Search Results for "injective functions"
Find videos related to your search query. Browse through our collection of videos matching "injective functions". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "injective functions"
50 results found

17:15
INJECTIVE, SURJECTIVE, and BIJECTIVE FUNCTIONS - DISCRETE MATHEMATICS
TrevTutor
1.2M views

0:58
Injective, Surjective and Bijective function.|One-One and Onto function.|@vmatics444
V Matics
103.2K views

9:06
Functions | Inverse Functions | Composite Functions | 2023 GCE Maths paper 1 question 15
GCSE Mathematics Zone
92.7K views

19:15
Hash Functions in hashing, Hashing in data structures, Types of hash functions, division method
CSIT Tutorials by KanyaKumari
4.5K views

0:18
Linear functions have a constant rate of change and graph as Linear functions#amanyt #sirajshaikh#pw
Ravaan Tutorial
1.0K views

12:12
9 Statistical functions in Excel you need to know | Excel Functions
Excel Tutorial
3.2K views
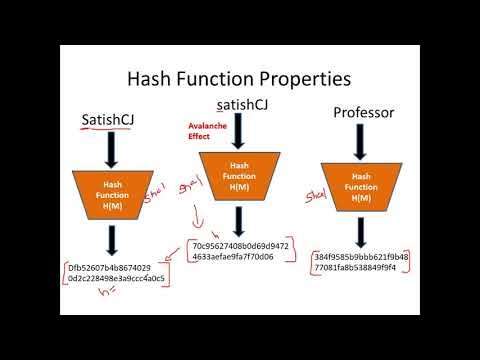
44:53
Introduction to Hash Functions and Application of Hash Functions in Cryptography - CSE4003
Satish C J
24.6K views

0:32
3 dynamic array functions you need to know. Who knew all three of these functions?! ✋🏼 #excel
Excel Dictionary
18.0K views

39:14
Python Functions Tutorial | Working With Functions In Python | Python Training | Edureka
edureka!
159.2K views

13:47
Relation and Functions Part 6 (Graphs of functions ) Mathematics CBSE Class X1
examfear
1 views

3:56
Inverse Trigonometric Functions - Composition of Functions
Saameer Mody
227 views

1:43
Inverse Trigonometric Functions - Algebra Functions
Saameer Mody
224 views

5:33
Inverse Trigonometric Functions - Functions
Saameer Mody
2 views

1:00
Using Python Dictionaries to Represent Functions #short
andrew octopus
239 views

0:33
How Cryptographic Hash Functions Keep You Safe! 🔍 #cryptocurrency #bitcoin #blockchain #shorts
Cryptocurrency Classroom
94 views

0:48
OneNote Math Function Creates Sliders to Explore Functions with Ease
The Resourceful Teacher IRL
109 views

49:40
Low-Complexity Cryptography and Simple Hard-to-Learn Functions
Simons Institute for the Theory of Computing
436 views
![[Chapter 2a] Cryptography II + Hash Functions & Wordlists](/image/i.ytimg.com/vi/-lCGZIPeExI/hqdefault.jpg)
2:16:21
[Chapter 2a] Cryptography II + Hash Functions & Wordlists
Avocado
5.9K views

53:38
Verifiable Random Functions and Their Relation to Identity-Based Encryption -1
Mathnet Korea
355 views

0:51
One way hash functions explained #shorts
Standard Edition Security
225 views

0:37
Weak Hash Functions are a SECURITY RISK!
World Economic and Cryptocurrency News
1.1K views

5:31
#54 S/MIME - Secure MIME protocol - Functions, Services |CNS|
Trouble- Free
215.2K views

22:07
Oblivious Pseudorandom Functions from Isogenies
IACR
1.2K views

10:03
Cryptography Hashing functions SHA and specificaly SHA1 hashing
Alon Lalezari - אלון ללזרי
11 views

1:00
Functions Simplified for Absolute Beginners! Learn to Code Fast
Error Makes Clever
135.3K views

7:27
Hash Functions 🔥🔥
Perfect Computer Engineer
159.9K views

0:51
Hash Functions
Gnana Lakshmi T C
149 views

12:08
Graphing Polynomial Functions Using End Behavior, Zeros, and Multiplicities
Mario's Math Tutoring
469.5K views

17:05
Basics of Cryptology – Part 20 (Cryptanalysis – Cost & Fitness Functions - Language Models)
Cryptography for Everybody
802 views

1:37:06
Calculus 1 Lecture 0.2: Introduction to Functions.
Professor Leonard
1.2M views
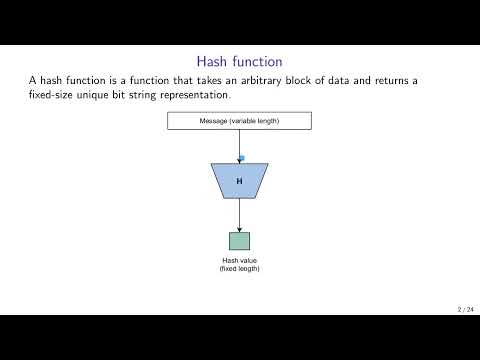
57:46
Applied Cryptography: 3. Hash functions and HMAC
Applied Cryptography by University of Tartu
635 views

13:37
Exam Functions Grade 10
Kevinmathscience
412.3K views

13:44
V3a: Hash functions: Fundamental concepts (Applied Cryptography 101)
Cryptography 101
1.0K views

26:38
Functions | IGCSE Maths 0580
Croizone Math
976 views
14:18
Functions
The Organic Chemistry Tutor
1.2M views

2:36
What is Hashing? Hash Functions Explained Simply
Lisk
440.5K views
![[CompNetSec] - 13 - Cryptographic Hash Functions](/image/i.ytimg.com/vi/2yxHePuitJc/hqdefault.jpg)
1:00:43
[CompNetSec] - 13 - Cryptographic Hash Functions
Hicham Elmongui
7.3K views

2:52
Universal Computable Functions
Obsidian Student Explanations
125 views
2:29
Generating Computable Functions Pt. 2
Obsidian Student Explanations
33 views
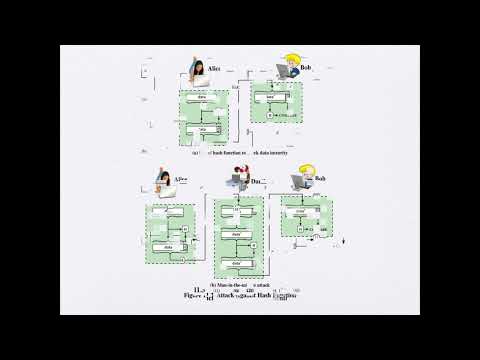
26:57
CH3 Cryptographic Hash Functions 1
د محمود-الحاسبات وتقنية المعلومات
293 views
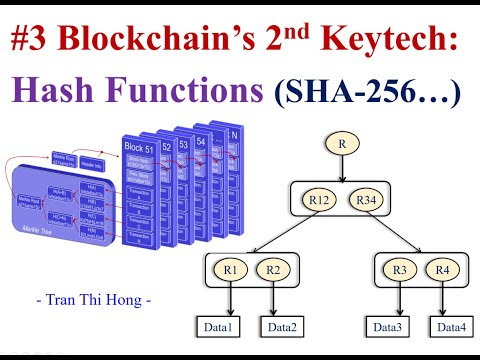
14:13
#4 Why do we need cryptography hash functions SHA256 for blockchain network?
FuTech
274 views
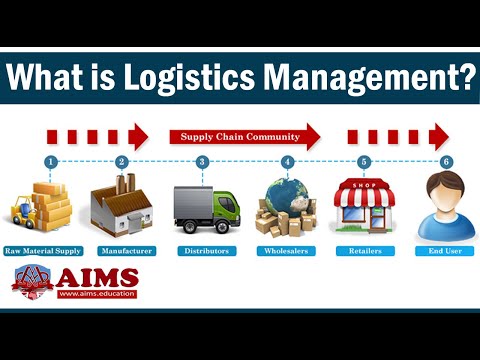
8:52
What is Logistics Management? Meaning, Basic Functions, Examples & Strategies| AIMS Education
AIMS Education
2.8M views

10:54
PBKDF2 - Password Based Key Derivation Functions in .NET
Stephen Haunts (Coding in the Trenches)
11.3K views
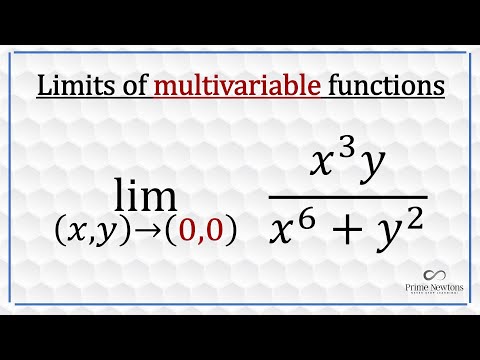
11:35
Limits of multivariable functions
Prime Newtons
59.1K views

56:32
New Approaches for Building Cryptographic Hash Functions
Microsoft Research
114 views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

30:06
14.1: Functions of Several Variables
Alexandra Niedden
205.8K views
11:34
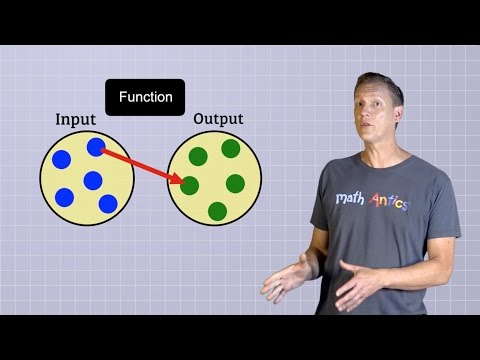
Algebra Basics: What Are Functions? - Math Antics
mathantics
3.6M views
18:19
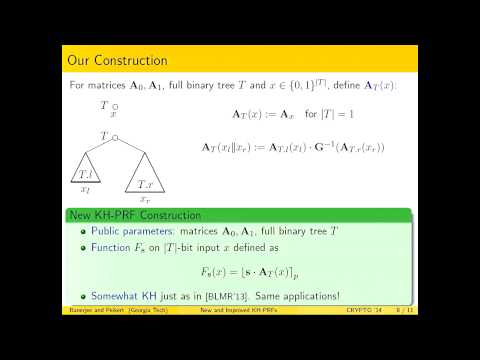
New and Improved Key-Homomorphic Pseudorandom Functions
IACR
612 views

24:26
Chosen-Ciphertext Security from Slightly Lossy Trapdoor Functions.
IACR
465 views