Search Results for "Remote User Authentication Using Public Keys"
Find videos related to your search query. Browse through our collection of videos matching "Remote User Authentication Using Public Keys". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Remote User Authentication Using Public Keys"
50 results found

1:48
Public Speaking | Public Speaking For Beginners | How to Master Public Speaking |How To Improve Public Speaking | Basics Of Public Speaking | Public Speaking and Presentation | Public Speaking For Beginners | How To Talk Confidently
Self Learning Videos
4 views

20:53
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Chirag Bhalodia
33.5K views

13:49
Remote User Authentication using Asymmetric Encryption in Network Security | Woo and Lam Proposal
Chirag Bhalodia
30.0K views

8:37
Remote user authentication using symmetric encryption
Anand Pashupatimath
4.6K views

9:47
We Remote Control Real Human - 100% Real || Remote Control man || Remote man
RANGOLI TV
13 views

21:42
Remote User Authentication: Principles & Techniques | Cryptography- #21is71 #cryptography #vtupadhai
VTU padhai
4.0K views

20:25
INS: Unit-9 Remote User-Authentication (Kerberos)
Twinkal Patel
423 views

58:47
Kerberos Version 4 & 5 and Remote User Authentication with Asymmetric Encryption -#21is71 VTU 7thsem
VTU padhai
2.3K views

3:32
Public and Private Keys - Public Key Cryptography - SSH Keys - Public Key RSA Encryption Decryption
Cloud Concepts
48 views

11:49
Authentication functions and 3 ways to produce authentication | Message authentication
Abhishek Sharma
263.4K views

5:15
How Crypto wallets work | 🗝🔐Private keys & Public Keys | Private aur Public key kya hai | Hindi/Urdu
Haroon VOICE
816 views

4:50
Web 3 Tech Series - Public Key Cryptography - What are secret keys and public keys?
Hubel Labs
116 views

2:46
USER AUTHENTICATION USING CRYPTOGRAPHY AND STEGANOGRAPHY FOR WEB APPLICATIONS
Gagan Suneja
214 views

3:53
Signing using asymmetric keys | Public & Private Keys and Digital Signatures |Network Security
Software Systems
580 views

24:11
PUBLIC KEY DISTRIBUTION || PUBLIC KEY INFRASTRUCTURE || DIFFERENT WAYS OF DISTRIBUTING PUBLIC KEYS
t v nagaraju Technical
28.2K views

23:53
(Mario) The Music Box part 3 - Keys keys keys...
RobBoberty
2 views

1:05
X-keys USB Stick Keys with 16 programmable keys Review
Ardellaii
26 views

0:21
IRCTC User Id & password kaise banaye Hindi #How to create IRCTC user is & password
BIKASH 4888
3.1M views

8:22
How to input data from keyboard in python | keyboard input in python | read data from keyboard | python practically | easy way of python programming | python basics | read data from user | input from user in python | input function in python
ALL IN ONE
8 views

14:01
VB.NET Creating Login with Admin & User (User Level)
Codinger Tutorial
14 views

5:39
How to input data from keyboard in python | keyboard input in python | read data from keyboard | python practically | easy way of python programming | python basics | read data from user | input from user in python | input function in python
ALL IN ONE
1 views

1:01
Lg ac remote demo in hindi // lg ac remote function
Home Appliances market
1.7M views
4:10
Remote - calm down remix (wire Oh) #Rippers Boss Datt# song Written by:remote
DARK3M VEVO
302.4K views

0:39
Does not work remote control JCB remote #shorts #experiment #entertainment
Mk HACKER
25.7K views

0:05
Download Physical Principles of Remote Sensing (Topics in Remote Sensing) PDF Free
Vfonseca
2 views

3:21
Remote Coder Positions | Remote Medical Coding Job Tips
PDNSeek .com
41 views

4:23
Remote control differences and best remote control
john info
4 views

0:19
8k Tv | Samsung Neo QLED solar-cell remote #samsung #remote #smartgadgets #8k
The Box Show
445.7K views

9:54
Valie Export: .......remote........remote (1973)
Filmow
1.4K views

23:47
Remote-Controlled Semi Truck?! Testing Scania’s New Pro Remote 2.0
Bruce Wilson
35.6K views

19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views

0:30
About For Books Mechanics of User Identification and Authentication: Fundamentals of Identity
dm_09d226e7605f9f5a1a3a6425e52120d4
0 views

4:27
Introduction to User Authentication - CompTIA Network+ N10-005: 5.3
Professor Messer
15.0K views

1:09:38
CSE571-11-15B: User Authentication Protocols (Part 2 of 3)
Raj Jain
1.8K views

0:40
Why Continuous User Authentication Matters
CyberGuard
1 views

0:27
Unlocking the Secrets of User Authentication
CyberGuard
0 views
13:31
Build Node.js User Authentication - Password Login
Web Dev Simplified
565.0K views

0:51
Public Keys vs Private Keys 🔑 Crypto Wallets Explained! 🚀 (In 50 Seconds! 👍) #cryptocurrency
Crypto Casey
11.3K views

7:24
Symmetric Keys, Asymmetric Keys, Public Key Encryption And Man In The Middle Attack
Akshay N
18 views

0:48
What are Public Keys & Private Keys in #Crypto #cryptowallet
Sahicoin
9.0K views

1:00
What are Keys in Blockchain? | Public Key and Private Key | Crypto Keys? | Describedot | Day 11
Describedot
9.1K views

0:40
Public keys vs. Private keys (in less than a minute 😉)
Trezor
1.7K views

7:31
Private Keys & Public Keys: Grundlagen der Kryptographie & Sicherheit im Bitcoin-Netzwerk | 005
BTC Vision
15 views

0:59
Public Keys vs. Symmetric Keys: Security for Everyone, Everywhere
Zcash Media
1.0K views

3:49
Was sind Public Keys, Private Keys und Wallet Adressen? | Lesson 7 Bitpanda Academy
Bitpanda
2.7K views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

13:38
Cryptography (18CS744) Mutual authentication, one way authentication, kerberos and kerberos diff
1VA19CS061 YASHAS HM
106 views

6:23
Secrecy and Authentication using Public-Key/Two-Key Cryptography or Asymmetric Encryption
CSE Adil
86 views
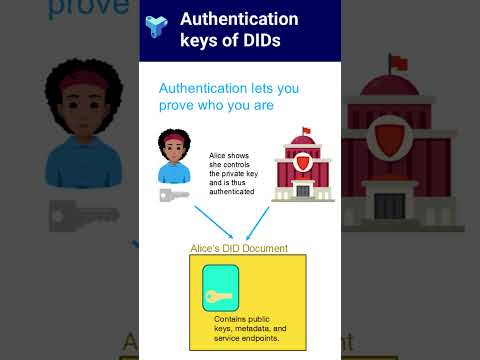
0:59
Authentication keys
LF Decentralized Trust
278 views
Page 1