Search Results for "cryptographic orchestration"
Find videos related to your search query. Browse through our collection of videos matching "cryptographic orchestration". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "cryptographic orchestration"
50 results found

1:50
Data Center Orchestration Part 3: Maintenance Mode
F5 Networks
7 views

6:23
Management & Orchestration Enablement Strategies
LightReading
1.5K views

8:50
Introduction to Cryptographic Attacks | Types of Cryptographic Attacks Explained With Measures
Shree Learning Academy
2.3K views

0:34
Cryptographic | CRYPTOGRAPHIC meaning
Word Mastery Channel
0 views

6:55
Attacks on Cryptographic Hash Algorithms || what is cryptographic? || Best Mind Like
Best Mind Like
45 views

0:34
How To Pronounce Cryptographic🌈🌈🌈🌈🌈🌈Pronunciation Of Cryptographic
Isabella Saying
33 views

0:02
How to pronounce Cryptographic / Cryptographic pronunciation
Raccoon Teaches You
48 views

9:59
VTU June 19 - Definition And Properties of Cryptographic Hash - Cryptographic And Network Security
Education
66 views

0:33
How Cryptographic Hash Functions Keep You Safe! 🔍 #cryptocurrency #bitcoin #blockchain #shorts
Cryptocurrency Classroom
94 views

23:38
The Price Of Active Security In Cryptographic Protocols
Fidelity Center for Applied Technology (FCAT®)
31 views

0:47
The Enigma Machine: Cryptographic Innovator
Bored Sapien
318 views

0:58
The Secret Codes of the Enigma Machine: Cryptographic Turning Point
History with AI
263 views

17:31
BIKE - Cryptographic Engineering
Danny Silvestre Suarez
243 views

6:03
Cryptanalysis - Cryptographic Services - Network Security - CCNA - KevTechify | vid 63
Kev Techify
221 views

1:38:51
PETS 2022 Moti Yung Keynote Privacy Integrated Computing” Cryptographic Protocols in Practice
All Hacking Cons
17 views

10:14
Bitcoin - Cryptographic hash function
Khan Academy
284.5K views

1:05
The Science of Blockchain: Cryptographic Trust
Thought Shot
190 views
0:10
Cryptographic Terms
Quick Cybersecurity Study
352 views

9:04
Message Digest and Digital Signature | Cryptographic Hash Function
saurabhschool
16.4K views
26:35
Symmetric Cipher Model & Cryptanalysis: Exploring Cryptology & Cryptographic Categories - Encryption
Mukesh Chinta
596 views

4:47
PBL RKS-115 Implementation of Cryptographic Algorithms in Steganography and Puzzle Game
Kelompok 5 PBL-115 RKS
35 views

8:32
What is a Cryptographic Hash function?
Keifer Kif
1.4K views

23:33
Basics of Cryptology – Part 22 (Cryptography – Kerckhoffs' Principle & Modern Cryptographic Goals)
Cryptography for Everybody
1.7K views

1:00
Cryptography: The Importance of Strong Encryption #code #accesscontrol #cryptography #cryptographic
Muskan Singh
286 views

25:17
CS C S009 Non-Cryptographic Protocol Vulnerabilities
Studio IIT Bombay
539 views
![[CompNetSec] - 13 - Cryptographic Hash Functions](/image/i.ytimg.com/vi/2yxHePuitJc/hqdefault.jpg)
1:00:43
[CompNetSec] - 13 - Cryptographic Hash Functions
Hicham Elmongui
7.3K views

5:30
Cryptographic Technology | Steganography | Cryptology | Basic Terminology of Cryptography
CSE Adil
10 views

0:44
Revolutionizing Digital Privacy with Advanced Cryptographic Techniques
Tech-Pulse-7
27 views

3:46
An assessment of cryptographic protocols susceptible to quantum attacks
Aliro
63 views
26:57
CH3 Cryptographic Hash Functions 1
د محمود-الحاسبات وتقنية المعلومات
293 views
![[PriSC'25] Keynote: Bringing Verified Cryptographic Protocols to Practice](/image/i.ytimg.com/vi/3mshgSCvH40/hqdefault.jpg)
1:00:28
[PriSC'25] Keynote: Bringing Verified Cryptographic Protocols to Practice
ACM SIGPLAN
32 views
16:50
The Caesar Cipher: A Simple Yet Powerful Cryptographic Technique
Harshit Jain
78 views

1:50
10 Exciting Facts About Cryptographic Engineering | KNOW iT
KNOW iT
12 views
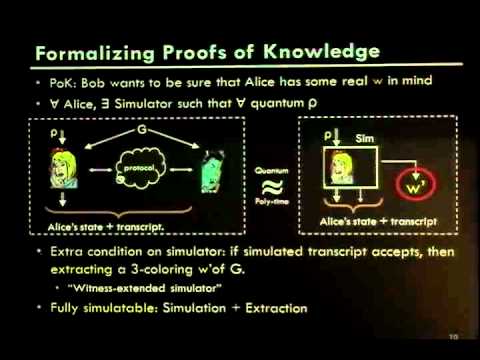
19:25
Classical Cryptographic Protocols in a Quantum World
IACR
532 views

48:51
The State of Cryptographic Multilinear Maps
IACR
1.4K views

0:42
The Puzzling Emergence of the 2002 Quantum Cryptographic Conundrum
Social Media Trails
896 views

0:51
The Hidden Genesis of Diffie-Hellman: A Cryptographic Breakthrough
Offbeat Paths
133 views

0:58
The Enigma of the Kryptos Sculpture: A Modern-Day Cryptographic Puzzle
Bouncer Mania
600 views

2:09
A Quantum Random Number Generator for cryptographic applications
Stripe YSTE
1.3K views
0:33
Mastering Key Management Unlocking Cryptographic Secrets
Suggest Name
30 views

0:15
Types Of Cryptographic Techniques
EduAllinOne
3 views

0:56
The Enigma Machine: A Turning Point in Cryptographic History #ww2 #enigma
TruthDiscovery
35 views

3:47
Cryptographic Keys - CompTIA Security+ SY0-501 - 6.1
Professor Messer
71.0K views

2:18
Cryptographic Devices Provide Clues to History, Politics
Duke University
2.9K views
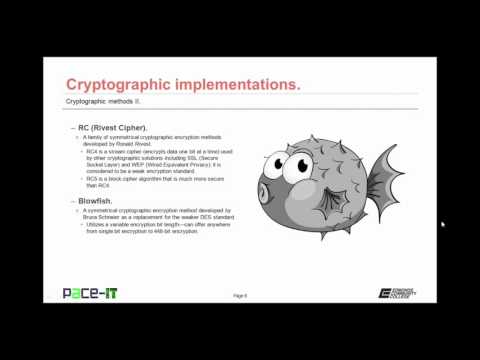
7:54
PACE-IT: Security + 6.2 - Cryptographic Methods (part 2)
PaceIT Online
249 views

38:57
HOPE Number Six (2006): Constructing Cryptographic Protocols
Channel2600
112 views
![[POPL'23] A Core Calculus for Equational Proofs of Cryptographic Protocols](/image/i.ytimg.com/vi/5rQstrKftGE/xhqdefault.jpg.pagespeed.ic.Z9JzJlLjY0.jpg)
25:50
[POPL'23] A Core Calculus for Equational Proofs of Cryptographic Protocols
ACM SIGPLAN
291 views

58:37
s-7: Cryptographic Primitives I
IACR
530 views

0:11
03 ✅ Cryptographic #virl #ytshorts #shorts Blockchain #youtubeshorts Bitcoin
TechNo Alee
34 views

27:51
Cryptographic Protocols
GNS S
203 views