Search Results for "Secure Applications with KMS"
Find videos related to your search query. Browse through our collection of videos matching "Secure Applications with KMS". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Secure Applications with KMS"
50 results found

9:27
03 AWS Custom KMS | Import Custom Key or your Secrets into KMS | Encrypt data with custom key
Valaxy Technologies
7.7K views

7:15
How to secure Gmail ? || Gmail ko secure kaise kare ?क्या आपका Gmail Secure है ?
DoWithMe Start Learning
1 views

0:45
applications apps hotel Casa applications apps hotel Que applications apps hotel Canta
TV INTERNET
1 views

1:19
apps hotel Vídeo applications apps hotel qualquer applications apps hotel hipoteca applications
TV INTERNET
1 views

4:42
AWS KMS Key Encrypt/Decrypt 👉 Lambda Tutorial 🔥
Gokce DB
3.6K views

4:07
What Cryptographic Algorithms Does KMS Use For Security? - Cloud Stack Studio
Cloud Stack Studio
0 views

0:37
Asymmetric Encryption in AWS KMS #shorts #encryption #publickey #privatekey
RaviTeja Mureboina
170 views

31:18
Achieve public key cryptography using AWS KMS Asymmetric key pair and OpenSSL.
Apar Vaidyanathan
1.0K views

0:31
Symmetric Encryption in AWS KMS #shorts #enryption #decrypt #encrypt
RaviTeja Mureboina
925 views

1:13
Day 19 | AWS KMS Simplified | Symmetric vs Asymmetric vs Envelope 🧠
TechSaralta
160 views

3:00
Why Are Cryptographic Algorithms Crucial For KMS Data Protection? - Cloud Stack Studio
Cloud Stack Studio
0 views

10:30
AWS KMS Asymmetric Encryption and Decryption in Python Demo
Vincent Stevenson
3.7K views

8:20
26 AWS Interview Questions - What are Symmetric and Asymmetric Keys in AWS KMS
Pythoholic
1.3K views

2:43
What Is A Cryptographic Key For KMS? - Cloud Stack Studio
Cloud Stack Studio
0 views
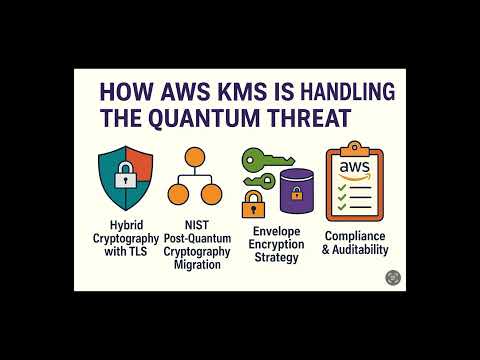
1:31
How AWS KMS Is Preparing for Quantum Computing ?
Distributed Systems
202 views
1:06
Master AWS KMS Creating Multi-Region Encryption Keys for Your Database
SuccPinn Cloud & DevOps + AI
47 views
4:00
How Do Cryptographic Algorithms Protect Your KMS Keys? - Cloud Stack Studio
Cloud Stack Studio
0 views

1:55
KMS Tools 2017-Windows 10-8.1-8-7 Permanent Activator.
MacrosSentil
1 views

15:41
Asymmetric Encryption & Digital signing using AWS KMS Explained in Hindi
CYBER SECURITY INFORMAL TALK
330 views

17:12
10. AWS In Hindi | S3 | Security | Encryption Concepts | Key Management Service KMS
Together with Abhi
3.4K views

10:22
AWS KMS Asymmetric Key Demo Create JSON Web Token Using RSA Key Pair
TrickSumo
72 views

8:28
AWS Key Management Service (AWS KMS)
Digital Cloud Training
51.3K views

14:45
Encryption with cloud kms keys
CodeFlex
5 views

40:47
🔐 AWS KMS Mastery: 🔑 Encrypt & Decrypt Data Like a Pro 🚀 | Full Hands-On Guide 🖥️
KodeHorizen
88 views

0:28
KMS Tools 2017 - Microsoft Office 2013-2016 Activator.
Piyosi Softy
18 views
0:25
KMS Tools 2017 - Microsoft Office 2013- 2016 Activator.
MaroliJusta
67 views
0:23
KMS Tools 2017 - MS Office 2013-2016 Activator.
TonyKraizen
2 views
1:10
Windows & Office KMS Activation Tools 2017.
JudsonCracks
11 views

0:41
KMS TOOLS 2017 - ALL WINDOWS & OFFICE ACTIVATOR.
Piyosi Softy
397 views
0:25
KMS Tools 2017 Portable - MS Office 2013-2016 Activator.
TonyKraizen
3 views

1:00
I traveled 4777 Kms for Fried Chicken!!😮😋
Cassius Clyde Pereira
14.7M views

4:33
Windows 8 Permanent Activation (Phone Activation)(NO KMS)
betchay
754 views

4:48
KMS Activador de Office
KMS Activador de Office
10.0K views

0:58
Future of Ev’s after 8yrs and 1,60,000 kms explained by Anand Kulkarni #motorbyte #automobile
MotorByte
1.3M views

5:34
Cyclisme - E3 Saxo Classic 2025 - Mathieu van der Poel large vainqueur après un raid solo de 40 kms... Wout Van Aert a déçu
Cyclism'Actu TV
46.5K views

0:13
Difference between unconditionally secure and computationally secure in cryptography and .....
SUKANYA BASU
973 views

8:37
SSH (Secure shell) protocol in Hindi | Secure shell protocol in Network Security
Abhishek Sharma
84.3K views

46:18
Roll Your Own Secure Cloud Storage with SSHFS - Secure Shell File System - Hak5
Hak5
5 views

4:10
Difference between Computationally Secure and Unconditional Secure Cipher | Information Security
Easy Engineering Classes
6.4K views

0:55
Overview of Secure Aggregation #ai #artificialintelligence #machinelearning #aiagent Overview Secure
NextGen AI Explorer
12 views

2:05
Secure USB Flash Drive - SanDisk Enterprise Secure ...
John Objet
1 views

0:05
Read Secure Software and Comm. on Handheld Devices: Secure Software and Communication on Handheld
Isaksen
2 views

3:39
Medical Coding Services | Secure Medical Coding & Secure Medical Data Handling
PDNSeek .com
5 views

4:53
Best browser for privacy 2021 | Iridium Browser | A browser securing your privacy | Most Secure Web Browsers That Protect Your Privacy | most secure browser 2021
FOCUS EXCLUSIVE
13 views

0:25
A Secure Erasure Code-Based Cloud Storage System with Secure Data Forwarding
satish20059
259 views
![Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]](/image/i.ytimg.com/vi/Hs-7ixoSqAA/xhqdefault.jpg.pagespeed.ic.BPwrxXKFrf.jpg)
41:29
Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]
Microsoft Research
77 views

2:09
Cryptography Skills: Building Secure Applications with Cryptography in .NET Course Preview
Pluralsight
193 views

3:57
Module 4.2 Applications of Public key cryptosystems|S8 ECE|SECURE COMMUNICATION KTU|ECT434
bushara abdulrahim
2.6K views

0:07
Read Chaos Synchronization and Cryptography for Secure Communications: Applications for Encryption
Kkrantz
4 views

10:11
Quantum network applications - A roadmap toward a secure and private quantum world
France Quantum
62 views