Search Results for "cse4003"
Find videos related to your search query. Browse through our collection of videos matching "cse4003". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "cse4003"
29 results found

51:39
Data Encryption Standard (DES) - Explained with an Example - Cryptography - CyberSecurity - CSE4003
Satish C J
82.4K views

26:29
Chinese Remainder Theorem - Cryptography - Cyber Security CSE4003
Satish C J
7.8K views

34:59
AES IV - Advanced Encryption Standard - Encryption and Decryption - Cyber Security CSE4003
Satish C J
120.4K views

19:33
Caeser Cipher and Multiplicative Cipher - Cryptography - Cyber Security CSE4003
Satish C J
4.8K views
20:16
Vigenere Cipher - Explained with an Example - Cryptography - Cyber Security - CSE4003
Satish C J
20.7K views

36:01
Block Cipher Modes - Cryptography - Cyber Security - CSE4003
Satish C J
10.5K views

18:54
Modular Exponentiation - Cryptography - Cyber Security - CSE4003
Satish C J
16.0K views

40:54
Miller Rabin Primality Test with Examples - Cyber Security - CSE4003
Satish C J
10.5K views

16:59
Primality Testing - Fermat's little Theorem - Carmichael Numbers - Cyber Security CSE4003
Satish C J
17.7K views
4:58
Public key Cryptography - What is it? - Cryptography - Cyber Security - CSE4003
Satish C J
6.1K views
44:53
Introduction to Hash Functions and Application of Hash Functions in Cryptography - CSE4003
Satish C J
24.6K views

23:24
Playfair Cipher - Explained with an Example - Cryptography - Cyber Security CSE4003
Satish C J
5.5K views

41:31
Elliptic Curve Cryptography - Session 1 - Cyber Security CSE4003
Satish C J
43.5K views

16:01
RSA Algorithm - Explained with Examples - Cyber Security - CSE4003
Satish C J
20.0K views

23:37
Discrete Logarithm -Finding Primitive Roots - Cryptography - CSE4003
Satish C J
26.2K views

48:51
Hping3 Demo- Kali Linux - Ping Flood and SYN Flood Attack - DOS and DDOS - Explained - CSE4003
Satish C J
71.1K views
22:40
Modular Arithmetic - Congruence and its Properties - Cryptography - Cybersecurity - CSE4003
Satish C J
8.2K views

32:45
Hill Cipher - Encryption and Decryption - Step by Step - Cryptography - Cyber Security - CSE4003
Satish C J
55.0K views
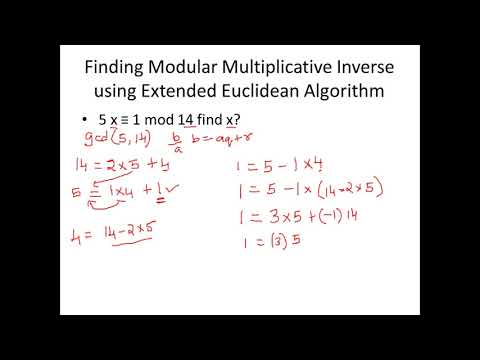
15:14
Modular Multiplicative Inverse - Cryptography - Cyber Security - CSE4003
Satish C J
14.5K views

6:09
Fermat's Theorem - Cryptography - Cyber Security - CSE4003
Satish C J
3.9K views

10:11
Elgamal Cryptosystem - Public key Cryptography - Cyber Security - CSE4003
Satish C J
37.4K views
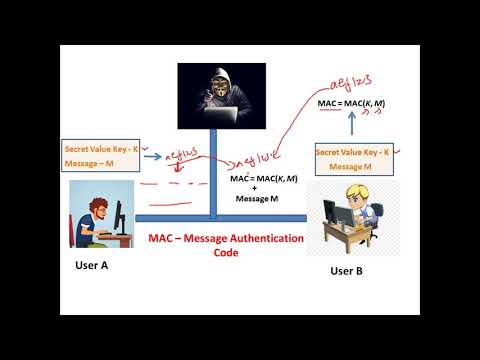
29:42
Message Authentication Code (MAC) and HMAC - Cryptography - Cyber Security CSE4003
Satish C J
37.3K views

16:55
Block cipher modes cryptography cyber security cse4003
CodeFix
3 views
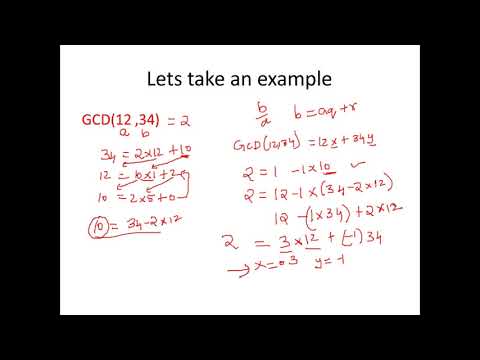
14:34
Extended Euclidean Algorithm - Cryptography - Cyber Security - CSE4003
Satish C J
10.1K views
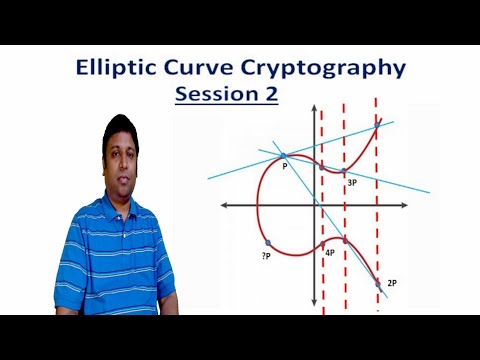
53:39
Elliptic Curve Cryptography - Session 2 - Cyber Security - CSE4003
Satish C J
29.1K views

11:48
Euclidean Algorithm for Finding GCD - Cryptography - Cyber Security - CSE4003
Satish C J
9.4K views

37:02
AES III - Advanced Encryption Standard - Introduction , Key Expansion in AES Cyber Security CSE4003
Satish C J
90.7K views

15:27
Diffie Hellman Key Exchange Algorithm - Cryptography - Cyber Security - CSE4003
Satish C J
18.7K views

17:40
Block Cipher Vs Stream Cipher - Cryptography - Cyber Security - CSE4003
Satish C J
26.1K views