Search Results for "One-Way Authentication"
Find videos related to your search query. Browse through our collection of videos matching "One-Way Authentication". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "One-Way Authentication"
50 results found

11:49
Authentication functions and 3 ways to produce authentication | Message authentication
Abhishek Sharma
263.4K views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views
1:06:45
Gravitation | NEET All PYQs 07: Gravitation | Physics | Physics NEET | Gravitation One Shot, Gravitation One Shot NEET PYQs, NEET PYQs Gravitation One Shot, Physics NEET PYQs Gravitation One Shot AK Sir, #AKSir #aksir #neet #neetphysics #physicsneet
sun ray
10 views

10:57
One Night Ending Explained | One Night Season 1 | One Night Australian Series | one night paramount
UlTiMaTe ChAnGe FoR LiFe
210 views

1:04:28
Cryptography and Network Security BCS072 Unit 3 One shot | Message Authentication Codes Unit 3 AKTU
EduShine Classes - Arman Ali
273 views

0:31
Visual OTP: The Visual One Time Password Authentication Protocol
Visual OTP
462 views

5:55
Two Step Verification? Otp? Two Step Authentication? One Time Passwords Explained
TechInfoEdu
2 views

9:08
Custom one hot encoding | one hot encoding without any library | one hot encoder without sklearn
Hope In Data Science
112 views

7:04
G.One & Ra.One In Action | RA.One | Shah Rukh Khan
Eros Now Music
119.0M views
8:29
Latest Android-One smartphone ⚡⚡| Cheapest budget android-One smartphone #android #android-one #stock-android
AB Multimedia
37 views

1:37:20
One Night, One Baby, One Forever
Short TZ
991 views
3:55
One Man -- One Woman -- One Person by Sheikh Tawfique Chowdhury
Rehan Ahmed
272 views

1:48:06
One Night, One Mistake, One Forever
Shortmovies68
340 views

7:14
Application of public key cryptography | Authentication | Confidentiality | Digital Signature
Chirag Bhalodia
22.5K views

31:22
23-IP Security (IPSec) Part 1 🔐 | Authentication Header Explained | Network Security
Sundeep Saradhi Kanthety
204.7K views

51:12
Authentication-1 : MSR VTU CNC
Rohit M
41 views

1:10:42
B Level - NMIS 5 Public Key Infrastructure & Message Authentication
Online Free Education
13 views
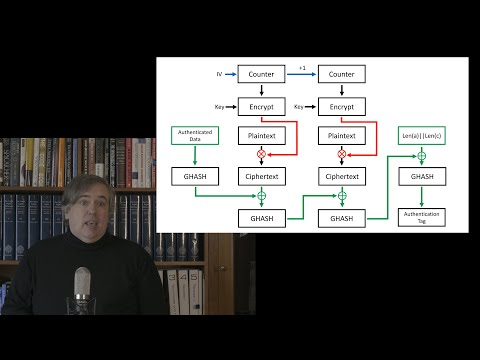
39:03
Covid Cryptography 6: Message Authentication Codes and Authenticated Encryption
MathMesh
122 views

12:55
Types of Message Authentication | Message Encryption | Part 1 | Network Security | Hindi Urdu
Ask Faizan
4.3K views

19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views

7:01
#40 Kerberos - Authentication Protocol, Working with diagram|CNS|
Trouble- Free
304.6K views

2:16:38
InfoSec L1 - Crypto 1 - Authentication
Maria Eichlseder
4.9K views

0:09
What is Authentication? #cybersecurity #learn #terms #cyber #security #tech
IT and Cyber Security Definitions
750 views

10:28
Module 5.2 Message Authentication Functions
bushara abdulrahim
2.9K views

20:53
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Chirag Bhalodia
33.5K views

31:30
AUTHENTICATION REQUIREMENTS_FUNCTIONS_MAC_HASH FUNCTION
IN TECH
333 views

14:09
Information Security Measures (Authentication, Digital Signature, Firewalls, Steganography)
5-Minute Lessons by Victor
973 views
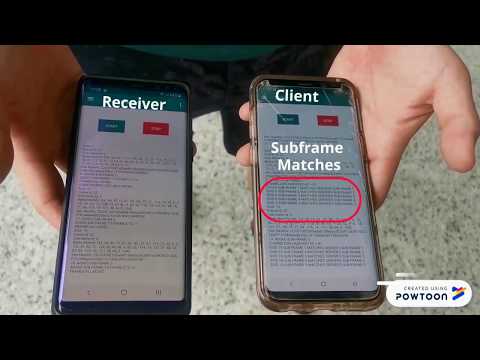
1:05
Fast Authentication using Chameleon Hashing Key Chain
University of Glasgow Singapore
229 views

12:54
Authentication Functions | Cryptography and Network Security
Ekeeda
910 views
1:04:39
Message authentication and hash functions (part-1)
Keerthi Humsika K
58 views
16:37
Message Authentication using Hash Functions - Network Security
Lectures by Shreedarshan K
4.3K views

11:14
Authentication Methods - SY0-601 CompTIA Security+ : 2.4
Professor Messer
136.2K views

18:07
Lecture 23: Public key cryptography and authentication method Asymmetric Key Requirements
QZ Historia
41 views
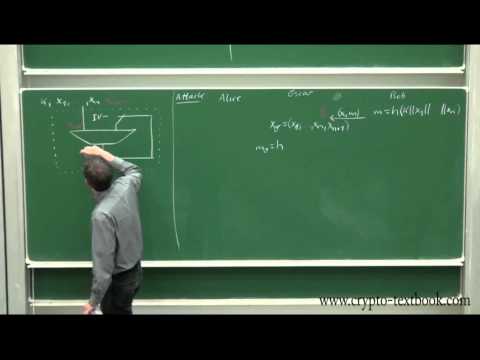
1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views
1:04:18
Assumptions of Encryption and Authentication (ITS335, L04, Y15)
Steven Gordon
1.2K views

9:11
Security goals of Cryptography (Authentication, Integrity, confidentiality and, Repudiation) Hindi.
Helping Tutorials
12.1K views

1:19:10
Authentication with Symmetric Key Crypto and MACs (CSS322, L17, Y14)
Steven Gordon
1.5K views

40:57
13-Message Authentication in Cryptography 🔐 | MAC vs Hash Functions vs Encryption
Sundeep Saradhi Kanthety
234.7K views

1:00
Authentication vs Authorization
A Binary Code
92.8K views

13:01
Message Authentication Code MAC
Ekeeda
284 views

2:46
USER AUTHENTICATION USING CRYPTOGRAPHY AND STEGANOGRAPHY FOR WEB APPLICATIONS
Gagan Suneja
214 views

10:56
CS409(Mod4_1): Message Authentication and requirements - Module 4 -Cryptography and network security
Greeshma G S
11.7K views

0:47
Biometric Authentication in Cybersecurity
Tomorrow’s Tech Today
17 views
1:18:04
Authentication and Public Key Cryptography (ITS335, Lecture 5, 2013)
Steven Gordon
1.3K views
14:06
Authentication Bangla tutorial 2 : encrypting database
Anisul Islam
5.3K views

22:09
PhotoProof: Cryptographic Image Authentication for Any Set of Permissible Transformations
IEEE Symposium on Security and Privacy
851 views

19:58
V4a: Message authentication codes: Fundamental concepts (Applied Cryptography 101)
Cryptography 101
736 views

28:39
Symmetric-key cryptography VII - Message authentication codes (MACs)
Tanja Lange: Cryptology
191 views

12:09
Lecture 22: Lecture 4 slides- Public key cryptography and authentication method
QZ Historia
42 views