Search Results for "collision resistance is desirable for hash functions"
Find videos related to your search query. Browse through our collection of videos matching "collision resistance is desirable for hash functions". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "collision resistance is desirable for hash functions"
50 results found

10:30
Introduction to HASHING in Data Structures || Hash Functions,Hash Table, Hash Keys,Hash Values in DS
Sundeep Saradhi Kanthety
11.5K views

8:56
11 Cryptographic Hash Function and its Properties: Pre-image, Second Pre-image, Collision Resistance
Dr Nitin Naik - Aston University, UK
29.5K views

19:15
Hash Functions in hashing, Hashing in data structures, Types of hash functions, division method
CSIT Tutorials by KanyaKumari
4.5K views
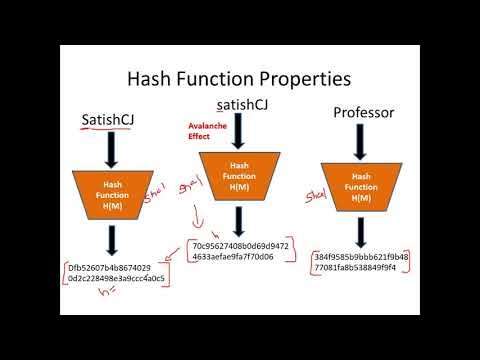
44:53
Introduction to Hash Functions and Application of Hash Functions in Cryptography - CSE4003
Satish C J
24.6K views

9:00
Hash Functions || hash function algorithm || hash function cryptography || hashing vs encryption
The Ecomly Tech
24 views

0:13
Hash Oil,buy Hash oil online,Hash oil for sale,Prefilled hash oil cartridges for sale http://dabstarshop.com
dabstarshop dabstarspharmacy
1 views

0:54
🔑 What is Hashing? | Hash Functions & Collision Handling Explained | Java Data Structures #dsa
Dev Dood
186 views

0:46
What Is Hash Collision and What Does It Mean To Be Resistant To Hash Collisions?
Binance Academy
1.3K views

5:33
L-6.2: Collision Resolution Techniques in Hashing | What are the collision resolution techniques?
Gate Smashers
1.1M views

7:26
Highly desirable (White) House for sale. Price tag: one bill
malinga123_80
6 views
![ACM CCS 2017 - Improved Collision-Resistance Guarantees for MD-Based [...] - Julia Len](/image/i.ytimg.com/vi/aaW7X50mTS4/hqdefault.jpg)
25:49
ACM CCS 2017 - Improved Collision-Resistance Guarantees for MD-Based [...] - Julia Len
Association of Computing Machinery 2017
259 views

1:17
Muscle Fitness : What is the difference between "fixed resistance" and "variable resistance"?
VideojugSportsandOutdoors
1 views

9:06
Functions | Inverse Functions | Composite Functions | 2023 GCE Maths paper 1 question 15
GCSE Mathematics Zone
92.7K views

25:51
Hash Tables: Hash Functions, Sets, & Maps - DSA Course in Python Lecture 4
Greg Hogg
84.9K views

13:56
Hash Tables and Hash Functions
Computer Science Lessons
1.7M views

9:33
What is Hashing? Hashing Algorithm, Hash Collisions & Hash Functions
Monis Yousuf
20.2K views
![[HINDI] What is a Cryptographic Hash? | Hash Functions | Hashing v/s Encryption | Beginner's Guide](/image/i.ytimg.com/vi/qMemCPACnWw/xhqdefault.jpg.pagespeed.ic.G9pQ20ONPm.jpg)
12:21
[HINDI] What is a Cryptographic Hash? | Hash Functions | Hashing v/s Encryption | Beginner's Guide
Bitten Tech
35.7K views

27:54
CRYPTOGRAPHIC HASH FUNCTIONS in HINDI/URDU | , Secure Hash Algorithm | Birthday Paradox Attack
Shahzeb Khan Dasti
256 views

37:31
Five* non-cryptographic hash functions enter. One hash function leaves.
Linux.conf.au 2016 -- Geelong, Australia
4.7K views

26:58
SHA-512 ALGORITHM || SECURE HASH ALGORITHM || CRYPTOGRAPHIC HASH FUNCTIONS || NETWORK SECURITY
t v nagaraju Technical
174.9K views

12:00
Hash Function in cryptograhy | Properties of Hash Function | Simple Hash Function Technique
Chirag Bhalodia
107.9K views

14:52
Applications of Hash Function | Purpose of Hash Function | Real Time Application of Hash Function
Chirag Bhalodia
32.1K views

16:25
Collision Resolution Techniques in Hashing - Separate Chaining Hash Table - Coding With Clicks
Coding With Clicks
667 views

37:17
How we created the first SHA-1 collision and what it means for hash security - Defcon 25
Elie Bursztein
9.2K views
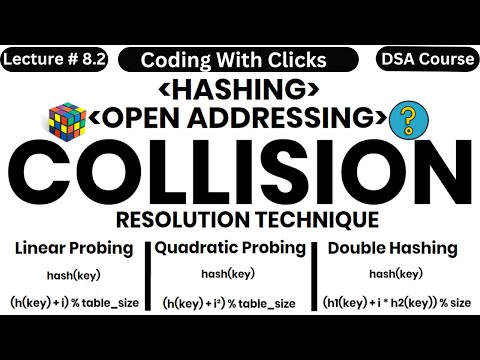
11:47
Collision Resolution Techniques in Hashing - Open Addressing Hash Table - Coding With Clicks
Coding With Clicks
547 views

0:32
3 dynamic array functions you need to know. Who knew all three of these functions?! ✋🏼 #excel
Excel Dictionary
18.0K views

39:14
Python Functions Tutorial | Working With Functions In Python | Python Training | Edureka
edureka!
159.2K views

5:33
Inverse Trigonometric Functions - Functions
Saameer Mody
2 views

13:47
Relation and Functions Part 6 (Graphs of functions ) Mathematics CBSE Class X1
examfear
1 views

1:43
Inverse Trigonometric Functions - Algebra Functions
Saameer Mody
224 views

3:56
Inverse Trigonometric Functions - Composition of Functions
Saameer Mody
227 views

0:18
Linear functions have a constant rate of change and graph as Linear functions#amanyt #sirajshaikh#pw
Ravaan Tutorial
1.0K views

12:12
9 Statistical functions in Excel you need to know | Excel Functions
Excel Tutorial
3.2K views

0:33
How Cryptographic Hash Functions Keep You Safe! 🔍 #cryptocurrency #bitcoin #blockchain #shorts
Cryptocurrency Classroom
94 views
![[Chapter 2a] Cryptography II + Hash Functions & Wordlists](/image/i.ytimg.com/vi/-lCGZIPeExI/xhqdefault.jpg.pagespeed.ic.QXc4mtbpKC.jpg)
2:16:21
[Chapter 2a] Cryptography II + Hash Functions & Wordlists
Avocado
5.9K views

0:51
One way hash functions explained #shorts
Standard Edition Security
225 views

7:27
Hash Functions 🔥🔥
Perfect Computer Engineer
159.9K views

2:36
What is Hashing? Hash Functions Explained Simply
Lisk
440.5K views
![[CompNetSec] - 13 - Cryptographic Hash Functions](/image/i.ytimg.com/vi/2yxHePuitJc/hqdefault.jpg.pagespeed.ce.bngtY8SLsy.jpg)
1:00:43
[CompNetSec] - 13 - Cryptographic Hash Functions
Hicham Elmongui
7.3K views

26:57
CH3 Cryptographic Hash Functions 1
د محمود-الحاسبات وتقنية المعلومات
293 views
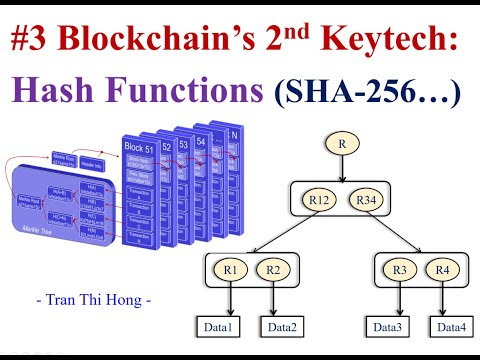
14:13
#4 Why do we need cryptography hash functions SHA256 for blockchain network?
FuTech
274 views

0:56
Cryptographic Hash Functions
Mathematical Minutes
46 views

6:50
Cryptographic Hash Functions (Part 1): Overview
Sourcefire
52.3K views
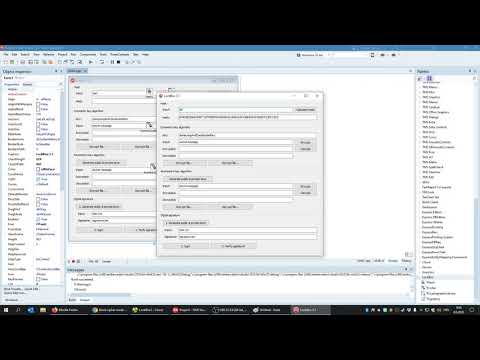
24:32
C++ Builder - Hash functions, Symmetric + Asymmetric Cryptography, and Digital Signature (LockBox)
VCL Examples
3.1K views

49:06
Cryptographic Hash Functions (Contd...2)
nptelhrd
8.8K views

1:04:39
Message authentication and hash functions (part-1)
Keerthi Humsika K
58 views

7:28
Passwords & hash functions (Simply Explained)
Simply Explained
389.8K views

16:37
Message Authentication using Hash Functions - Network Security
Lectures by Shreedarshan K
4.3K views

9:50
Cryptography Explained. Symmetric and Asymmetric Encryption. Hash functions. Digital signatures.
Encyclopedia
136 views

59:18
CSE571-11-11: Cryptographic Hash Functions
Raj Jain
8.1K views
Page 1