Search Results for "data confidentiality"
Find videos related to your search query. Browse through our collection of videos matching "data confidentiality". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "data confidentiality"
51 results found

1:27
confidentiality meaning l meaning of confidentiality l confidentiality ka matlab Hindi mein l vocab
Worldwide Dictionary
865 views

1:04
Java Secure Coding: Data Confidentiality and Integrity 12 2 Asymmetric Crypto
AppSec Labs
823 views

3:54
How Does Encryption Ensure Data Confidentiality In Network Security? - Talking Tech Trends
TalkingTechTrends
1 views

4:11
Demystifying Data Encryption: Safeguarding Secrets for Confidentiality and Integrity
bytesofinfosec
20 views

0:06
Types of Data 1)Quantitative Data 2)Qualitative Data Statistics #education #statistics #data data
Student Study House
173.7K views

2:47
Data Entry Services, Data Processing, Data Coversion, Data Mining Services Data Entry Solution
Dataentrysolution
5 views
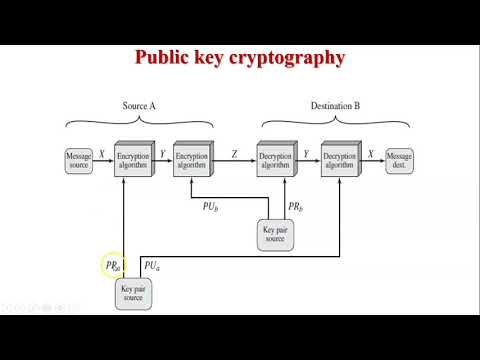
7:14
Application of public key cryptography | Authentication | Confidentiality | Digital Signature
Chirag Bhalodia
22.5K views

0:28
Ensuring Confidentiality and Non-Repudiation in Messages #shorts #cybersecurity #cissp
CISSP Study Group
454 views

0:36
Public and Private Key #availability #ciatriad #confidentiality
CompScience101
1.1K views

18:31
RC4, PLACEMENT OF ENCRYPTION FUNCTION, TRAFFIC CONFIDENTIALITY & KEY DISTRIBUTION IN CRYPTOGRAPHY
COMPUTER SCIENCE & ENGINEERING
6.6K views
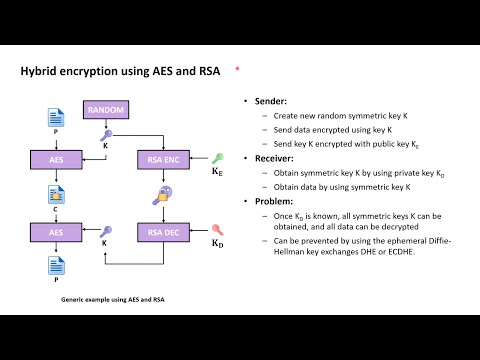
13:09
TLS Essentials 3: Confidentiality with AES, RSA & hybrid encryption
Cyrill Gössi
1.7K views
34:32
Cryptography Fundamentals: Confidentiality, Integrity, & Non-Repudiation Explained
Ricardo Calix
32 views

4:18
cyber security goals- CIA confidentiality,integrity,availability in hindi | MCA/btech/bca/bsc it
Unbeaten Learning
90.6K views

0:43
CIA Triads in Cyber Security #cia #triads #confidentiality #integrity #availability
CyberNIIX
391 views

59:37
The State of Personal Online Security and Confidentiality | SXSW LIVE
SXSW
103.0K views

5:33
Network Security Goals :Confidentiality, Integrity, Availability |CIA Triad in Cryptography hindi
DK Technical Point 2.0
2.0K views

26:06
CRYPTOGRAPHY & NETWORK SECURITY CONFIDENTIALITY USING SYMMETRIC ENCRYPTION
vignan degree college
5.7K views

6:32
Security Goals : Confidentiality,Integrity,Availability Explained in Hindi
5 Minutes Engineering
655.8K views

2:31
How to achieve Confidentiality using PKI?
PKIIndia
296 views

0:49
Confidentiality: Symmetric key Encryption #cybersecurity #cryptography #encryption #education
The Cyber Dojo
26 views

0:32
Mastering Cybersecurity Confidentiality, Integrity, Availability Explained
Cyber Guardians
548 views

9:55
CIA Model | Confidentiality, Integrity, Availability, Authenticity and Non-Repudiation | Hindi
Cyberwings Security
70.2K views

9:11
Security goals of Cryptography (Authentication, Integrity, confidentiality and, Repudiation) Hindi.
Helping Tutorials
12.1K views

12:34
Cybersecurity Architecture: Fundamentals of Confidentiality, Integrity, and Availability
IBM Technology
269.8K views

7:52
Security Goals - Confidentiality, Integrity and Availability - Cryptography and Network Security
Dr. Faheem Mushtaq
198 views

2:29
Confidentiality, Integrity, Availability | Security Goals | In HINDI
5 Minutes Programming
550 views
0:25
Confidentiality | CISSP |
Professional Certifications
214 views
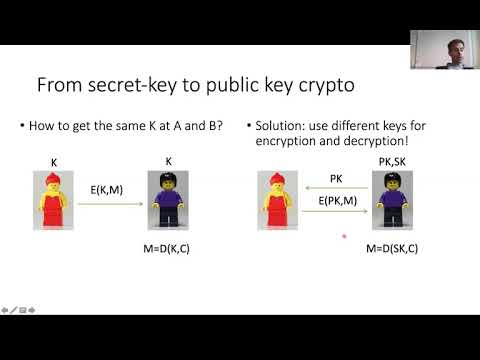
32:01
5.3. Confidentiality: Public-key Encryption
Blockchain Academy Network
430 views

0:58
Master Confidentiality: Your CIA Triad Guide!
Justin
13 views

10:29
Lightweight Cryptography Delivers Confidentiality and Integrity to IoT
ursamajor.technology
524 views

4:06
Security Goals in Cryptography Network Security | CIA Traid | Confidentiality Integrity Avalaibility
Techystudy Best Learning Online
240 views

9:27
CIA Properties | Confidentiality, Integrity, Availability with examples
Gate Smashers
207.4K views

0:16
What is confidentiality ?
Networks Professionals
95 views
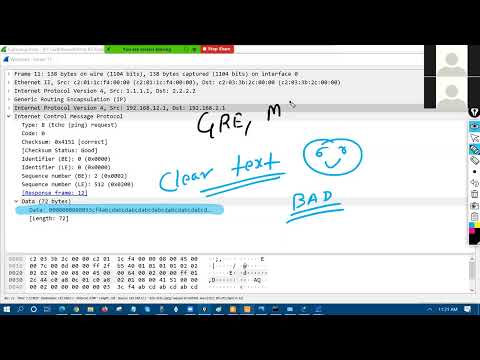
1:27:36
IPsec Day1 Authentication, Encryption, Confidentiality | Substitution Transposition Techniques
Law Sah
142 views

10:09
CIA Triad: Confidentiality, Integrity & Availability | Cybersecurity
Gate Smashers
54.7K views

22:50
BEST PAPER AWARD: Cryptanalysis of OCB2: Attacks on Authenticity and Confidentiality
IACR
833 views

1:46:34
Lecture 3 SYMMETRIC ENCRYPTION AND MESSAGE CONFIDENTIALITY
Quantum Tech Academy
776 views
0:31
WHAT IS CONFIDENTIALITY IN CIA TRIAD?
TNV Akademi
552 views

37:21
Cryptography, Security Modelling, Privacy, and Confidentiality in Hyperledger
LF Decentralized Trust
917 views
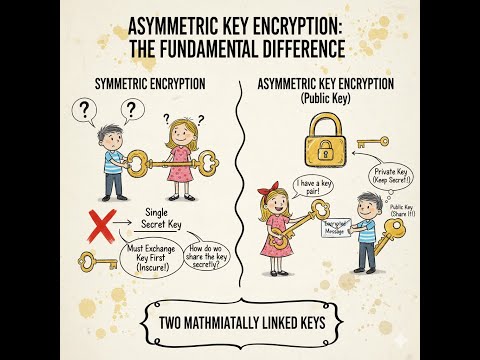
5:18
Confidentiality: Asymmetric Key Encryption #cybersecurity #cryptography #encryption #education
The Cyber Dojo
27 views
10:20
traffic confidentiality in cryptography and network security explain in Telugu
Hema study tutorial
5.8K views
0:14
Cyber Security Does the encryption algorithm RSA provide confidentiality
Trivia Quiz App general knowledge & programming
26 views

13:32
Confidentiality : Traditional symmetric key ciphers, substitution ciphers
Pravisha candideyes
544 views
5:18
2. Confidentiality 101 Introduction. Symmetric and Asymmetric encryption.
AgileMark Pod
102 views

0:16
Olivia Dunne Jokes That She Broke SI Swimsuit’s Confidentiality Agreement for One Special Person
Sports Illustrated
4.7K views

3:48
HOWAI CLARIFIES CONFIDENTIALITY WITH FOREX
CCNTV6
467 views

1:00
CIA Triad | Confidentiality | Integrity | Availability #cybersecurity #ciatriad
Cyber Aware Hub
5.8K views

2:59
Episode 137: Encryption - Part 13 - Confidentiality
SANS Digital Forensics and Incident Response
382 views
0:26
Symmetric and Asymmetric Encryption are important concept for confidentiality in cybersecurity
RZ_Cyber
111 views

0:56
Data Analyst vs Data Scientist | Difference between Data Analyst and Data Scientist | Must Watch
Analytics Vidhya
108.9K views

3:48
HOWAI CLARIFIES CONFIDENTIALITY WITH FOREX
CCNTV6
467 views
Page 1 Next