Search Results for "authentication using public key cryptography"
Find videos related to your search query. Browse through our collection of videos matching "authentication using public key cryptography". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "authentication using public key cryptography"
50 results found

1:48
Public Speaking | Public Speaking For Beginners | How to Master Public Speaking |How To Improve Public Speaking | Basics Of Public Speaking | Public Speaking and Presentation | Public Speaking For Beginners | How To Talk Confidently
Self Learning Videos
4 views

4:20
What is PUBLIC-KEY CRYPTOGRAPHY? WHat does PUBLIC-KEY CRYPTOGRAPHY mean? PUBLIC-KEY CRYPTOGRAPHY meaning & explanation
The Audiopedia
1 views

6:28
Key Of The Kaaba History In Urdu | key of kaaba family | kaaba,key of kaaba,key of the kaaba history in urdu,key of kaaba history,key of kaaba history in urdu,history of khana kaba,key of kaaba history in english,amazing history of key of khana kaaba
Knowldge Factory
10 views

38:43
Public Key Cryptography | Asymmetric Key Cryptography | Components of Public Key Cryptography
Dr. Majid Khan Mathematics Waley
343 views

6:23
Secrecy and Authentication using Public-Key/Two-Key Cryptography or Asymmetric Encryption
CSE Adil
86 views

11:49
Authentication functions and 3 ways to produce authentication | Message authentication
Abhishek Sharma
263.4K views

4:09
public key applications in urdu hindi | public key applications lecture | public key tutorial | p 41
IT Expert Rai Jazib
121 views

9:55
what is symmetric key cryptography and asymmetric key cryptography , public key and private key
sawji gyaan
10 views

22:28
public key cryptography in urdu hindi| public key cryptography lecture | PK cryptography tutorial|40
IT Expert Rai Jazib
452 views

3:55
difference between public key and private key, what is public key and private key, o level exam,
tech MCQ & theory
3.4K views

17:39
Public Key Distribution -Public Key Authority, Public Certificates #21is71 #cryptography #CNS #VTU
VTU padhai
1.9K views

3:32
Public and Private Keys - Public Key Cryptography - SSH Keys - Public Key RSA Encryption Decryption
Cloud Concepts
48 views

18:07
Lecture 23: Public key cryptography and authentication method Asymmetric Key Requirements
QZ Historia
41 views

11:18
Symmetric Key Cryptography VS Asymmetric Key Cryptography | Private vs Public Key Cryptography
Simple Snippets
8.7K views

15:44
Public Key Distribution in Cryptography | Public Key Distribution | Key Distribution
Chirag Bhalodia
57.3K views

5:34
Public-Key Certificate and Public-Key Infrastructure (PKI) - Asymmetric Cryptography and Key
Ton Ha Nhi
11 views

0:39
sbb key programmer review,Sbb Key Programmer,sbb car key programmer,sbb key programmer v33 manual,sbb key programmer v33,key programmer sbb
lara-baby
8 views

2:55
The difference between Private key and public Key || Symmetric key and Asymmetric key cryptography
Pooja Patel
10 views

16:03
Public key cryptography and Application of public key cryptography
Chirag Bhalodia
64.6K views

5:35
Requirement of Public Key cryptography | Cryptanalysis of public key cryptography
Chirag Bhalodia
12.9K views

24:11
PUBLIC KEY DISTRIBUTION || PUBLIC KEY INFRASTRUCTURE || DIFFERENT WAYS OF DISTRIBUTING PUBLIC KEYS
t v nagaraju Technical
28.2K views

17:11
RSA - Using asymmetric key cryptography with node.js (Public key cryptography)
Rafael Queiroz Gonçalves
1.7K views

32:24
public key encryption: Key distribution, message Authentication and hash function- part1
Dr. Moonther
384 views

13:16
Public Key vs Private Key | SSH Authentication | DevOps Realtime Interview Questions
DevOps and Cloud with Siva
12.4K views

18:04
Symmetric Key and Public Key Encryption | Public key Encryption hindi urdu (IT430)
theITeducation.com
897 views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

13:38
Cryptography (18CS744) Mutual authentication, one way authentication, kerberos and kerberos diff
1VA19CS061 YASHAS HM
106 views

7:14
Application of public key cryptography | Authentication | Confidentiality | Digital Signature
Chirag Bhalodia
22.5K views
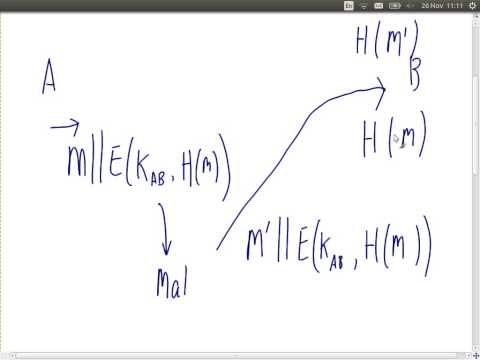
1:18:04
Authentication and Public Key Cryptography (ITS335, Lecture 5, 2013)
Steven Gordon
1.3K views
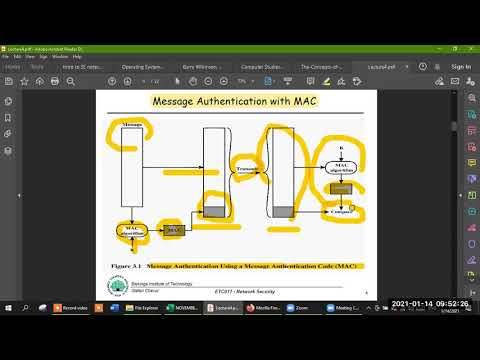
12:09
Lecture 22: Lecture 4 slides- Public key cryptography and authentication method
QZ Historia
42 views

3:11
Public key vs Private key ll Symmetric key vs Asymmetric key
Guptasmartclasses
38 views

36:43
Dasar Kriptografi PUBLIC KEY (Public Key Cryptography Basics - TryHackMe)
Recoon
14 views

0:46
What Is Public-Key Cryptography? What Is Public & Private Key?
Binance Academy
13.3K views

0:06
Read Public Key Cryptography: 4th International Workshop on Practice and Theory in Public Key
Sieglinde
0 views

20:08
Public key cryptography principles of public key cryptosystems
Ekeeda
407 views

0:06
Read Public Key Cryptography: 4th International Workshop on Practice and Theory in Public Key
Lreuter
0 views

13:19
18_Public Key Cryptography - Key pair, Secrecy and Authentication
Angayarkanni S A
238 views

2:56
Encryption key cryptography type(symmetric key cryptography & asymmetric key cryptography) in HINDI
Shukla Classes
40 views

31:18
Achieve public key cryptography using AWS KMS Asymmetric key pair and OpenSSL.
Apar Vaidyanathan
1.0K views

11:26
Distribution of Secret Key using Public Key Cryptography
Prof. sampath
181 views

0:35
Key west florida accommodations, key west vacation rentals, key west condos, key west hideaways, key west nightlife
Tommy Lee
57 views

18:08
CS14: Digital Signature in Cyber Security | Symmetric Key | Asymmetric Key| Public Key Cryptography
University Academy
37.2K views
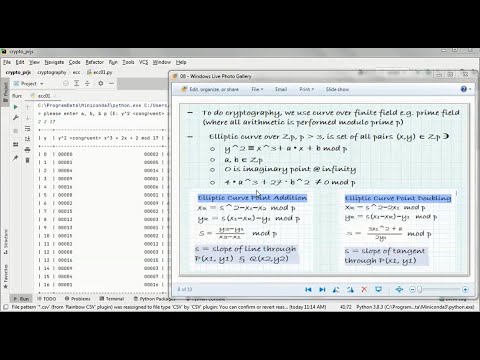
22:34
Elliptic Curve Cryptography + Python + Public Key Cryptography (public version)
Prototype Project
1.3K views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

8:37
Cryptography||Symmetric Key cryptography||Asymmetric Key Cryptography||Cryptography Notes
PPC Learning
2.3K views

1:10:42
B Level - NMIS 5 Public Key Infrastructure & Message Authentication
Online Free Education
13 views

0:05
Read Access Control Authentication And Public Key Infrastructure (Information Systems Security
Tuuli Mark
1 views

0:05
Download Access Control Authentication And Public Key Infrastructure (Information Systems Security
Maisi Baker
2 views
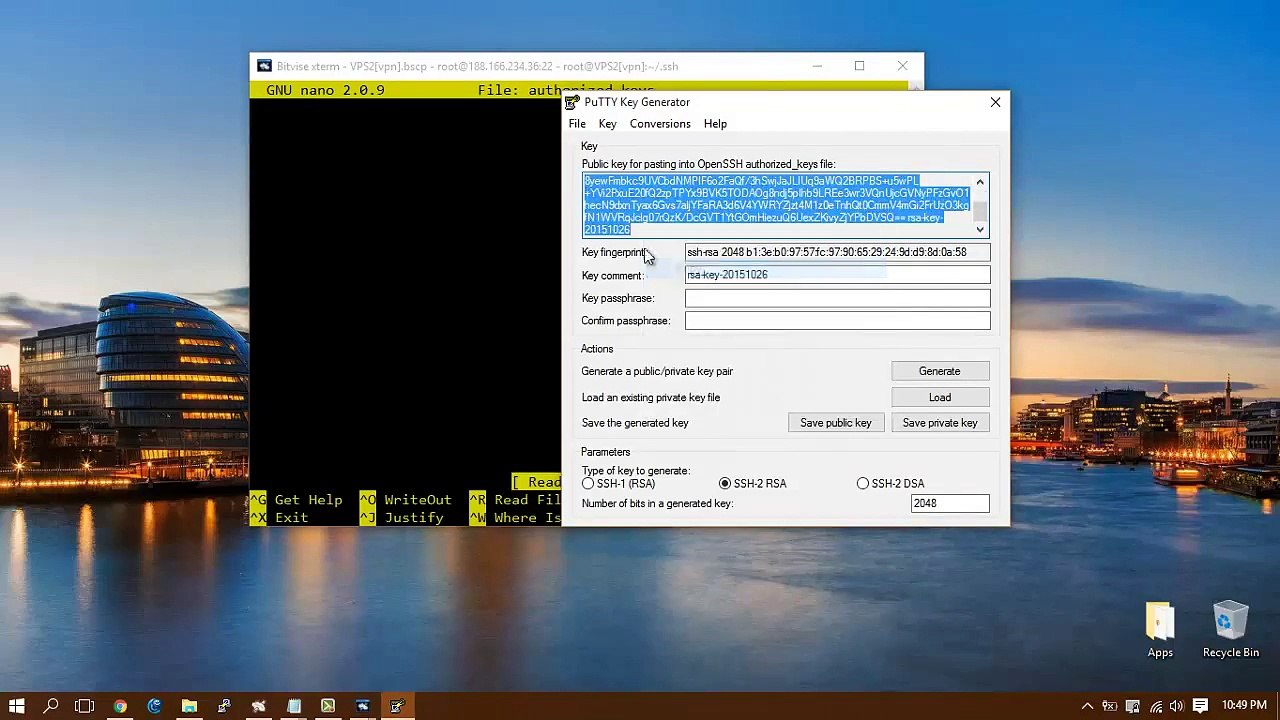
2:38
How To setup VPS with Public Key Authentication (Bitvise ssh)
panduanvps
3 views

0:30
Review ACCESS CONTROL AUTHENTICATION PUBLIC KEY INFRASTRUCTURE 2E (Jones Bartlett Learning
katewebix
1 views
Page 1