Search Results for "routing through a network"
Find videos related to your search query. Browse through our collection of videos matching "routing through a network". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "routing through a network"
51 results found
7:08
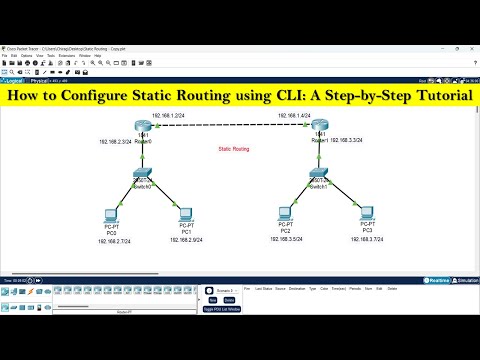
How to configure static routing using CLI | Static Routing configuration step by step
Chirag Bhalodia
134.3K views

0:07
Read Mathematical Aspects of Network Routing Optimization (Springer Optimization and Its Applications)
Gadarine
1 views
![[BTTH S6 Episode 141 ] Battle Through The Heavens Season 5 Episode 141 (btth) #southmovie #chinesemovie #hollywoodmoviesinhindi #bollywoodmovies #viralvideo #live #btths7 #BTTHS Battle Through The Heavens Season 5 Episode 64,65 Battle Through The Heaven](/image/s1.dmcdn.net/v/Y8yCu1e0HHwmKsqDs/xx720.pagespeed.ic.cYS7z_qZ1g.jpg)
17:15
[BTTH S6 Episode 141 ] Battle Through The Heavens Season 5 Episode 141 (btth) #southmovie #chinesemovie #hollywoodmoviesinhindi #bollywoodmovies #viralvideo #live #btths7 #BTTHS Battle Through The Heavens Season 5 Episode 64,65 Battle Through The Heaven
CREATIVE_CHRONICLES
1.1K views

10:43
Encryption Technique | Network Safety through Encryption | Protect Your Network | TechTalk Explorers
TechTalk Explorers
0 views
3:48
Secret Common Randomness from Routing Metadata in Ad-Hoc Networks
NS2 CODE
26 views

25:46
Kryptographie: Beyond Cryptographic Routing: Echo Protokoll & Era of Exponential Encryption |deutsch
Spot-On Encryption Suite Messenger
21 views

0:56
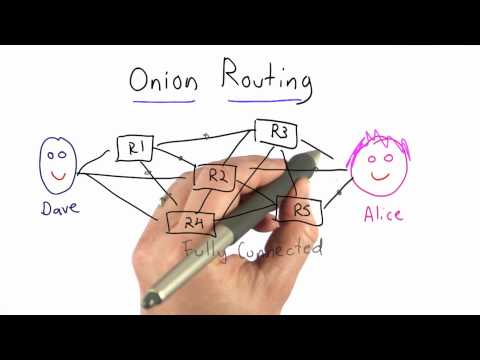
Onion Routing - Applied Cryptography
Udacity
814 views
4:08
Cryptographic Versus Trust-based Method s for MANET Routing Security
projectsnine
604 views

0:28
Onion Routing - Applied Cryptography
Udacity
742 views

21:17
DD Podcast Cryptography - Beyond Cryptographic Routing (english)
Spot-On Encryption Suite Messenger
22 views
1:52
Onion Routing - Applied Cryptography
Udacity
12.7K views

4:26
Energy-Efficient Reliable Routing Considering Residual Energy in Wireless Ad Hoc Networks
Ieeeprojectchennai
32 views

2:40
Invantive Web Service Rule-based Routing
invantive BV
25 views
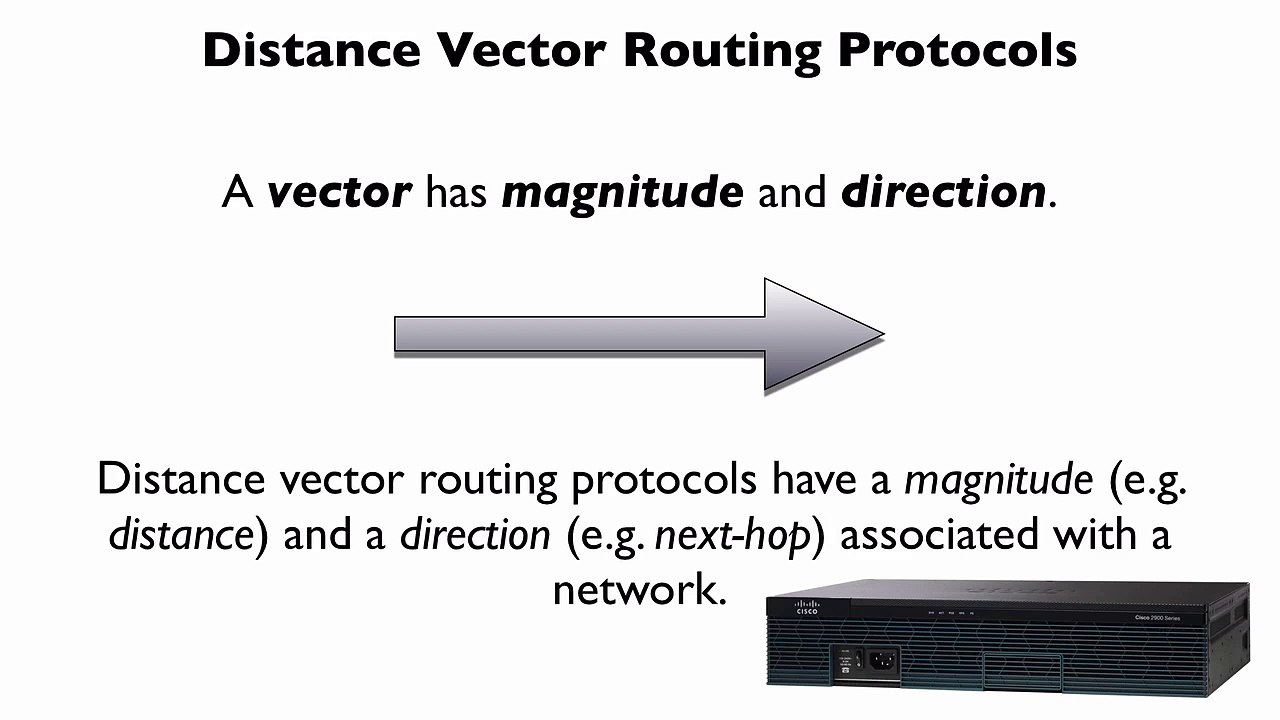
9:28
189.Distance Vector Routing Protocols
StudyNetworking
14 views

3:19
190.Link State Routing Protocols
StudyNetworking
11 views
4:06
Routing Protocols Using OMNeT++ Simulator output
Omnet-Manual
9 views
3:00
297.Metric in Routing Protocol
StudyNetworking
14 views
1:44
323.Routing Structures
StudyNetworking
10 views

0:27
Read Data Networks: Routing, Security, and Performance Optimization PDF Free
Fcosma
1 views

8:54
Creating Routing Components
Kira Kung
0 views

1:14
How To Find Bank Routing Number
Bank Routing Number Finder
73 views

7:06
OSPF Area Types| CISCO Certification |CCNA CCNP COURSE | Explained Step By Step | Packet Tracer |SPF LSA Routing Protocol Tutorial | Packet Tracer | cisco packet Tracer CISCO Certification |CCNA CCNP CCIE COURSE |
iEducation
20 views

14:18
Onion Routing - Computerphile
qwak1234
10 views

0:22
Routing Number on Check
ZilMoney
2 views

0:56
Onion Routing Solution - Applied Cryptography
Udacity
978 views

6:02
Network Security Model | Network security model in cryptography | Network Security
Chirag Bhalodia
22.5K views

14:06
CRYPTOGRAPHY AND NETWORK SECURITY NOTES | NETWORK SECURITY NOTES | NETWORK SECURITY
DIVVELA SRINIVASA RAO
382 views

8:25
Cryptography and Network Security Unit 1- Part 5 | Network Security & Network Access Security Models
TN55 RLE
442 views

45:59
01731, Network Steganography / Network Information Hiding, Chapter 7a Network-level Countermeasures)
Steffen Wendzel
812 views

23:56
What Is Network Security? | Introduction To Network Security | Network Security Tutorial|Simplilearn
Simplilearn
124.2K views

40:38
Cryptography in network (Network security basics) |Lecture 25| Data Communication & Computer Network
Mateen Yaqoob
58 views

1:55
Retina Network Security Scanner - Conficker Worm Serial - Retina Network Security Scanner - Conficker Wormretina network security scanner conficker worm (2015)
Jose Sanchez
2 views

6:33
What Is Network Marketing Network Marketing Explained! What Is Network Marketing Anyways
Most Popular Videos
1 views

11:37
What is Pi Network | Pi Network in Pakistan | Pi Network kya Hai | Pi Cryptocurrency Review in urdu
90s Mentor
25 views

7:54
Network Marketing Nedir, Neden Network Marketing, Network Marketing Gerçeği
musaduman
3 views

48:14
Learn English Through Stories Level 3 🔥 | Graded reader | Learn English Through Audio Podcast
English 5Days
990.4K views

21:20
สัประยุทธ์ทะลุฟ้าภาค 5 ตอนที่ 72 ซับไทย (Fights Break Sphere S5)斗破苍穹 72 #动漫嗨翻天 #斗破苍穹 #萧炎 #美杜莎 #炎鳞สัประยุทธ์ทะลุฟ้าภาค5 ซับไทย72 Battle through the heavens SS5#btth Battle Through the Heavens Season 5 Episode 72 English Sub -- sub indo - video Dailymotion
Candy Model
854 views

0:39
Greatness is achieved through service, not through self-promotion | The Power of Service | How to Achieve Greatness | The Secret to Success | The Importance of Giving Back | Find Your Purpose
Zubi Dot Com
2 views

29:03
Critical Infrastructure Network Attacks: Code Red, Alert Network Operators
RSA Conference
551 views

5:38
Network Layer In Computer Network | OSI Model | Networking Layers | Computer Networks | Simplilearn
Simplilearn
38.0K views

20:58
Network Information Hiding, Chapter 4 (Fundamentals of Network-based Information Hiding)
Steffen Wendzel
276 views

43:15
cryptography and network security || cryptography and network security bangla tutorial.
Online_learning_tube
229 views

4:27
NAS vs SAN - Network Attached Storage vs Storage Area Network
PowerCert Animated Videos
2.0M views

38:05
Network Security Tutorial | Introduction to Network Security
CRAW SECURITY
1.1K views

8:36
Network Security Model| Model of Network Security | Information and Cyber Security
T N V S PRAVEEN
292 views

42:46
RSA Algorithm in Cryptography and Network Security - UGC NET PYQs | NETWORK SECURITY - RSA ALGORITHM
Unify Study
4.6K views

39:52
Network Security | What is a network and reference model? | Great Learning
Great Learning
4.4K views

6:53
Network security attacks in Hindi | Active attacks and Passive attacks in Network security in Hindi
QuickCS
1.2K views

12:05
What is Network Security? | Types of Network Attacks | How these Attacks are done
Tech Guru Manjit
14.6K views

13:06
Steganography | network Security in tamil,#sscomputerstudies,#steganography,#network,#security
SS Computer Studies
1.5K views

5:36
On a road trip through South Africa: Route 62
DW (English)
720 views
Page 1 Next