Search Results for "Secure CommunicationPublic-Key Cryptography"
Find videos related to your search query. Browse through our collection of videos matching "Secure CommunicationPublic-Key Cryptography". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Secure CommunicationPublic-Key Cryptography"
50 results found

7:15
How to secure Gmail ? || Gmail ko secure kaise kare ?क्या आपका Gmail Secure है ?
DoWithMe Start Learning
1 views

0:13
Difference between unconditionally secure and computationally secure in cryptography and .....
SUKANYA BASU
973 views

4:10
Difference between Computationally Secure and Unconditional Secure Cipher | Information Security
Easy Engineering Classes
6.4K views
![Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]](/image/i.ytimg.com/vi/Hs-7ixoSqAA/xhqdefault.jpg.pagespeed.ic.BPwrxXKFrf.jpg)
41:29
Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]
Microsoft Research
77 views

0:55
Overview of Secure Aggregation #ai #artificialintelligence #machinelearning #aiagent Overview Secure
NextGen AI Explorer
12 views

8:37
SSH (Secure shell) protocol in Hindi | Secure shell protocol in Network Security
Abhishek Sharma
84.3K views

0:05
Read Secure Software and Comm. on Handheld Devices: Secure Software and Communication on Handheld
Isaksen
2 views

2:05
Secure USB Flash Drive - SanDisk Enterprise Secure ...
John Objet
1 views

4:53
Best browser for privacy 2021 | Iridium Browser | A browser securing your privacy | Most Secure Web Browsers That Protect Your Privacy | most secure browser 2021
FOCUS EXCLUSIVE
13 views

46:18
Roll Your Own Secure Cloud Storage with SSHFS - Secure Shell File System - Hak5
Hak5
5 views

3:39
Medical Coding Services | Secure Medical Coding & Secure Medical Data Handling
PDNSeek .com
5 views

0:25
A Secure Erasure Code-Based Cloud Storage System with Secure Data Forwarding
satish20059
259 views

2:09
Cryptography Skills: Building Secure Applications with Cryptography in .NET Course Preview
Pluralsight
193 views
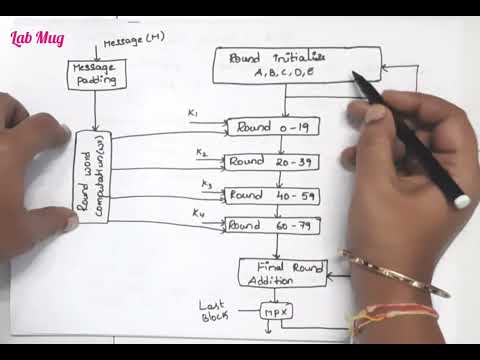
10:54
Secure Hash Algorithm (SHA) in Cryptography and Network Security #cryptography #networking #security
Lab Mug
11.2K views

0:52
What is Cryptography Domain | Aspirepod Kaushik | #shorts #podcast #cryptography #secure
Kaushik Halavadiya
358 views

3:40
What is Cryptography? | Explain Cryptography | How Cryptography Works? | Cryptography Information
Crypto & Blockchain News (CBN)
4 views
![[Cryptography] What is Cryptography? | Introduction To Cryptography | Cryptography Tutorial in Hindi](/image/i.ytimg.com/vi/8are73H9oUQ/xhqdefault.jpg.pagespeed.ic.GWwooXAHkM.jpg)
19:28
[Cryptography] What is Cryptography? | Introduction To Cryptography | Cryptography Tutorial in Hindi
Cyber Odisha
97 views

8:20
Cryptography|Cryptography in computer network | Cryptography in Matrices|Cryptography linear Algebra
Smart Studies Academy
35 views

1:15
Cryptography Projects | Cryptography Thesis | Cryptography Experts | Cryptography Projects Ideas
MatlabSimulation. Com
416 views

4:40
Cryptography|What is cryptography|Cryptography tutorial|Cryptography and network security lecture
Last Night Study
287 views

4:35
Cryptography Explained - What is Cryptography | History Of Cryptography | Types of Cryptography
Encryption Consulting LLC
404 views

0:21
Cryptography | Definition of Cryptography | What is Cryptography? | Define Cryptography
Maths With Bushra
16 views

4:03
cryptography, cryptography introduction, cryptography definition, cryptography example
Ahmad Hassan
7 views

4:17
Improved Eaack Develop Secure Intrusion Detection System For Manets Using Hybrid Cryptography
1 Crore Projects
37 views

55:35
Cryptography and Network Security Part 4/5 | WIlliam Stallings |Secure communication - S8 EC, CS,KTU
bushara abdulrahim
498 views

44:23
Blockchain Cryptography Math Explained: A Guide to the Mathematics Behind Secure Digital Ledgers
Network Technician
6 views

8:19
Breaking ECDSA (Elliptic Curve Cryptography) - rhme2 Secure Filesystem v1.92r1 (crypto 150)
LiveOverflow
78.4K views
36:07
Quantum Cryptography: How Weird Physics Could Secure Your Secrets Forever
Volkan Duran
55 views

10:22
INFORMATION SECURITY( HINDI).WHAT IS CRYPTOGRAPHY AND HOW IT WORKS TO SECURE YOUR INFORMATION.(ICT)
Computerprime
2.3K views

6:17
Secure QR-Code Based Message Sharing System Using Cryptography and Steganography
SHOAIB SHAIKH
633 views
12:01
Secure Data Transfer Based on Visual Cryptography - Part1
AmAn
30 views

14:53
Quantum Cryptography: The Future of Secure Communication
CyberSecTV
32 views
3:17
How Does No-Cloning Theorem Secure Quantum Cryptography? - Quantum Tech Explained
Quantum Tech Explained
0 views

2:44
Why Is Quantum Cryptography The Future Of Secure Communication? - Quantum Tech Explained
Quantum Tech Explained
7 views
1:33
Secure File Storage in Cloud Computing Using Cryptography in Python | Python Project Ideas
Nevon Projects
56.2K views

9:49
HAR 2009: How to use quantum cryptography for secure identification 4/6
Christiaan008
151 views

1:02
Unpacking Quantum Cryptography: Will It Secure Our Digital World?
AI BreakDown
1 views

8:02
Yubico's Post-Quantum Cryptography Revolution: Secure Digital Identity Beyond Passkeys
Creative Space
4 views

1:08:14
Cryptography: From Mathematical Magic to Secure Communication
Simons Institute for the Theory of Computing
36.1K views

0:45
Quantum Computing & Post-Quantum Cryptography Explained | Future of Secure Tech 2025
Rise Academy Career Connect
54 views

4:52
Secure File Storage On Cloud Using Hybrid Cryptography (part 1)
Awais Akbar
2.8K views

1:12
"Cryptography 101: The Secrets Behind Secure Transactions"
theblueprint
40 views

0:51
Quantum Cryptography: The Future of Secure Communication #shorts #science #technology #tech
A3TR
81 views

1:00
Quantum cryptography for secure communication
Fact Filled Shorts
6 views

5:31
Secure Cloud Data Using Hybrid Cryptography Using Python
Myra Projects
60 views

0:44
Quantum Cryptography—The Secret to Secure Communication!
Legends & Innovations
87 views
11:52
Cryptography Project - Secure Message Send
Catherine E
516 views
7:35
Intelligent cryptography approach secure distributedbig data | Final Year Projects 2016 - 2017
ClickMyProject
130 views

0:33
Unlocking Quantum Cryptography -The Future of Secure Communication #quantum #quantumcryptography
Tammi James Reflections
84 views

3:01
How Will Quantum Cryptography Secure Consumer Data? - America First Democrats
America First Democrats
0 views