Search Results for "ktu s8 cs"
Find videos related to your search query. Browse through our collection of videos matching "ktu s8 cs". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "ktu s8 cs"
50 results found

55:35
Cryptography and Network Security Part 4/5 | WIlliam Stallings |Secure communication - S8 EC, CS,KTU
bushara abdulrahim
498 views

9:44
IDEA - International Data Encryption Algorithm - Basic Structure (KTU CSE 409 Cryptography-Module 2)
KTU Computer Science Tutorials
6.0K views
23:57
Advanced Encryption Standard(AES)-Mix Column Transformation- (KTU CSE 409 Cryptography-Module 2)
KTU Computer Science Tutorials
4.1K views

3:36
Module 4.3 Requirements of Public key cryptosystems|S8 ECE|SECURE COMMUNICATION KTU|ECT434
bushara abdulrahim
2.4K views

8:47
Block Cipher - Data Encryption Standard | S7 | KTU | CSE | Cryptography and Network Security
Merin David's Lecture Notes
2.7K views

9:51
Substitution Ciphers-PlayFair Cipher-Part 2(KTU CSE 409 Cryptography-Module 1)
KTU Computer Science Tutorials
4.7K views

14:08
Attacks-Malicious Code-Brute Force(KTU CS 472 Principles of Information Security-S8CS-Mod 1 Part 6)
KTU Computer Science Tutorials
1.3K views
13:31
Turing Machine (TM) | CST301 | FLAT MODULE 5 | KTU | Anna Thomas | SJCET
Anna Thomas
29.2K views
9:41
Substitution Cipher-Playfair Cipher-KTU CST433 Security in Computing-S7CS -Mod 1-Part 5
KTU Computer Science Tutorials
3.0K views

11:35
Module 4.1 Public key cryptosystems|S8 ECE|SECURE COMMUNICATION KTU|ECT434#engineering #ktutuition
bushara abdulrahim
4.5K views
5:48
AES Algorithm | Cryptography | Malayalam Lecture | KTU
KTU Engineering Malayalam Lectures
22.0K views

9:58
Symmetric Cipher: Substitution (Numericals) | S7 | KTU | CSE | Cryptography and Network Security
Merin David
1.8K views

10:48
Module 5.3_Message Authentication Code,Secure communication ktu s8 ec #engineering #ktutuition
bushara abdulrahim
2.3K views

48:22
Cryptography and Network Security Part 3/5 | WIlliam Stallings |Secure communication - S8 EC, CS,KTU
bushara abdulrahim
490 views
11:45
Cryptanalysis-Types-KTU CST433 Security in Computing-S7CS Elective-Module 1-Part 2
KTU Computer Science Tutorials
3.9K views

18:45
Key Management - IPSEC ( KTU CSE 409 Cryptography & Network Security - Module 5)
KTU Computer Science Tutorials
4.0K views
20:23
Cryptography-Symmetric Cipher Model-KTU CST433 Security in Computing-S7CS Elective-Module 1-Part 1
KTU Computer Science Tutorials
7.2K views

8:19
Kerberos: Realm, Difference between Version 4 and 5 | CST409 | NSP MODULE 1 |KTU| Anna Thomas |SJCET
Anna Thomas
5.5K views

32:45
IDEA Encryption Algorithm(Cryptography & Network Security, KTU)
kiran baby
6.8K views

1:35:57
Cryptography and Network Security Part 1/5 | WIlliam Stallings | Secure communication - S8 EC KTU
bushara abdulrahim
1.3K views

24:42
Field-GF(2^n) (KTU CST332 Foundations of Security in Computing-S6CS-Mod 1-Part 13)
KTU Computer Science Tutorials
2.1K views
25:21
RSA Algorithm With Example ( Asymmetric Encryption- KTU CSE 409 - Cryptography - Module 3)
KTU Computer Science Tutorials
11.4K views

9:21
KTU || EC 407 COMPUTER COMMUNICATION || MODULE VI || NETWORK ATTACKS || LECTURE 18
Nandu V S
14.1K views
15:19
Substitution Cipher-Polyalphabetic-Vigenere-KTU CST433 Security in Computing-S7CS -Mod 1-Part 4
KTU Computer Science Tutorials
3.3K views

4:18
Symmetric Cipher: Transposition (Numericals) | S7 | KTU | CSE | Cryptography and Network Security
Merin David's Lecture Notes
830 views
13:55
Secure Sockets Layer (SSL)-Introduction-Part 1 (KTU CSE 409 Cryptography-Module 6)
KTU Computer Science Tutorials
8.6K views

12:49
FLAT|Module 1|KTU S5 CSE |CST 301|Introduction to Formal languages and automata theory|#cst301#flat
C-TECH
9.2K views

12:59
Equivalence of PDA and CFG: CFG to PDA | CST301 | FLAT MODULE 4 | KTU | Anna Thomas | SJCET
Anna Thomas
25.1K views

12:00
Symmetric Cipher: Substitution | S7 | KTU | CSE | Cryptography and Network Security
Merin David
3.6K views

12:23
IDEA Algorithm | Cryptography | Malayalam Lecture | KTU
KTU Engineering Malayalam Lectures
7.8K views
11:22
Secure Electronic Transaction (SET)-Introduction-Part 1(KTU CSE 409 Cryptography -Module 6)
KTU Computer Science Tutorials
8.8K views
6:38
Euclidean Algorithm Problems (KTU CSE 409 - Cryptography And Network Security - Module 3)
KTU Computer Science Tutorials
3.1K views
21:55
Key Management-Distribution of Public Keys-Part 2(KTU CSE 409 Cryptography Network Security Module3)
KTU Computer Science Tutorials
2.5K views
8:05
Transport Layer Security(TLS)- (KTU CSE 409 Cryptography-Module 6)
KTU Computer Science Tutorials
5.0K views

3:57
Module 4.2 Applications of Public key cryptosystems|S8 ECE|SECURE COMMUNICATION KTU|ECT434
bushara abdulrahim
2.6K views

15:45
Scheduling Algorithms in RTOS Quick Revision| KTU S6 RTOS
Easy Electronics
18.1K views

10:32
Substitution Ciphers-Vernam Cipher-One Time Pad-Part 5(KTU CSE 409 Cryptography-Module 1)
KTU Computer Science Tutorials
3.1K views
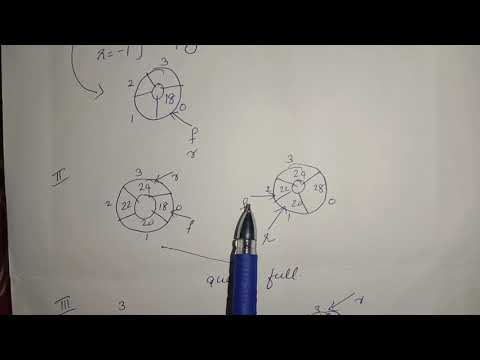
11:41
Problems on Fermat's Theorem ( KTU CSE 409 - Cryptography - Module 3)
KTU Computer Science Tutorials
7.7K views

5:56
Key Exchange using ECC-KTU CST433 Security in Computing S7CS - Mod 3 Part 17
KTU Computer Science Tutorials
1.3K views
20:01
Payment Processing-Secure Electronic Transaction (SET)-Part 4 (KTU CSE 409 Cryptography-Module 6)
KTU Computer Science Tutorials
5.3K views

24:03
Substitution Cipher-Caeser-Monoalphabetic-KTU CST433 Security in Computing-S7CS -Mod 1-Part 3
KTU Computer Science Tutorials
4.1K views

24:17
Substitution Ciphers-Caesar Cipher-Monoalphabetic Ciphers-Part 1(KTU CSE 409 Cryptography-Module 1)
KTU Computer Science Tutorials
7.7K views

21:04
Symmetric Cipher Model-Introduction-Part 1 (KTU CSE 409 Cryptography-Module 1)
KTU Computer Science Tutorials
7.4K views
14:40
Circular Queue -Data structure S3 KTU
Computer Science Lectures
10.5K views

25:29
Substitution Ciphers-Hill Cipher-Part 3(KTU CSE 409 Cryptography-Module 1)
KTU Computer Science Tutorials
4.6K views
25:24
Substitution Cipher-Hill Cipher-With Example-KTU CST433 Security in Computing-S7CS -Mod 1-Part 6
KTU Computer Science Tutorials
3.4K views

14:19
Conversion of FA to RE: State Elimination Method | CST301 | FLAT MODULE 2 | KTU | Anna Thomas |SJCET
Anna Thomas
32.0K views

11:41
Problems on Fermat's Theorem KTU CST332 Foundations of Security in Computing-S6CS
KTU Computer Science Tutorials
2.2K views

37:29
Cryptography and Network Security Part 5/5 | WIlliam Stallings |Secure communication - S8 EC, CS,KTU
bushara abdulrahim
325 views

6:04
Rotor Machines and Steganography | S7 | KTU | CSE | Cryptography and Network Security
Merin David's Lecture Notes
5.5K views
Page 1