Search Results for "message authentication code based on hash function"
Find videos related to your search query. Browse through our collection of videos matching "message authentication code based on hash function". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "message authentication code based on hash function"
50 results found

12:00
Hash Function in cryptograhy | Properties of Hash Function | Simple Hash Function Technique
Chirag Bhalodia
107.9K views

14:52
Applications of Hash Function | Purpose of Hash Function | Real Time Application of Hash Function
Chirag Bhalodia
32.1K views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

7:40
Hash function based on CBC in cryptography | Hash function based on cipher block chaining
Chirag Bhalodia
24.0K views

9:00
Hash Functions || hash function algorithm || hash function cryptography || hashing vs encryption
The Ecomly Tech
24 views

9:01
Message Authentication Code (MAC) in Cryptography Hash Function || Network Security in Telugu
Lab Mug
14.3K views

11:49
Authentication functions and 3 ways to produce authentication | Message authentication
Abhishek Sharma
263.4K views

20:58
16-HMAC Algorithm Explained 🔐 | Hash-Based Message Authentication Code in Network Security
Sundeep Saradhi Kanthety
168.4K views

1:05
gods message| message from god| god's message for me today| god's final message| god's message today
God heal us
2 views

32:24
public key encryption: Key distribution, message Authentication and hash function- part1
Dr. Moonther
384 views

10:30
Introduction to HASHING in Data Structures || Hash Functions,Hash Table, Hash Keys,Hash Values in DS
Sundeep Saradhi Kanthety
11.5K views

0:13
Hash Oil,buy Hash oil online,Hash oil for sale,Prefilled hash oil cartridges for sale http://dabstarshop.com
dabstarshop dabstarspharmacy
1 views

8:19
LEC11| Blockchain | Cryptographic Hash Function & Properties of Hash Function by Mrs. G. Sowmya
MLID - MLR Institute of Technology
2.3K views

9:32
Hash function Keya hai? hashing Algorithm? password hashing? password and hash function Hindi
Technical Haroon
8.1K views
0:09
Function | Definition of function | define function | simple definition of function
Tartull education
23.4K views

2:20
Hash Based Message Authentication
Udacity
59.1K views

6:33
HMAC explained | keyed hash message authentication code
Jan Goebel
85.3K views

9:37
Introduction of Message Authentication Code (MAC) | Application of MAC | Cryptographic MAC Function
Chirag Bhalodia
31.5K views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

1:04:39
Message authentication and hash functions (part-1)
Keerthi Humsika K
58 views

16:37
Message Authentication using Hash Functions - Network Security
Lectures by Shreedarshan K
4.3K views

40:57
13-Message Authentication in Cryptography 🔐 | MAC vs Hash Functions vs Encryption
Sundeep Saradhi Kanthety
234.7K views

12:55
Types of Message Authentication | Message Encryption | Part 1 | Network Security | Hindi Urdu
Ask Faizan
4.3K views

7:53
Introduction to Hashing|Hashing in Data Strucutures|What is Hashing|Hash Table|Hash function
Scratch Learners
107.6K views

13:39
Introduction to Hashing in Data Structure | Hash Table, Hash Function | DSA using Java #56
ForMyScholars
27.2K views

26:41
What is HASHING ? | Why do we NEED it? | What is a Hash Function | (Example - Array vs Hash Table)
Simple Snippets
9.5K views

13:13
Hashing in Data Structure - Hashing in DSA - Hash Table - Hash Function - Collisions - Load Factor
Coding With Clicks
1.9K views

13:18
Introduction to Cryptographic Hash Function| Merkel Damgard Scheme | SHA-256 | Secure Hash Algorithm
Muhammed Mustaqim
607 views

37:31
Five* non-cryptographic hash functions enter. One hash function leaves.
Linux.conf.au 2016 -- Geelong, Australia
4.7K views

0:13
Euler function of 12 |phi function of 12 #Euler function #group #ringtheory #discretemathematics
Alpha Maths Academy
36.8K views

9:04
Message Digest and Digital Signature | Cryptographic Hash Function
saurabhschool
16.4K views

12:56
CMAC Explained: A Deep Dive into Cipher-based Message Authentication
Network Technician
6 views

7:40
MAC Based on Hash Function | HMAC in network security
Chirag Bhalodia
67.7K views

13:01
Message Authentication Code MAC
Ekeeda
284 views

14:41
MAC in Cryptography || Message Authentication Code in Cryptography and network security
Abhishek Sharma
396.9K views

1:01
Cryptography - MAC - Message Authentication Code #cryptography
Alon Lalezari - אלון ללזרי
1.2K views

7:13
#35 MAC ( Message Authentication Code ) - Working and Significance |CNS|
Trouble- Free
223.0K views

11:49
Network Security - Message Authentication Code (MAC) | Cryptography and Network Security
Lectures by Shreedarshan K
2.5K views

13:01
Message Authentication Code MAC | Cryptography and Network Security
Ekeeda
253 views

18:43
Message Authentication Code -16
Cryptography
445 views

19:48
Message Authentication Code | Online Education | Learn Online
Education Online
5 views

1:21
16. Message Authentication Code MAC
Cybersecurity at St. Cloud State University
28.5K views

0:18
What is a MAC (Message Authentication Code)?
Intelligence Gateway
690 views

29:42
Message Authentication Code (MAC) and HMAC - Cryptography - Cyber Security CSE4003
Satish C J
37.3K views

2:31
MAC (message authentication code ) in cryptography network system
kysupportdev
7.0K views

8:08
MAC in Hindi - Message Authentication Code Process, Significance, HMAC Concept
Easy Engineering Classes
111.9K views

2:24
Network Security and Cryptography: Message Authentication Code(MAC)
OnlineTeacher
598 views

20:53
MAC in Cryptography || Message Authentication Code in Network Security And Cryptography.
Anas Khan
192 views

3:24
MAC (Message Authentication Code) | Unit 4 Cryptography and Cyber Security CB3491 | Anna University
CSE IT Exam Preparation
1.1K views
2:31
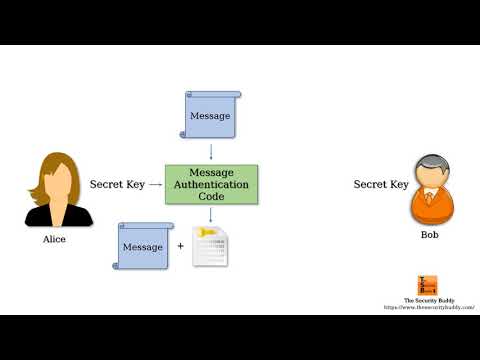
What is a Message Authentication Code (MAC)?
The Security Buddy
27.8K views
Page 1