Search Results for "hmac function"
Find videos related to your search query. Browse through our collection of videos matching "hmac function". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "hmac function"
50 results found
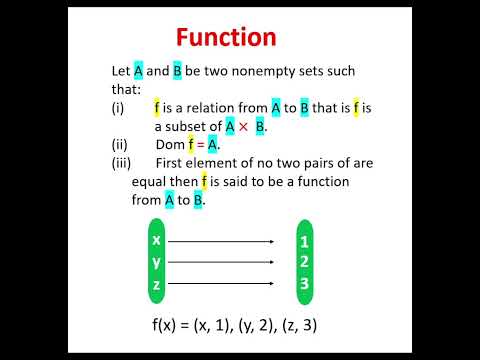
0:09
Function | Definition of function | define function | simple definition of function
Tartull education
23.4K views

9:00
HMAC and CMAC in Cryptography Hash Function || Network Security in Telugu
Lab Mug
10.9K views

11:19
MAC function ,HMAC,CMAC in Cryptography and cyber security tamil||CCS||Anna university reg-2021.
Murugan Tech World
7.8K views

7:40
MAC Based on Hash Function | HMAC in network security
Chirag Bhalodia
67.7K views

12:00
Hash Function in cryptograhy | Properties of Hash Function | Simple Hash Function Technique
Chirag Bhalodia
107.9K views

14:52
Applications of Hash Function | Purpose of Hash Function | Real Time Application of Hash Function
Chirag Bhalodia
32.1K views

0:13
Euler function of 12 |phi function of 12 #Euler function #group #ringtheory #discretemathematics
Alpha Maths Academy
36.8K views

1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views

7:24
Data Integrity - How Hashing is used to ensure data isn't modified - HMAC - Cryptography
Practical Networking
77.9K views

7:05
HMAC - Cryptography I
Nguyen Duong Anh
80 views

11:03
Learn the ART of CRYPTOGRAPHY - SHA-1 HMAC Hashing Explained (Urdu/Hindi)
Cybersecurity Academy - CertificationHUB
184 views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

8:10
#36 HMAC (Hash Based) & CMAC (Cipher Based) |CNS|
Trouble- Free
232.6K views

22:00
CNS HMAC
Kallam Gopala Reddy
312 views

9:24
Securing Stream Ciphers (HMAC) - Computerphile
Computerphile
326.5K views

20:35
HMAC | Cryptography and Network Security
Ekeeda
677 views

1:09:59
Go UUID HMAC
Learn To Code
945 views

10:26
Razorpay integration in asp.net web app | HMac SHA256 signature create and matching
New Arts
1.4K views

0:46
HMAC Promo take 2
Players 2Pros
29 views

12:48
Função de Hash - MD5 e SHA - Código HMAC - Aula completa
Prof. Sergio Villarreal
3.7K views

57:46
Applied Cryptography: 3. Hash functions and HMAC
Applied Cryptography by University of Tartu
635 views

20:58
16-HMAC Algorithm Explained 🔐 | Hash-Based Message Authentication Code in Network Security
Sundeep Saradhi Kanthety
168.4K views

29:42
Message Authentication Code (MAC) and HMAC - Cryptography - Cyber Security CSE4003
Satish C J
37.3K views

8:08
MAC in Hindi - Message Authentication Code Process, Significance, HMAC Concept
Easy Engineering Classes
111.9K views

13:49
V4b: CBC-MAC and HMAC (Applied Cryptography 101)
Cryptography 101
1.1K views

12:51
Cryptography with Python 30: HMAC, Encrypt-then-MAC and GCM
Cyrill Gössi
1.1K views

5:15
HMAC Nested MAC Method || Lesson 73 || Cryptography || Learning Monkey||
Wisdomers - Computer Science and Engineering
1.1K views

6:09
HMAC & Message Authentication Codes (MACs) - Why Hashing alone is NOT ENOUGH for data integrity
JayPMedia
6.7K views

9:40
Message Authentication Codes: CMAC and HMAC
Cihangir Tezcan
4.8K views

6:33
HMAC explained | keyed hash message authentication code
Jan Goebel
85.3K views

0:31
zubeen garg function program 🥰😍 #shorts #zubeengarg #function #bihu #cutegirl
MUSIC ASSAM
1.8M views

21:20
Python Lambda Function | Anonymous Function In Python | Python Tutorial | Edureka
edureka!
63.4K views

3:00
Print function in Python | Python tutorial print() function
CodePy
1 views

8:19
LEC11| Blockchain | Cryptographic Hash Function & Properties of Hash Function by Mrs. G. Sowmya
MLID - MLR Institute of Technology
2.3K views

0:58
Injective, Surjective and Bijective function.|One-One and Onto function.|@vmatics444
V Matics
103.2K views

9:32
Hash function Keya hai? hashing Algorithm? password hashing? password and hash function Hindi
Technical Haroon
8.1K views

0:17
XOR Function In Excel | Excel Formula | XOR Function | Excel World
Zeba Ali
1.5K views

15:44
Asymmetric Key Cryptography - Euler Phi Function (Euler Totient Function)
Vaishali Yadav
231 views

11:33
Zeta function in terms of Gamma function and Bose integral
blackpenredpen
133.8K views

13:19
The Xi Function and the Symmetry of the Riemann Zeta Function
Mike, the Mathematician
337 views

9:00
Hash Functions || hash function algorithm || hash function cryptography || hashing vs encryption
The Ecomly Tech
24 views

10:29
Function अब उंगलियों पर Basics of Function (in Hindi)
Absolute world
5 views

10:19
Aggregate Function in Excel in Hindi | Excel Sheet Aggregate Function
Cybotech Campus Nawada
14 views

10:29
The F Function of DES (Mangler Function)
Neso Academy
165.2K views

6:58
One - way function & trapdoor function in modern cryptography
Sunny Classroom
13.9K views

0:55
Differential Calculus (Limits & Continuity) - Absolute function; Continuity of function
Saameer Mody
390 views

7:40
Hash function based on CBC in cryptography | Hash function based on cipher block chaining
Chirag Bhalodia
24.0K views

8:40
Euler’s Totient Function (Phi Function)
Neso Academy
350.3K views

0:13
"Master the PRODUCT Function in Excel | Easy Excel Formula" | "Excel PRODUCT Function | Multiply Multiple Values in Excel"
Mr. EXCEL HACKS
1.8K views

0:39
Creating a function in Python. Use the "def" keyword, give a function a name and list its arguments
Funy Coder
78.9K views