Search Results for "Secure Communication Protocols"
Find videos related to your search query. Browse through our collection of videos matching "Secure Communication Protocols". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Secure Communication Protocols"
50 results found

2:47
Locking Down Data: Cryptographic Protocols for Secure Communication Explained
Operational Excellence Mastery
6 views

5:52
Study of Quantum Cryptography Protocols for Secure Quantum Communication by Brian Tey 17142084/1
Brian Tey
29 views

14:04
Quantum Protocols for Secure Communication: The Future of Digital Security
Quanten Deep-Dive Podcast
78 views

3:08
SSL and TLS Explained: Secure Communication Protocols for Web Security
CodeLucky
5 views

5:52
ISRO 2nd Test of Quantum Communication | Future of secure communication technology
Indian Defense Analysis
4.0K views
![Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]](/image/i.ytimg.com/vi/Hs-7ixoSqAA/xhqdefault.jpg.pagespeed.ic.BPwrxXKFrf.jpg)
41:29
Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]
Microsoft Research
77 views

0:05
Read Secure Software and Comm. on Handheld Devices: Secure Software and Communication on Handheld
Isaksen
2 views

7:15
How to secure Gmail ? || Gmail ko secure kaise kare ?क्या आपका Gmail Secure है ?
DoWithMe Start Learning
1 views

0:59
Protocols | meaning of Protocols
The Definition Channel
504 views

0:11
network protocols and ports | networking protocols interview questions
Technical Spartan - Thakur
149.4K views

1:21
Solar Energy - Renewable Energy - Montreal Protocols & Kyoto Protocols
Cyber Energy Ltd
11 views

0:08
Read [ AACN Protocols for Practice: Noninvasive Monitoring[ AACN PROTOCOLS FOR PRACTICE: NONINVASIVE
Airini Arono
0 views

0:05
Download Telephone Triage Protocols for Adults 18 Years and Older (Telephone Triage Protocols
MarianRench
1 views

0:35
Best product Telephone Triage Protocols for Nurses (Briggs, Telephone Triage Protocols for
walker
1 views
![[Read] TCP/IP Illustrated, Volume 1: The Protocols: The Protocols v. 1 (Addison-Wesley](/image/s2.dmcdn.net/v/Pt3_y1e9_0lvZvH-V/xx720.pagespeed.ic.GE78wmqjuE.jpg)
0:33
[Read] TCP/IP Illustrated, Volume 1: The Protocols: The Protocols v. 1 (Addison-Wesley
phamza-elhaddars
7 views

0:36
TCP/IP Illustrated, Volume 1: The Protocols: Protocols v. 1 (APC) Review
yoheg
5 views

4:37
Adherence to Covid-19 Protocols: Clamp-down on persons violating protocols begins (10-8-21)
The Multimedia group
3 views

17:04
UNIT IV-COMMUNICATION SECURITY,AUTHENTICATION PROTOCOLS
janadeep n
24 views

15:26
Security Protocols: Lecture 2e (Cryptographic Hash Functions & Communication Integrity)
Antonis M
322 views

51:05
UGC NET Paper 1 Communication | UGC NET Communication Paper 1 Mock Test By Kanupriya Mam
UGC NET Adda247
4.6K views

4:58
Wireless Communication Important Questions Anna University | EC3501 | Wireless Communication #ec3501
Bullet Nandhu
14.7K views

50:15
UGC NET Paper 1 Communication PYQs | Communication UGC NET Paper 1 PYQs | UGC NET Paper 1 PYQs
PW UGC NET
3.1K views

7:59
Communication Tips: Communication in Romantic Relationships
Teeb TV–Indie Filmmaking | Mental Tips
356 views

19:03
What is SSL? | What is SSL Ceritificate? | SSL Architecture and Protocols | Secure Socket Layer
Chirag Bhalodia
72.1K views

2:36
Provably Secure Three-Party Authenticated Quantum Key Distribution Protocols
projectsnine
861 views

4:47
Secure Protocols - CompTIA Security+ SY0-701 - 4.5
Professor Messer
71.1K views

17:54
Episode 4 | Advanced Cryptography: PKI, Digital Certificates & Secure Protocols | BCIS 4345
Joseph H.Schuessler
49 views
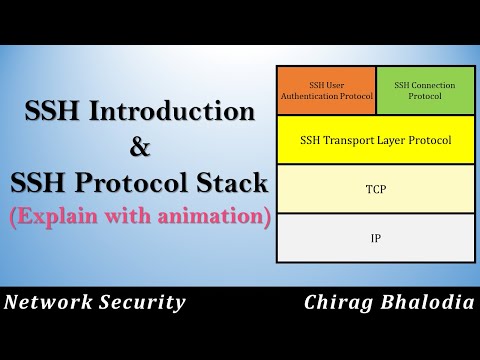
25:33
SSH | SSH Protocol Stack | SSH Protocols explain with animation | Why SSH? | Secure Shell (SSH)
Chirag Bhalodia
22.9K views
1:09:14
s-20: Cryptographic Protocols and Secure Computation II
IACR
361 views

20:31
27-Secure Socket Layer (SSL) Part 2 | Handshake & Alert Protocols | Cryptography & Network Security
Sundeep Saradhi Kanthety
90.1K views

10:27
Secure Protocols - CompTIA Security+ SY0-501 - 2.6
Professor Messer
146.7K views

23:06
Master Advanced Cryptography: Digital Certificates, PKI, & Secure Protocols | Chapter 4
Joseph H.Schuessler
67 views
3:01
How To Secure And Rotate Cryptographic Keys In Encryption Protocols?
Internet Infrastructure Explained
1 views
27:06
Secure Quantum Extraction Protocols
IACR
152 views
3:05
How Do Cryptographic Protocols Like RSA Secure Network Security? - Talking Tech Trends
TalkingTechTrends
1 views

6:09
SSL Vs TLS: Ultimate Guide to Secure Your Website Using Cryptographic Protocols
Temok Voice
26 views

7:58
Secure protocols | Encryption 101
CyberSecurityTV
7.0K views

0:06
Read Secure Multi-Party Non-Repudiation Protocols and Applications (Advances in Information
Kurtanidze 83
1 views

0:08
Read Secure Multi-Party Non-Repudiation Protocols and Applications (Advances in Information
Tbestavashvili
0 views

0:07
Read Engineering Secure Two-Party Computation Protocols: Design Optimization and Applications
Tbestavashvili
0 views
![[PDF] Efficient Secure Two-Party Protocols: Techniques and Constructions (Information Security](/image/s1.dmcdn.net/v/FVODb1e98sGL1pB3Q/x720)
0:05
[PDF] Efficient Secure Two-Party Protocols: Techniques and Constructions (Information Security
OceaNewton
3 views

5:47
Brian Tey 17142084/1 Study of Quantum Cryptography Protocols for Secure Quantum
Brian Tey
34 views

0:05
Read Secure Multi-Party Non-Repudiation Protocols and Applications (Advances in Information
Aschock
2 views

0:06
Read Efficient Secure Two-Party Protocols: Techniques and Constructions (Information Security
Bgerstner
0 views

1:07:09
s-10: Cryptographic Protocols and Secure Computation I
IACR
522 views

55:35
Cryptography and Network Security Part 4/5 | WIlliam Stallings |Secure communication - S8 EC, CS,KTU
bushara abdulrahim
498 views
19:53
Understanding Asymmetric Encryption: The Key to Secure Communication
Visualize Byte Code
9 views

14:53
Quantum Cryptography: The Future of Secure Communication
CyberSecTV
32 views

0:42
Unlocking the Quantum Internet Future of Secure Communication #quantumInternet #securecommunication
Inspiration Station
11 views

2:44
Why Is Quantum Cryptography The Future Of Secure Communication? - Quantum Tech Explained
Quantum Tech Explained
7 views