Search Results for "Privacy and Secrecy"
Find videos related to your search query. Browse through our collection of videos matching "Privacy and Secrecy". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Privacy and Secrecy"
50 results found

1:21
What is the Difference Between Secrecy and Privacy | Secrecy Vs. Privacy | InfosecTrain
INFOSEC TRAIN
569 views

4:53
Best browser for privacy 2021 | Iridium Browser | A browser securing your privacy | Most Secure Web Browsers That Protect Your Privacy | most secure browser 2021
FOCUS EXCLUSIVE
13 views

56:30
IMA Public Lectures : Secrecy, privacy, and deception: the mathematics of cryptography; Jill Pipher
IMA UMN
970 views

0:51
The Dawn of Digital Privacy: From Secrecy to Encryption
TechMetamorph
12 views

15:24
You want Privacy? Ditch iOS and Android and use the best privacy phone (2025 edition)
David Bombal
125.8K views

0:23
Read IT-Security and Privacy: Design and Use of Privacy-Enhancing Security Mechanisms (Lecture
Sophia Tran
0 views

0:07
Read Cyber Security and Privacy: 4th Cyber Security and Privacy Innovation Forum CSP Innovation
Nigoghosian
2 views

0:07
Download Cyber Security and Privacy: 4th Cyber Security and Privacy Innovation Forum CSP Innovation
Artzouig
1 views

0:57
Extreme Privacy and how to be Invisible online #shorts #privacy #wifi #iphone #android
David Bombal
103.7K views

2:04
Digital Privacy and the Right to be Protected | Protect Digital Privacy
2 Minute Teachables
639 views

1:30
Privacy meaning in Hindi | Privacy ka kya matlab hota hai | daily use English words
Worldwide Spoken English By VS
152.2K views

5:21
WhatsApp Advanced Chat Privacy Kya Hai | WhatsApp New Update Advanced Chat Privacy Update | On Off
Sikhe All In Hindi
65.9K views

6:08
Advanced Chat Privacy in WhatsApp Kya Hai, WhatsApp Advanced Chat Privacy Kya Hota Hai & How to Use
Sikhe All In Hindi
75.5K views

0:30
Whatsapp Advanced Chat Privacy | Whatsapp Advanced Chat Privacy Kya Hota Hai | #youtubeshorts
Kajal Mishra
98.4K views

2:25
Whatsapp Advanced Chat privacy kya hai | Whatsapp new update advanced chat privacy update 🔥
Fabing Tech
155.4K views

0:54
Unlocking privacy's future #encryption #privacy #history
Laura jackson
630 views

1:42
What is Privacy in Meet | Google Meet me Privacy in meet kya hota hai
Techsore 2
105.3K views
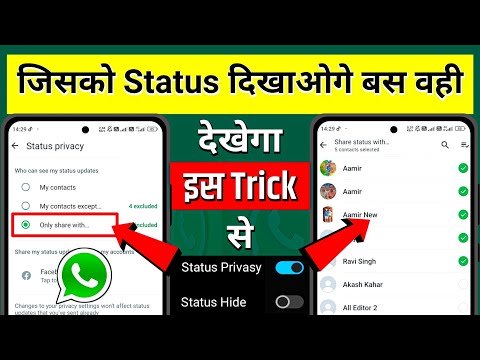
3:27
📲 Whatsapp Status Privacy Only Share With Kya Hota Hai | Whatsapp Status Privacy | Only Share With
SunnyTechTricks
126.6K views

0:40
🔐 ZK-SNARKs Explained: Privacy & Scalability in Crypto! 🚀#ethereum #tech #privacy #crypto
BitnByte Mining
213 views

1:17
Privacy Policy: How to Create A Privacy Policy for Your ...
Jonathan
46 views
0:22
Discover the best tools for digital privacy #privacy#digitalprivacy #cybersecurity
AI-Assist
2.0K views

14:01
Privacy in digital world, Basics of GDPR, Personal Data, Digital Privacy, Emerging Technologies, mba
DWIVEDI GUIDANCE
18.6K views

1:40
Privacy Eraser Serial (privacy eraser portable 2015)
Amy Jones
226 views

0:15
How to off privacy protection password on Redmi || privacy protection password setting #shorts
Amol BhauTech-4
739.6K views

0:39
Elon Musk's X Faces EU Privacy Complaints Over AI Data Use. Nine EU Countries File Complaints Against Platform for Privacy Breaches.
Benzinga
17.6K views

4:18
RSA Key Exchange and Forward Secrecy - Cryptography Essentials
Practical Networking
6.7K views

6:05
Secure Pixel Secrecy Embedding Secret Keys with Python and LSB Steganography in Images
1Crore Projects
4 views

5:43
Cryptography, Perfect Secrecy and One Time Pads | Two Minute Papers #25
Two Minute Papers
14.3K views

5:50
how to encrypt and decrypt in online | Malayalam|Secrecy Armor |
Secrecy Armor
28 views

13:19
18_Public Key Cryptography - Key pair, Secrecy and Authentication
Angayarkanni S A
238 views

6:23
Secrecy and Authentication using Public-Key/Two-Key Cryptography or Asymmetric Encryption
CSE Adil
86 views

0:31
FYF - MAT198H1S - Cryptology: The Mathematics of Secrecy and Security
Innis Registrar
499 views

13:00
Diffie-Hellman Key Exchange and Forward Secrecy
Practical Networking
10.2K views

1:05:04
Public Key Cryptography: Secrecy in Public - Professor Raymond Flood
Gresham College
14.0K views

3:56
Code Girls, Once Sworn To Secrecy, Honored Publicly For Their Service | Sunday TODAY
TODAY
25.6K views

25:54
Cryptography:Zero-Knowledge Proofs, Perfect Secrecy, Caesar Cipher
Mr Sam
35 views

15:54
How LIC’s Secrecy Came Full Circle — From Mundhra to Adani
Moneylife News Bites
29.1K views

11:38
Substitution Cipher -The science of secrecy 01
NPTEL-NOC IITM
63.1K views

0:49
Used Ciphered Letters to Maintain Secrecy #facts #history
MAFIAOVERDOSE
414 views

1:05:04
Public Key Cryptography Secrecy in Public │ Professor Raymond Flood │
Documentary HD Full
24 views
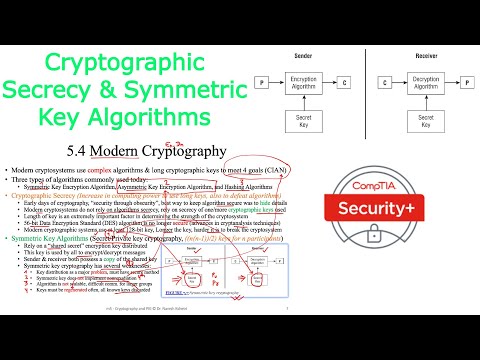
7:13
Cybersecurity | Cryptography Secrecy | Symmetric Key Algorithm
Naresh KSHETRI
187 views

4:12
Perfect secrecy | Journey into cryptography | Computer Science | Khan Academy
Khan Academy Labs
149.3K views

0:05
Read Books The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography
Melodytuten
0 views
![Full [PDF] Downlaod The Code Book: The Evolution of Secrecy from Mary, Queen of Scots to Quantum](/image/s2.dmcdn.net/v/GwR-u1e1L1Amganq9/xx720.pagespeed.ic.D73X8O1f0F.jpg)
0:17
Full [PDF] Downlaod The Code Book: The Evolution of Secrecy from Mary, Queen of Scots to Quantum
jobin
1 views

0:33
The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography Best Sellers
vomlivodre
4 views

0:30
Full version The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography
dm_1d39b47814cb28198d112c168fe848ba
5 views

17:23
Science of Secrecy -edited
f544044714
58 views

5:31
Introduction to Cryptography: Perfect Secrecy
Wolfram U
1.3K views

3:38
Perfect Forward Secrecy - CompTIA Security+ SY0-401: 6.1
Professor Messer
36.2K views

31:25
Lec 5|| Perfect Secrecy Part II#fahadusman#cryptography
fahad osman
965 views
Page 1