Search Results for "computationally secure encryption scheme"
Find videos related to your search query. Browse through our collection of videos matching "computationally secure encryption scheme". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "computationally secure encryption scheme"
51 results found

0:13
Difference between unconditionally secure and computationally secure in cryptography and .....
SUKANYA BASU
973 views

4:10
Difference between Computationally Secure and Unconditional Secure Cipher | Information Security
Easy Engineering Classes
6.4K views

5:06
10th class computer pairing scheme 2024 |10th class computer scheme 2024 | 10th computer scheme 2024
Shahid Iqball
50 views

25:02
Computationally Volume-Hiding Structured Encryption
IACR
775 views

9:47
Ponzi scheme explained simply Urdu Hindi _ How pyramid scheme works_ _Ponzi schemes India Pakistan
Dr Muhammad Farooq Buzdar
61 views

0:07
Read Proxy Blind Multi-Signature Scheme: Proxy Blind Multi-signature Scheme Using Elliptic
Isaksen
0 views

16:27
Secure Tensor Decomposition Using Fully Homomorphic Encryption Scheme
SivaKumar ChennaiSunday
100 views
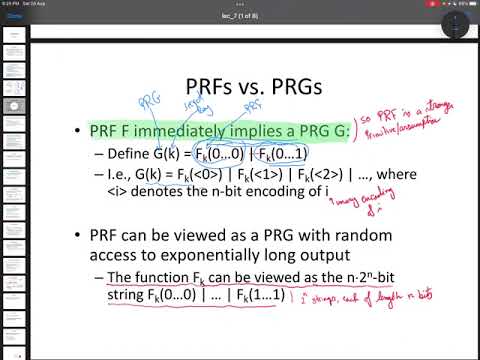
50:22
Lecture 11: Encryption scheme that is CPA-secure
Cryptography - علم التشفير
773 views

14:44
Toward a Fully Secure Authenticated Encryption Scheme From a Pseudorandom Permutation
IACR
111 views

7:15
How to secure Gmail ? || Gmail ko secure kaise kare ?क्या आपका Gmail Secure है ?
DoWithMe Start Learning
1 views

32:17
A Hybrid Scheme of Public-Key Encryption and Somewhat Homomorphic Encryption
ChennaiSunday Sivakumar
241 views
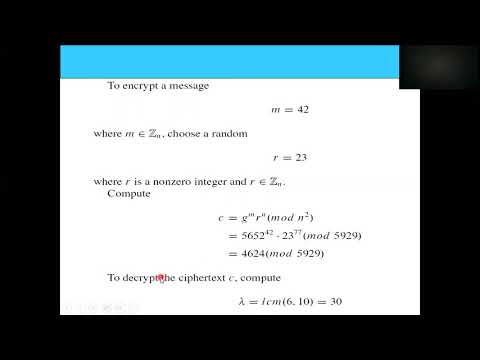
17:32
Paillier Encryption Scheme | Homomorphic Encryption Algorithm | E-Votin
Dr. Majid Khan Mathematics Waley
4.7K views

49:40
Design and of Encryption/ Decryption Architectures for BFV Homomorphic Encryption Scheme
Ekalavya Projects
757 views

7:13
A SECURE DATA DYNAMICS AND PUBLIC AUDITING SCHEME FOR CLOUD STORAGE | CLOUD COMPUTING
Takeoff Edu Group
523 views

13:18
Introduction to Cryptographic Hash Function| Merkel Damgard Scheme | SHA-256 | Secure Hash Algorithm
Muhammed Mustaqim
607 views
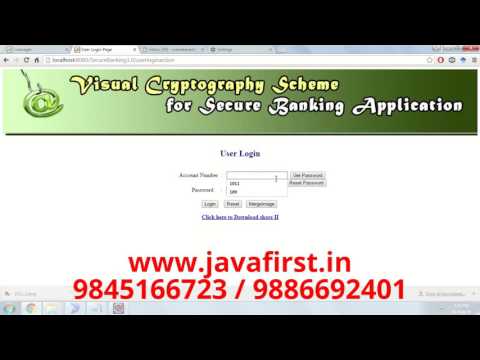
8:32
Visual Cryptography Scheme for Secure Banking Application
DHS Projects Bangalore
766 views

0:51
Elliptic Curve Cryptography-Based Scheme for Secure Signaling and Data Exchanges in P... | RTCL.TV
Social RTCL TV
106 views

1:01
A Secure Payment Scheme with Low Communication and Processing Overhead for Multihop Wireless Networks
JPInfo
25 views

0:46
Sunak launches scheme to help veterans secure high-paid jobs
ODN
2.0K views

1:11
What is Encryption? Explain Encryption, Define Encryption, Meaning of Encryption
Audioversity
261 views

26:41
How does Digital Signatures and Encryption actually work in the RSA Scheme - With Maths?
LearnWeb3
919 views
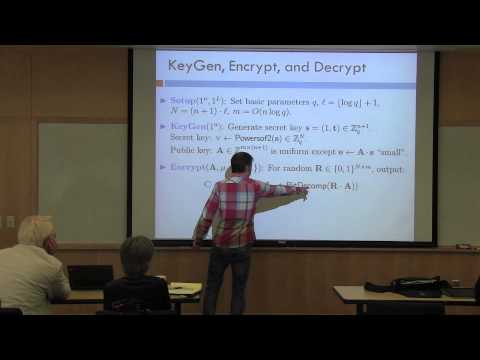
1:21:56
14 Craig Gentry on a Simple Fully Homomorphic Encryption Scheme & Thoughts on Bootstrapping
Workshop on Lattices with Symmetry
5.9K views

22:32
Jintai Ding - ZHFE, a New Multivariate Public Key Encryption Scheme
Institute for Quantum Computing
2.2K views

2:21
Mr. Larson said that by some estimates, with the default encryption scheme
RisingWorld
0 views

0:43
Cryptanalysis of a Symmetric Fully Homomorphic Encryption Scheme
XOOM PROJECTS
4 views

5:13
Five ingredients of symmetric encryption scheme
Ganesh Balgi
806 views
1:08
Cryptanalysis of An Identity Based Encryption Scheme with Equality Test and Improvement
IFoxProjects
51 views
10:37
Performance Measurement of a Hybrid Encryption Scheme on an Embedded System
Computer Science & IT Conference Proceedings
37 views
3:54
How to establish an encryption key securely with the Quantum Key Distribution scheme ?
satnamo
2.4K views
1:15
Image encryption scheme using DNA and bases probability
sahil
438 views

1:17:51
Lecture 15: Elgamal Encryption Scheme by Christof Paar
Introduction to Cryptography by Christof Paar
67.2K views
31:12
An Efficient Multi User Searchable Encryption Scheme without Query Transformation Over Outsourced En
1 Crore Projects
626 views
16:09
Network security model and symmetric encryption scheme
Sarvani Anandarao
96 views
0:28
Implementation and Performance Evaluation of RNS Variants of the BFV Homomorphic Encryption Scheme
IFoxProjects
62 views

6:22
MATLAB code of Joint image encryption and compression scheme based on IWT and SPIHT
MATLAB CLASS
126 views
0:57
A post-quantum image encryption scheme
AiSeQ laboratory
147 views

14:15
Entity Encryption using AES | Spring Boot | JPA | Advanced Encryption Standard | Secure your data
VKS Tech
10.7K views

11:44
Encryption and Decryption in C language."Secure Code: to Implement Encryption and Decryption in C"
BAD engineer
292 views

0:37
Unbreakable Encryption Software. Top Secret Cryptography X.9 - One Time Pad, a High Power Unbreakable Encryption Software. Set up a secure system of communication, a proven system, that cannot be cracked by the FBI, DEA, CIA, NSA, or any other.
unbreakable_crypto
566 views

2:00
🔐 Encryption & Decryption Explained | How Data Stays Secure Online!#CyberSecurity #Encryption #yt
TechyBoyEra
82 views

2:48
Why Is Quantum Encryption Considered More Secure Than Classical Encryption? - Quantum Tech Explained
Quantum Tech Explained
0 views

1:00
The Top 5 Most Secure Encryption Methods | 2024 Guide#Cybersecurity #Encryption #DataProtection
TOP X FACTS
254 views

8:37
SSH (Secure shell) protocol in Hindi | Secure shell protocol in Network Security
Abhishek Sharma
84.3K views

46:18
Roll Your Own Secure Cloud Storage with SSHFS - Secure Shell File System - Hak5
Hak5
5 views
0:55
Overview of Secure Aggregation #ai #artificialintelligence #machinelearning #aiagent Overview Secure
NextGen AI Explorer
12 views

2:05
Secure USB Flash Drive - SanDisk Enterprise Secure ...
John Objet
1 views

0:05
Read Secure Software and Comm. on Handheld Devices: Secure Software and Communication on Handheld
Isaksen
2 views

3:39
Medical Coding Services | Secure Medical Coding & Secure Medical Data Handling
PDNSeek .com
5 views

4:53
Best browser for privacy 2021 | Iridium Browser | A browser securing your privacy | Most Secure Web Browsers That Protect Your Privacy | most secure browser 2021
FOCUS EXCLUSIVE
13 views

0:25
A Secure Erasure Code-Based Cloud Storage System with Secure Data Forwarding
satish20059
259 views

0:46
Sunak launches scheme to help veterans secure high-paid jobs
ODN
2.0K views
Page 1 Next