Search Results for "compression attack steganography"
Find videos related to your search query. Browse through our collection of videos matching "compression attack steganography". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "compression attack steganography"
50 results found

1:24
ten10@attack Lions attack Animal attack Top Attack to Animal Attacks And Loves when animals attack
Le Monde Artistique
129 views
16:25
Encryption Before Compression or Compression Before Encryption?
Cryptography for Everybody
2.3K views

0:50
and compression springs - are compression springs
AcxesSpring
12 views

5:07
Compression Spring Rate - Compression Springs
planetspringcom9
534 views

26:47
JPEG Compression - Image Compression - Image Processing
Ekeeda
19.7K views

21:05
Theory of Lossless JPEG - Image Compression - Data Compression and Encryption
Ekeeda
4.3K views

42:43
Theory of JPEG Compression - Introduction to - Data Compression and Encryption
Ekeeda
5.2K views

2:58
passive attack and active attack in hindi / passive attack and active attack difference ||#mscoder
ms coder
3.9K views

5:41
MATLAB code of Digital image Steganography with AES encryption and compression attack
MATLAB CLASS
356 views

1:50
steganography/steganography in hindi/steganography example/ steganography in cyber security|#mscoder
ms coder
4.5K views

3:02
Difference between Active and Passive attack | Active vs Passive attack | Passive vs Active attack
Chirag Bhalodia
15.9K views

1:18
DES-Brute Force attack-in cryptography/ define brute Force attack/what is brute Force attack
Cse View
1.8K views
0:58
Heart Attack: Early Signs and Symptoms - What is a heart attack Hindi Urdu | What Causes a Heart Attack?
All viral available
13 views

1:31
Attack! Attack! Attack
mtwmike
19 views

8:49
Piranha Attack on Humans [Animals Attack, Animal Attacks, Piranha Attacks, Piranha Attack
Leann Coronel
2 views

19:23
DDoS Attack | DDoS Attack Explained | What Is A DDoS Attack? | Cyber Attacks Explained | Simplilearn
Simplilearn
43.0K views

17:12
Dos and Ddos attack | Dos attack | denial of service attack | lecture 35
Simply Made
104.8K views

5:10
Lossless Compression And Information Hiding In Images Using Steganography | 1 Crore Projects
1 Crore Projects
208 views

2:50
Prj. An Edge Based Image Steganography with Compression and Encryption by Alex21C
Abhishek kumar
160 views

7:53
Hiding Data Using Efficient Combination of RSA Cryptography, and Compression Steganography Technique
OKOKPROJECTS
411 views
9:23
Hiding Data Using Efficient Combination of AES Cryptography, And Compression Steganography Technique
Naren Projects
271 views
3:13
Image Steganography and Compression Using Matlab Full Source Code
Matlab Projects
206 views

3:13
Matlab Code for Image Steganography & Compression Using DCT Matlab Project With Source Code
Matlab Projects
176 views

3:13
DCT Based Image Steganography & Compression Matlab Project With Source Code
Roshan Helonde
917 views

15:53
Cryptography and Network Security Attacks | Active Attack Vs Passive Attack | Steganography | AKTU
Edu Desire
1.9K views

1:25
Steganography/define Steganography/what is Steganography
Cse View
607 views

21:38
Backdoor | The Secret party Invite | Steganography | Image Steganography | Audio Steganography
Soundarya Durairaj
36 views

2:48
STEGANOGRAPHY Practical | Steganography examples | Steganography Techniques | Cyber Threats
ISO Training Institute
5.0K views

7:39
51 Steganography with OpenPuff || OpenPuff Steganography | kali Tutorial Steganography || OpenPuff
冊尺.廾丹亡片ヨ尺
75 views

7:48
what is steganography | type of steganography | how steganography works
PAKIT HUB
45 views

1:16
Steganography Projects | Steganography Projects using Matlab | Steganography Project in Python
MatlabSimulation. Com
55 views

5:45
52 Steganography with SNOW || Kali Tutorial Steganography | Steganography
冊尺.廾丹亡片ヨ尺
1.0K views

2:21
Hide any file in a photo or a video steganography || Steganography ||steganography tutorial
Uday Kumar Madarapu
181 views

12:39
What is STEGANOGRAPHY | INTRODUCTION TO STEGANOGRAPHY | STEGANOGRAPHY Explained HINDI URDU
LearnEveryone
12.3K views

0:18
Vari-Mu vs 1176/LA-2A: Quick Vocal Compression Decisions
Scott Murphy
1.3K views

0:10
Harshvardhan Rane Upcoming Movies 2026 #sanamterikasam2 vs #silaa #upcoming#movie#compression#shorts
Filmi Fast Update
1.4K views

0:57
Compressor shootout: LA-2A #mixing #compressor #compression #shootout #la2a #studio #producer
Mixing Theory Online
47 views

2:48
Encryption-then-Compression Systems usingGrayscale-based Image Encryption for JPEG Images
sahil
120 views
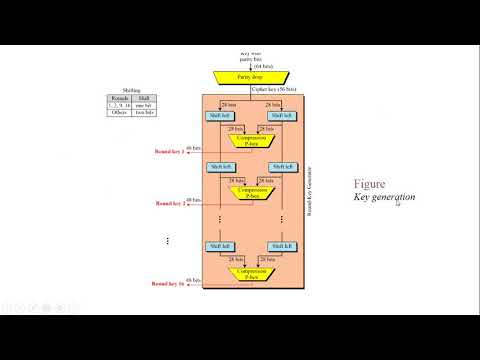
13:15
Lecture 11 DES Key Compression
Ansif Arooj Lectures
510 views

1:42
Designing an Efficient Image Encryption-Compression System Using A New Haar Wavelet
PhD Support & Journal Writing
73 views
0:13
Designing an Efficient Image Encryption Compression System using a New HAAR SYMLET and COIFLET W
PhD Research Labs
99 views

8:35
Commutative Encryption and Data Hiding in HEVC Video Compression | Matlab Image Processing Project
JP INFOTECH PROJECTS
742 views

0:05
Dharmendra vs Amitabh Bachchan Filmography Compression #amitabhbachchan #dharmendra
A2 Motivation Top 5
11.9M views

28:32
Public Key Compression and Modulus Switching for Fully H ...
IACR
967 views
![[GITHUB Provided] Image Encryption by RSA Algorithm upon Image Compression by DCT and Huffman Coding](/image/i.ytimg.com/vi/VM4CL5XHZqI/xhqdefault.jpg.pagespeed.ic._QSTlbAq8r.jpg)
5:27
[GITHUB Provided] Image Encryption by RSA Algorithm upon Image Compression by DCT and Huffman Coding
A Tsang PolyU
301 views
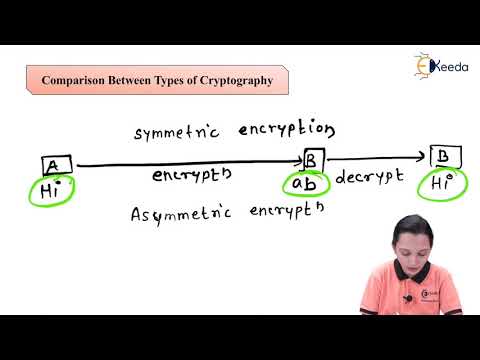
15:25
Comparison Between Types of Cryptography - Data Security - Data Compression and Encryption
Ekeeda
64 views

0:05
Read The Mathematics of Coding Theory: Information Compression Error Correction and Finite
Takoush
0 views
![[Download] Introduction to Information Theory and Data Compression, Second Edition (Applied](/image/s2.dmcdn.net/v/GyCLP1e3VO0z5yHEw/x720)
0:22
[Download] Introduction to Information Theory and Data Compression, Second Edition (Applied
Arsenios Atte
4 views

6:16
Video Compression Algorithms Explained in Hindi/Urdu | Full Movie in 1GB???
TechInfoEdu
11 views
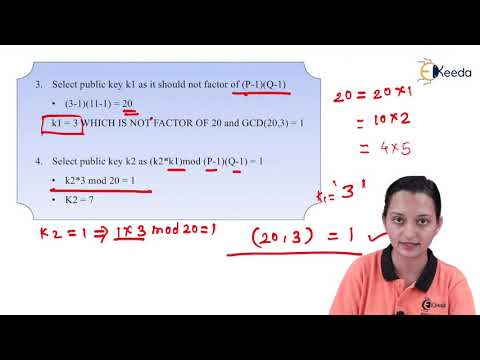
18:49
RSA Algorithms - Number Theory and Asymmetric Key Cryptography - Data Compression and Encryption
Ekeeda
718 views