CyberBuild Tech
1.3K views

0:48
Diferença entre criptografia simétrica e assimétrica #hacker #cybersecurity #criptografia #ssh
HackingNaTuga
81 views

48:04
Role of Cryptography in Network Security: DES & RSA algorithms, SSL, SSH
Information Security Awareness
46 views

0:11
Default Encryption Algorithm in SSH: 🔒 AES #shortsfeed #viral #gk #gkquiz
TechWiseNow
316 views

10:12
SSH Keys
RobEdwards
169.8K views
1:12
Generate Crypto Keys & SSH Like A Pro!
The Networking Doctors
119 views

7:48
IPsec vs. SSH vs. SSL/TLS | Network Security Protocols
Gate Smashers
68.2K views

1:45
Password Cracking: Cracking SSH known_hosts File
Pentester Academy TV
1.4K views
Page 1