Search Results for "security attacks on cryptographic hash function"
Find videos related to your search query. Browse through our collection of videos matching "security attacks on cryptographic hash function". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "security attacks on cryptographic hash function"
51 results found

12:00
Hash Function in cryptograhy | Properties of Hash Function | Simple Hash Function Technique
Chirag Bhalodia
107.9K views

14:52
Applications of Hash Function | Purpose of Hash Function | Real Time Application of Hash Function
Chirag Bhalodia
32.1K views

9:00
Hash Functions || hash function algorithm || hash function cryptography || hashing vs encryption
The Ecomly Tech
24 views

8:19
LEC11| Blockchain | Cryptographic Hash Function & Properties of Hash Function by Mrs. G. Sowmya
MLID - MLR Institute of Technology
2.3K views

10:30
Introduction to HASHING in Data Structures || Hash Functions,Hash Table, Hash Keys,Hash Values in DS
Sundeep Saradhi Kanthety
11.5K views

0:13
Hash Oil,buy Hash oil online,Hash oil for sale,Prefilled hash oil cartridges for sale http://dabstarshop.com
dabstarshop dabstarspharmacy
1 views

9:32
Hash function Keya hai? hashing Algorithm? password hashing? password and hash function Hindi
Technical Haroon
8.1K views

7:40
Hash function based on CBC in cryptography | Hash function based on cipher block chaining
Chirag Bhalodia
24.0K views
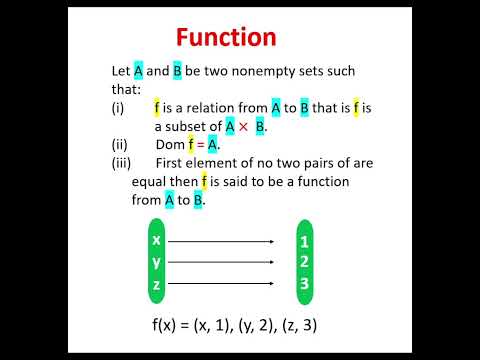
0:09
Function | Definition of function | define function | simple definition of function
Tartull education
23.4K views

13:18
Introduction to Cryptographic Hash Function| Merkel Damgard Scheme | SHA-256 | Secure Hash Algorithm
Muhammed Mustaqim
607 views

37:31
Five* non-cryptographic hash functions enter. One hash function leaves.
Linux.conf.au 2016 -- Geelong, Australia
4.7K views

1:02:56
Network Security - Cryptographic Hash Functions (Security Requirements and Attacks)
Waqas Ali
125 views

6:55
Attacks on Cryptographic Hash Algorithms || what is cryptographic? || Best Mind Like
Best Mind Like
45 views

8:50
Introduction to Cryptographic Attacks | Types of Cryptographic Attacks Explained With Measures
Shree Learning Academy
2.3K views

26:58
SHA-512 ALGORITHM || SECURE HASH ALGORITHM || CRYPTOGRAPHIC HASH FUNCTIONS || NETWORK SECURITY
t v nagaraju Technical
174.9K views

5:13
Cryptographic Hash Function (CHF) in Cryptography || Network Security in Telugu
Lab Mug
18.5K views

6:53
Network security attacks in Hindi | Active attacks and Passive attacks in Network security in Hindi
QuickCS
1.2K views

9:59
VTU June 19 - Definition And Properties of Cryptographic Hash - Cryptographic And Network Security
Education
66 views

3:26
best eagle attacks | eagle attacks mountain goats | eagle attacks fox | eagle under water | eagle attacks | eagle | falcon
GIlgit Baltistan Adventure
20 views

7:53
Introduction to Hashing|Hashing in Data Strucutures|What is Hashing|Hash Table|Hash function
Scratch Learners
107.6K views

13:39
Introduction to Hashing in Data Structure | Hash Table, Hash Function | DSA using Java #56
ForMyScholars
27.2K views

26:41
What is HASHING ? | Why do we NEED it? | What is a Hash Function | (Example - Array vs Hash Table)
Simple Snippets
9.5K views

13:13
Hashing in Data Structure - Hashing in DSA - Hash Table - Hash Function - Collisions - Load Factor
Coding With Clicks
1.9K views

0:13
Euler function of 12 |phi function of 12 #Euler function #group #ringtheory #discretemathematics
Alpha Maths Academy
36.8K views

1:34
Hash Security, Pass-the-Hash, and PKI Explained | Security+ in 60 Seconds
Cyber Buddy
40 views

11:15
Security of MAC and HASH Function | Cryptography and Network Security
Ekeeda
3.3K views
![[HINDI] What is a Cryptographic Hash? | Hash Functions | Hashing v/s Encryption | Beginner's Guide](/image/i.ytimg.com/vi/qMemCPACnWw/xhqdefault.jpg.pagespeed.ic.G9pQ20ONPm.jpg)
12:21
[HINDI] What is a Cryptographic Hash? | Hash Functions | Hashing v/s Encryption | Beginner's Guide
Bitten Tech
35.7K views

27:54
CRYPTOGRAPHIC HASH FUNCTIONS in HINDI/URDU | , Secure Hash Algorithm | Birthday Paradox Attack
Shahzeb Khan Dasti
256 views

10:14
Bitcoin - Cryptographic hash function
Khan Academy
284.5K views

9:04
Message Digest and Digital Signature | Cryptographic Hash Function
saurabhschool
16.4K views

8:32
What is a Cryptographic Hash function?
Keifer Kif
1.4K views
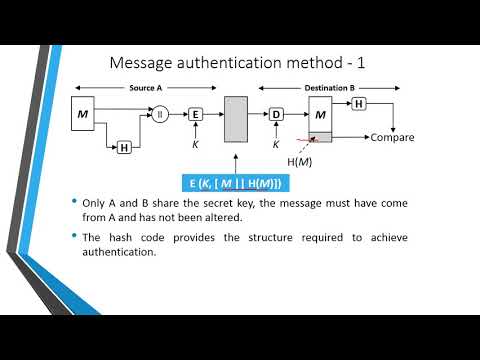
13:25
INS: Unit-5 Application of Cryptographic Hash function
Twinkal Patel
22.2K views
![Basics of Crypto Part 1 - Block (SHA256 Cryptographic Hash Function) [Compact]](/image/i.ytimg.com/vi/DELAC8fWOR8/hqdefault.jpg)
1:55
Basics of Crypto Part 1 - Block (SHA256 Cryptographic Hash Function) [Compact]
Unofficed
135 views

31:44
Cryptographic Hash Function
Internetwork Security
15.0K views
0:28
What is the function of a cryptographic hash? #crypto #quiz #marinaprotocol
StarkSpark
234 views

12:23
What is a Cryptographic Hash Function? | Where & How It Is Used In Crypto (Animated)
Cryptobie
1.1K views
7:36
Cryptographic Hash Function Explained | How it works? | Properties | Uses and Examples
JXploit
13.8K views
43:38
Lecture : 32 # Whirpool Cryptographic Hash Function
Learning Express
450 views

1:01
What is cryptographic hash function in crypto? Explained!! #crypto #cryptocurrency #bitcoin
Niyas Kp
16 views

0:39
Cybersecurity - Cryptography - What is the purpose of a cryptographic hash function?
TechThrillMatrix
65 views

8:56
11 Cryptographic Hash Function and its Properties: Pre-image, Second Pre-image, Collision Resistance
Dr Nitin Naik - Aston University, UK
29.5K views
44:36
Lecture : 29 #keyexchange Elliptic Curve Cryptography. Introduction to Cryptographic Hash Function
Learning Express
351 views
0:09
What is the function of cryptographic hash? #marinaprotocol #dailyquiz
Mining Tech Videos
117 views

0:26
(Answer) DAT/305 Week 3 — Apply — Cryptographic Hash Function
Grade One Essays
1 views

3:28
Cryptographic Hash Function - Applied Cryptography
Udacity
14.6K views

29:55
Cryptographic hash function: Introduction
Introduction to Cryptology
3.7K views

2:23
Cryptographic Hash Function Solution - Applied Cryptography
Udacity
2.5K views
45:47
An Introduction to Cryptographic Hash Function
Ravi Mittal
95 views

2:23
#22 - Cryptographic Hash Function | Blockchian Tutorial Series @FAMEWORLDEDUCATIONALHUB
FAME WORLD EDUCATIONAL HUB
83 views
1:05
#OneMinuteBlockchain Five Requirements of a Cryptographic Hash Function
The Blockchain Blog
90 views

1:01
Japan ramps up G7 security after attacks on prime minister
The Manila Times
311 views
Page 1 Next