Search Results for "one to one functions"
Find videos related to your search query. Browse through our collection of videos matching "one to one functions". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "one to one functions"
50 results found

9:06
Functions | Inverse Functions | Composite Functions | 2023 GCE Maths paper 1 question 15
GCSE Mathematics Zone
92.7K views

19:15
Hash Functions in hashing, Hashing in data structures, Types of hash functions, division method
CSIT Tutorials by KanyaKumari
4.5K views
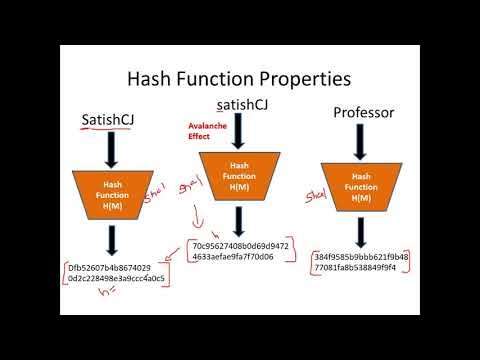
44:53
Introduction to Hash Functions and Application of Hash Functions in Cryptography - CSE4003
Satish C J
24.6K views

0:32
3 dynamic array functions you need to know. Who knew all three of these functions?! ✋🏼 #excel
Excel Dictionary
18.0K views

39:14
Python Functions Tutorial | Working With Functions In Python | Python Training | Edureka
edureka!
159.2K views

5:33
Inverse Trigonometric Functions - Functions
Saameer Mody
2 views

13:47
Relation and Functions Part 6 (Graphs of functions ) Mathematics CBSE Class X1
examfear
1 views

1:43
Inverse Trigonometric Functions - Algebra Functions
Saameer Mody
224 views

3:56
Inverse Trigonometric Functions - Composition of Functions
Saameer Mody
227 views

0:18
Linear functions have a constant rate of change and graph as Linear functions#amanyt #sirajshaikh#pw
Ravaan Tutorial
1.0K views

22:25
3.3.B: Cryptographic hashing from Strong One-Way function or One Way Functions (Or: Product ...
FOCS Conference
94 views

10:59
Discrete Math - 2.3.2 One-to-One and Onto Functions
Kimberly Brehm
270.2K views
1:06:45
Gravitation | NEET All PYQs 07: Gravitation | Physics | Physics NEET | Gravitation One Shot, Gravitation One Shot NEET PYQs, NEET PYQs Gravitation One Shot, Physics NEET PYQs Gravitation One Shot AK Sir, #AKSir #aksir #neet #neetphysics #physicsneet
sun ray
10 views

10:57
One Night Ending Explained | One Night Season 1 | One Night Australian Series | one night paramount
UlTiMaTe ChAnGe FoR LiFe
210 views

0:51
One way hash functions explained #shorts
Standard Edition Security
225 views

27:18
From One-Way Functions to Symmetric Key Encryption || @ CMU || Lecture 25c of CS Theory Toolkit
Ryan O'Donnell
745 views

32:39
Four* non-cryptographic hash functions enter. One leaves. by Adam Harvey
PyCon AU
852 views
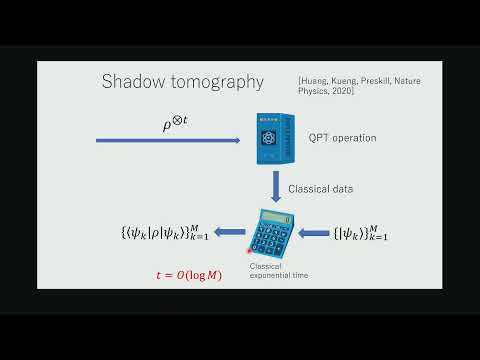
33:19
Introduction to Quantum Cryptography Without One-Way Functions
Simons Institute for the Theory of Computing
427 views

46:45
Capturing One-Way Functions via NP-Hardness of Meta-Complexity
Simons Institute for the Theory of Computing
589 views

42:52
Constant-Round Arguments from One-Way Functions
Simons Institute for the Theory of Computing
695 views
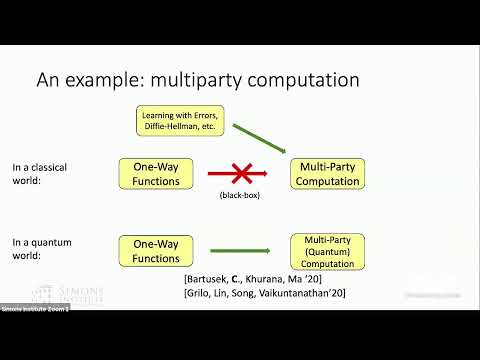
11:50
One-Way Functions Imply Secure Computation in a Quantum World
Simons Institute for the Theory of Computing
128 views

15:04
Lesson 14: One-way and hash functions (intypedia)
UPM
7.9K views

42:13
Cryptography Mathematics | Lecture 1 | One way functions | RSA Encryption #Hindi
Mathsmerizing
1.6K views

55:26
Tomoyuki Morimae - Quantum cryptography without one-way functions
Quantum Information @ RUB
236 views

37:31
Five* non-cryptographic hash functions enter. One hash function leaves.
Linux.conf.au 2016 -- Geelong, Australia
4.7K views

9:08
Custom one hot encoding | one hot encoding without any library | one hot encoder without sklearn
Hope In Data Science
112 views

7:04
G.One & Ra.One In Action | RA.One | Shah Rukh Khan
Eros Now Music
119.0M views
8:29
Latest Android-One smartphone ⚡⚡| Cheapest budget android-One smartphone #android #android-one #stock-android
AB Multimedia
37 views

1:37:20
One Night, One Baby, One Forever
Short TZ
991 views
3:55
One Man -- One Woman -- One Person by Sheikh Tawfique Chowdhury
Rehan Ahmed
272 views

1:48:06
One Night, One Mistake, One Forever
Shortmovies68
340 views

0:33
How Cryptographic Hash Functions Keep You Safe! 🔍 #cryptocurrency #bitcoin #blockchain #shorts
Cryptocurrency Classroom
94 views

49:40
Low-Complexity Cryptography and Simple Hard-to-Learn Functions
Simons Institute for the Theory of Computing
436 views
![[Chapter 2a] Cryptography II + Hash Functions & Wordlists](/image/i.ytimg.com/vi/-lCGZIPeExI/xhqdefault.jpg.pagespeed.ic.QXc4mtbpKC.jpg)
2:16:21
[Chapter 2a] Cryptography II + Hash Functions & Wordlists
Avocado
5.9K views

22:07
Oblivious Pseudorandom Functions from Isogenies
IACR
1.2K views

7:27
Hash Functions 🔥🔥
Perfect Computer Engineer
159.9K views

17:05
Basics of Cryptology – Part 20 (Cryptanalysis – Cost & Fitness Functions - Language Models)
Cryptography for Everybody
802 views

2:36
What is Hashing? Hash Functions Explained Simply
Lisk
440.5K views
![[CompNetSec] - 13 - Cryptographic Hash Functions](/image/i.ytimg.com/vi/2yxHePuitJc/hqdefault.jpg.pagespeed.ce.bngtY8SLsy.jpg)
1:00:43
[CompNetSec] - 13 - Cryptographic Hash Functions
Hicham Elmongui
7.3K views

26:57
CH3 Cryptographic Hash Functions 1
د محمود-الحاسبات وتقنية المعلومات
293 views

14:13
#4 Why do we need cryptography hash functions SHA256 for blockchain network?
FuTech
274 views

10:54
PBKDF2 - Password Based Key Derivation Functions in .NET
Stephen Haunts (Coding in the Trenches)
11.3K views

11:35
Limits of multivariable functions
Prime Newtons
59.1K views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

30:06
14.1: Functions of Several Variables
Alexandra Niedden
205.8K views

10:28
Module 5.2 Message Authentication Functions
bushara abdulrahim
2.9K views

10:30
Introduction to HASHING in Data Structures || Hash Functions,Hash Table, Hash Keys,Hash Values in DS
Sundeep Saradhi Kanthety
11.5K views

0:56
Cryptographic Hash Functions
Mathematical Minutes
46 views

11:54
computability theory 2 Generating Computable Functions
mohamed eldosuky
420 views

6:08:55
Steganography (Forensics Session 2) - Coding for Hacking (C Functions)
theshyhat
556 views
Page 1