Search Results for "hmac requires 1 key"
Find videos related to your search query. Browse through our collection of videos matching "hmac requires 1 key". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "hmac requires 1 key"
52 results found

6:28
Key Of The Kaaba History In Urdu | key of kaaba family | kaaba,key of kaaba,key of the kaaba history in urdu,key of kaaba history,key of kaaba history in urdu,history of khana kaba,key of kaaba history in english,amazing history of key of khana kaaba
Knowldge Factory
10 views

0:39
sbb key programmer review,Sbb Key Programmer,sbb car key programmer,sbb key programmer v33 manual,sbb key programmer v33,key programmer sbb
lara-baby
8 views

0:35
Key west florida accommodations, key west vacation rentals, key west condos, key west hideaways, key west nightlife
Tommy Lee
57 views

0:54
"Operationally, computing power is the biggest issue. It requires optimizing all these resources"
Beryl Elites
1.5K views

2:50
Proving P=NP Requires Concepts We Don't Have | Richard Karp and Lex Fridman
Lex Clips
61.9K views

0:09
Cyber Security Which of the following cryptography methods requires both public and private keys for
Trivia Quiz App general knowledge & programming
31 views

17:15
Why Quantum Computing Requires Quantum Cryptography
PBS Space Time
459.6K views

1:22
Sunny Leone: 'There is nothing in Jackpot which requires censorship'
Movie Talkies
9 views

2:19
Diverse storytelling requires authenticity
DW (English)
1 views

3:33
Saifuddin: Addressing foreign control over vegetable supply chain requires comprehensive solutions
The Star
215 views

59:28
Learning is endless and requires self-discipline
FreeDramaTV
254 views
0:39
Elon Musk Backs California's AI Regulation Bill That Requires Developers to Implement Safeguards
Benzinga
714 views

1:54
The Farmer's Bride Requires Care! Part 1: Angel Descends | movie | 2021 | Official Trailer
JustWatch
244 views
![Cultivating Immortality Requires a Rich Lady Episode 1-10 [ENG SUB]](/image/s2.dmcdn.net/v/VCRTt1enJ-A-YDUT9/x720)
1:02:10
Cultivating Immortality Requires a Rich Lady Episode 1-10 [ENG SUB]
REvive Anime
755 views

9:55
what is symmetric key cryptography and asymmetric key cryptography , public key and private key
sawji gyaan
10 views

3:55
difference between public key and private key, what is public key and private key, o level exam,
tech MCQ & theory
3.4K views

2:55
The difference between Private key and public Key || Symmetric key and Asymmetric key cryptography
Pooja Patel
10 views

3:11
Public key vs Private key ll Symmetric key vs Asymmetric key
Guptasmartclasses
38 views

6:57
Key Management and Key Distribution in Cryptography | Key Management | Key Distribution
Chirag Bhalodia
100.9K views

0:48
°FIFA 14° °KEYGEN°°KEY GENERATOR°°ACTIVATION°°PRODUCT KEY°°SERIAL KEY°°LICENCE KEY
morientesmalaka
241 views

3:17
Best Key West Restaurants | Best Key West Nightclubs | Best Key West DJs | Whats Hot Key West
LJ Cange
1 views

1:10
Magic Key Extractor Key Gen (Magic Key Extractormagic key extractor 2015)
Brenda Diaz
27 views
![Mirrakey License Key Generator Key Gen [Mirrakey License Key Generatormirrakey license key generator 2015]](/image/s2.dmcdn.net/v/8_ZGQ1e0GZW5oh8l_/xx720.pagespeed.ic.P1ZMrUV2OK.jpg)
1:50
Mirrakey License Key Generator Key Gen [Mirrakey License Key Generatormirrakey license key generator 2015]
Bob Sanderson
6 views

1:00
Key locksmith Dubai, key repairing, key making, key locksmith, locksmith Dubai
Ummeammarah11
2 views
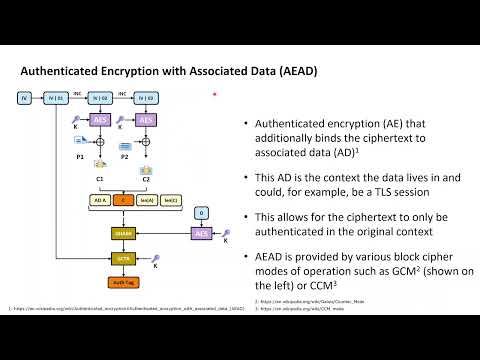
12:51
Cryptography with Python 30: HMAC, Encrypt-then-MAC and GCM
Cyrill Gössi
1.1K views
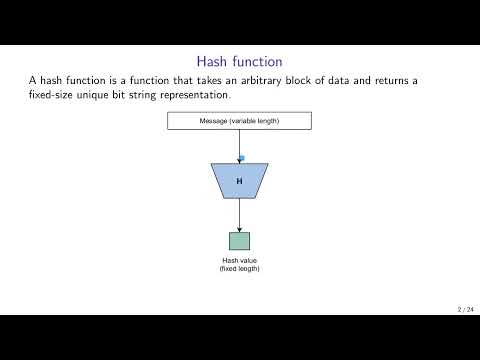
57:46
Applied Cryptography: 3. Hash functions and HMAC
Applied Cryptography by University of Tartu
635 views

8:08
MAC in Hindi - Message Authentication Code Process, Significance, HMAC Concept
Easy Engineering Classes
111.9K views
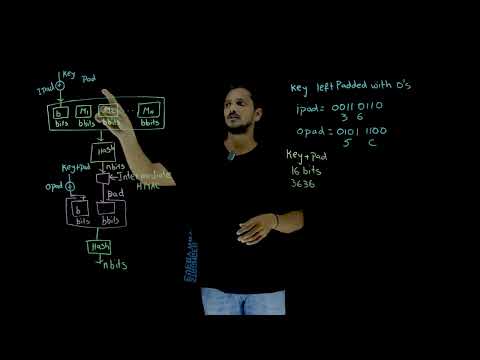
5:15
HMAC Nested MAC Method || Lesson 73 || Cryptography || Learning Monkey||
Wisdomers - Computer Science and Engineering
1.1K views

1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views
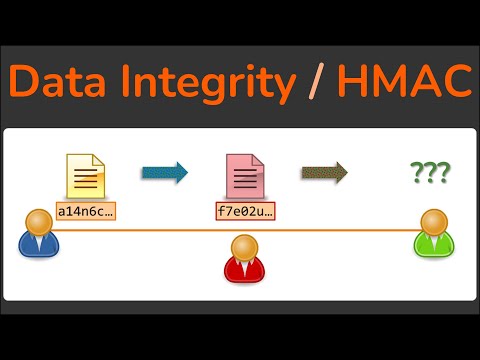
7:24
Data Integrity - How Hashing is used to ensure data isn't modified - HMAC - Cryptography
Practical Networking
77.9K views
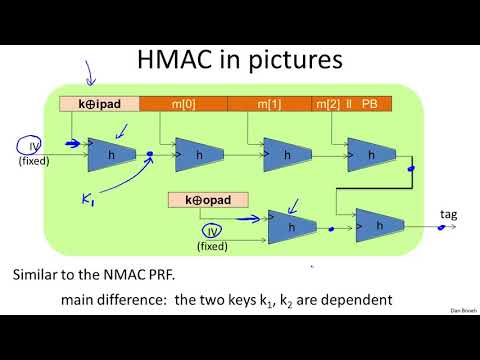
7:05
HMAC - Cryptography I
Nguyen Duong Anh
80 views

11:03
Learn the ART of CRYPTOGRAPHY - SHA-1 HMAC Hashing Explained (Urdu/Hindi)
Cybersecurity Academy - CertificationHUB
184 views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

12:48
Função de Hash - MD5 e SHA - Código HMAC - Aula completa
Prof. Sergio Villarreal
3.7K views

8:10
#36 HMAC (Hash Based) & CMAC (Cipher Based) |CNS|
Trouble- Free
232.6K views

9:40
Message Authentication Codes: CMAC and HMAC
Cihangir Tezcan
4.8K views
1:09:59
Go UUID HMAC
Learn To Code
945 views

6:33
HMAC explained | keyed hash message authentication code
Jan Goebel
85.3K views

29:42
Message Authentication Code (MAC) and HMAC - Cryptography - Cyber Security CSE4003
Satish C J
37.3K views
10:26
Razorpay integration in asp.net web app | HMac SHA256 signature create and matching
New Arts
1.4K views
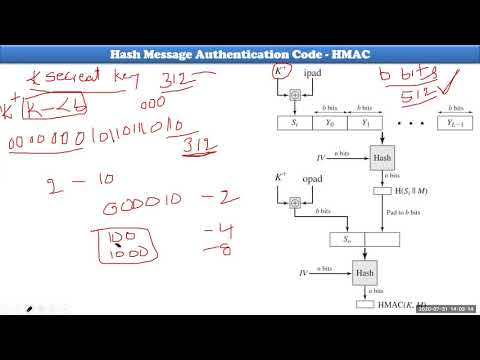
22:00
CNS HMAC
Kallam Gopala Reddy
312 views
20:58
16-HMAC Algorithm Explained 🔐 | Hash-Based Message Authentication Code in Network Security
Sundeep Saradhi Kanthety
168.4K views
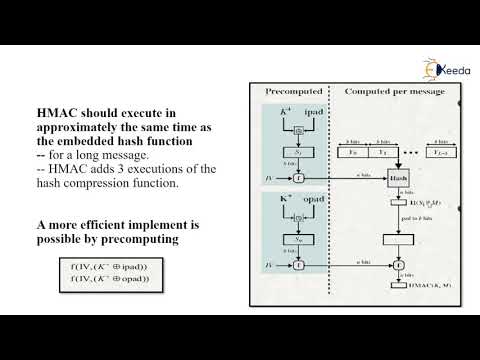
20:35
HMAC | Cryptography and Network Security
Ekeeda
677 views

6:09
HMAC & Message Authentication Codes (MACs) - Why Hashing alone is NOT ENOUGH for data integrity
JayPMedia
6.7K views

7:40
MAC Based on Hash Function | HMAC in network security
Chirag Bhalodia
67.7K views

13:49
V4b: CBC-MAC and HMAC (Applied Cryptography 101)
Cryptography 101
1.1K views

11:19
MAC function ,HMAC,CMAC in Cryptography and cyber security tamil||CCS||Anna university reg-2021.
Murugan Tech World
7.8K views

9:00
HMAC and CMAC in Cryptography Hash Function || Network Security in Telugu
Lab Mug
10.9K views

9:24
Securing Stream Ciphers (HMAC) - Computerphile
Computerphile
326.5K views

0:46
HMAC Promo take 2
Players 2Pros
29 views
![Cultivating Immortality Requires a Rich Lady Episode 1-10 [ENG SUB]](/image/s2.dmcdn.net/v/VCRTt1enJ-A-YDUT9/x720)
1:02:10
Cultivating Immortality Requires a Rich Lady Episode 1-10 [ENG SUB]
REvive Anime
755 views

1:54
The Farmer's Bride Requires Care! Part 1: Angel Descends | movie | 2021 | Official Trailer
JustWatch
244 views
Page 1 Next