Search Results for "authentication algorithms"
Find videos related to your search query. Browse through our collection of videos matching "authentication algorithms". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "authentication algorithms"
50 results found

11:49
Authentication functions and 3 ways to produce authentication | Message authentication
Abhishek Sharma
263.4K views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

13:38
Cryptography (18CS744) Mutual authentication, one way authentication, kerberos and kerberos diff
1VA19CS061 YASHAS HM
106 views

33:46
Clustering Algorithms | Data Science Algorithms | ML Algorithms | Edureka | ML Rewind - 3
edureka!
4.0K views

1:50
Intro to Algorithms - Georgia Tech - Computability, Complexity, Theory: Algorithms
Udacity
12.0K views

8:10:27
Machine Learning Algorithms Full Course 2022🔥 | Machine Learning Algorithms Explained | Simplilearn
Simplilearn
38.0K views

0:09
Top 9 Machine Learning Algorithms 2025 | Machine Learning Algorithms for Data Science
upGrad
13.7K views

1:11:05
Machine Learning Algorithms | Machine Learning Tutorial | Data Science Algorithms | Simplilearn
Simplilearn
450.7K views

5:35:20
Machine Learning Algorithms Full Course | Machine Learning Algorithms Explained | Simplilearn
Simplilearn
42.7K views

3:09
Why algorithms are called algorithms | BBC Ideas
BBC Ideas
3.3M views

49:40
Top Hashing Algorithms In Cryptography | MD5 and SHA 256 Algorithms Explained | Simplilearn
Simplilearn
21.5K views

42:50
Machine Learning Algorithms | Machine Learning Algorithms Explained | Edureka | ML Rewind - 1
edureka!
9.4K views

0:12
Top 10 Machine Learning Algorithms for Beginners | #MachineLearning #AI #DataScience #ML #Algorithms
Yashwant Harikishan
3.7K views

2:17
Algorithms - Trailers for Algorithms
ScreenPlay
78 views

0:19
Read Python Algorithms Mastering Basic Algorithms in the Python Language EBooks Online
Fatimia Ahmad
1 views
![Practical Algorithms for 3D Computer Graphics [PDF Download] Practical Algorithms for 3D Computer](/image/s2.dmcdn.net/v/Cy7Om1e8oo9lFooXy/xx720.pagespeed.ic.s5jEwDOfN-.jpg)
0:07
Practical Algorithms for 3D Computer Graphics [PDF Download] Practical Algorithms for 3D Computer
Noorhaert819
2 views
![[PDF Download] Essential Algorithms: A Practical Approach to Computer Algorithms [PDF] Full](/image/s1.dmcdn.net/v/D4mT51clTD98dZhMP/xx720.pagespeed.ic.f_Ewt2RZfi.jpg)
0:07
[PDF Download] Essential Algorithms: A Practical Approach to Computer Algorithms [PDF] Full
Coxagawrue1
14 views

0:06
Read Combinatorial Optimization: Theory and Algorithms (Algorithms and Combinatorics) Ebook
Lfarias
0 views

0:06
Read Parallel Algorithms and Cluster Computing: Implementations Algorithms and Applications
Marjanian
1 views

0:27
Download Design and Analysis of Algorithms: First Mediterranean Conference on Algorithms, MedAlg
Mkannan
1 views

1:04
Apex Algorithms – Best Online Betting Algorithms
apexalgorithms
23 views

0:38
Algorithms Illuminated (Part 2): Graph Algorithms and Data Structures: Volume 2
joyix1234
1 views

2:01
Understanding Social Media Algorithms | How to Crack Social Media Algorithms
Digital Pratiksha
13 views

46:18
10 ML algorithms in 45 minutes | machine learning algorithms for data science | machine learning
Unfold Data Science
412.0K views

4:35
Cryptography Algorithms: Explore New Algorithms in Zero-knowledge, Homomorphic Encryption
TechExploreTerrain
50 views

19:15
#1 Quantum Algorithms & Cryptography | Quantum Algorithms & Cryptography
NPTEL-NOC IITM
15.3K views

0:18
Graph Algorithms and Applications 3 (Journal of Graph Algorithms and Applications) (No.3)
bridonjamod55
1 views

3:41
Trick to Remember Time Complexity of Sorting Algorithms | Algorithms in CSE | GATE 2024 CSE | BYJU'S
BYJU'S Exam Prep GATE & ESE: EE,EC,IN,CS
4.0K views

1:46:54
Quantum Algorithms part 2 | Fundamentals to Shor's and Grover's Algorithms, Oracles, Entanglement
Research Tech info
44 views

0:43
Quantum Resistant Algorithms - QR Algorithms Future Proofing Encryption Short
Technically U
703 views

13:39
Sorting Algorithms Time and Space Complexity | Sorting Algorithms | Big-O | Geekific
Geekific
18.7K views

0:08
Read Algorithms for Sensor Systems: 6th International Workshop on Algorithms for Sensor Systems
Tkarapetian
0 views

3:20
Advanced Algorithms and Complexity - Learn Algorithms
Leelah Zelma
42 views

28:08
Space Complexity of Algorithms - How to Calculate Space Complexity of Algorithms in Data Structures
Simple Snippets
126.0K views

0:41
Kruskal's and Prim's Algorithms explained in 30 seconds #shorts #algorithms #computerscience
VarPi
6.0K views

7:14
Application of public key cryptography | Authentication | Confidentiality | Digital Signature
Chirag Bhalodia
22.5K views

31:22
23-IP Security (IPSec) Part 1 🔐 | Authentication Header Explained | Network Security
Sundeep Saradhi Kanthety
204.7K views

51:12
Authentication-1 : MSR VTU CNC
Rohit M
41 views

1:10:42
B Level - NMIS 5 Public Key Infrastructure & Message Authentication
Online Free Education
13 views

39:03
Covid Cryptography 6: Message Authentication Codes and Authenticated Encryption
MathMesh
122 views

12:55
Types of Message Authentication | Message Encryption | Part 1 | Network Security | Hindi Urdu
Ask Faizan
4.3K views

19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views

7:01
#40 Kerberos - Authentication Protocol, Working with diagram|CNS|
Trouble- Free
304.6K views
2:16:38
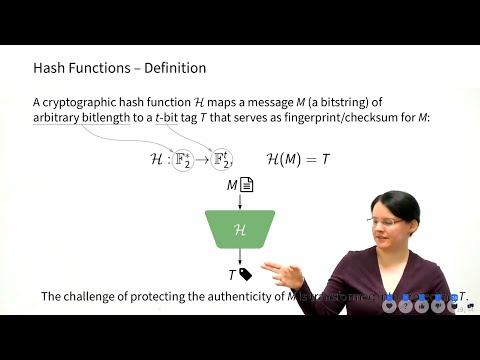
InfoSec L1 - Crypto 1 - Authentication
Maria Eichlseder
4.9K views

0:09
What is Authentication? #cybersecurity #learn #terms #cyber #security #tech
IT and Cyber Security Definitions
750 views

10:28
Module 5.2 Message Authentication Functions
bushara abdulrahim
2.9K views

20:53
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Chirag Bhalodia
33.5K views

31:30
AUTHENTICATION REQUIREMENTS_FUNCTIONS_MAC_HASH FUNCTION
IN TECH
333 views
14:09
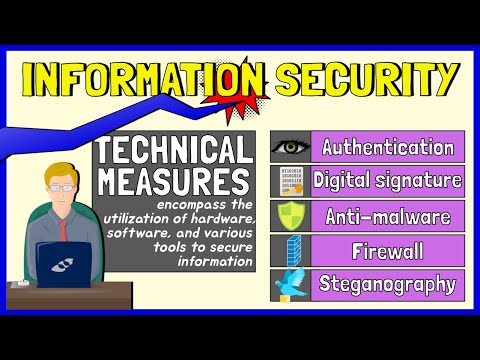
Information Security Measures (Authentication, Digital Signature, Firewalls, Steganography)
5-Minute Lessons by Victor
973 views
Page 1