Search Results for "Null Authentication"
Find videos related to your search query. Browse through our collection of videos matching "Null Authentication". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Null Authentication"
50 results found

4:44
rh-null golden blood|rh-null the rarest blood type| rh null blood secrets| Rare blood group in the world|real golden blood|golden blood power|golden blood dangerous| blood group finding| #bloodgroup
levelup4u
32 views

1:46
Agent Null Null Nix Trailer OV
FILMSTARTS
267 views

11:49
Authentication functions and 3 ways to produce authentication | Message authentication
Abhishek Sharma
263.4K views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

13:38
Cryptography (18CS744) Mutual authentication, one way authentication, kerberos and kerberos diff
1VA19CS061 YASHAS HM
106 views

14:41
Hypothesis Testing and The Null Hypothesis, Clearly Explained!!!
StatQuest with Josh Starmer
741.7K views

0:36
NULL, FIN and Xmas | Answer the Questions Series #shorts #thm #tryhackme
CyberTodd
429 views

5:45
Steganography & Null Ciphers In CISSP ISC2
Cybernous
248 views
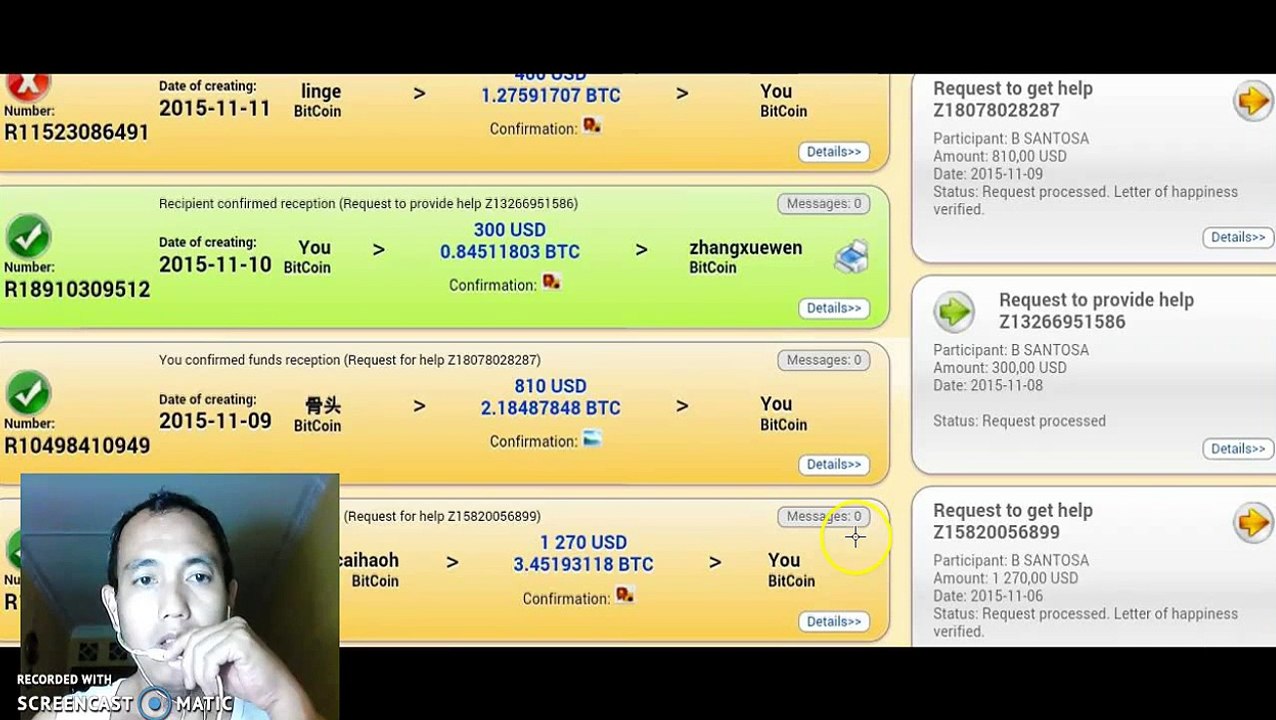
0:43
#HashTags: null
WEILI
11 views

0:47
Kap. Einführung 02 die Null, das Nichts
ziesche_de
2 views

10:33
PTI chief’s jail trial in cipher case declared ‘null and void’ - Law Experts' Analysis
ARY NEWS
6 views

11:57
Wie ich Programmieren lernen würde (Wenn ich von null starte)
Programmieren lernen
366.8K views

18:50
Indistinguishability Obfuscation of Null Quantum Circuits and Applications
Simons Institute for the Theory of Computing
141 views

0:06
POV: Du vertraust ChatGPT NULL bei Mathe 😵💫 #mathe #shorts
Studytime
24 views

42:58
Co-planar vectors | concurrent vectors | Null/zero vectors | unit vector | standard unit vector | polar vectors | Axial vectors #cityclasses
cityclasses
18 views
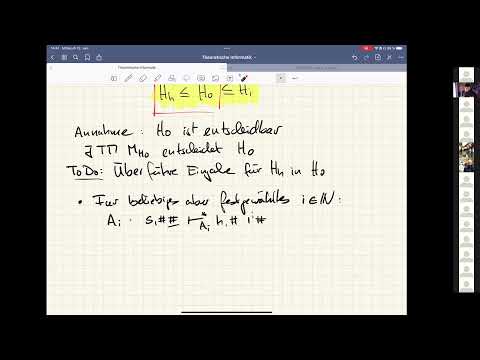
28:00
20220112 TI Aufzeichnung 12.1.22: Reduktion Spezielles Halteproblem auf Null-Halteproblem
Karsten Morisse
340 views

6:02
Zero Vector or Null Vector
Avinash Kishor (AVN sir)
1 views

0:35
About For Books Reason Rigor: How Conceptual Frameworks Guide Research (NULL) For Free
RoseDavis1707
0 views

7:48
Lec-54: Remove Null Production from CFG (Context Free Grammar) with example in Hindi
Gate Smashers
506.0K views

6:52
Hypothesis Testing - Null and Alternative Hypotheses
The Organic Chemistry Tutor
825.0K views

0:11
Hypothesis | Null & Alternative Hypothesis | Research Aptitude Part-7 | Nta Net Paper-1 (unit-2).
Nta Net Preparation
715.7K views

14:52
Null and Alternate Hypothesis - Statistical Hypothesis Testing - Statistics Course
Math and Science
2.1M views
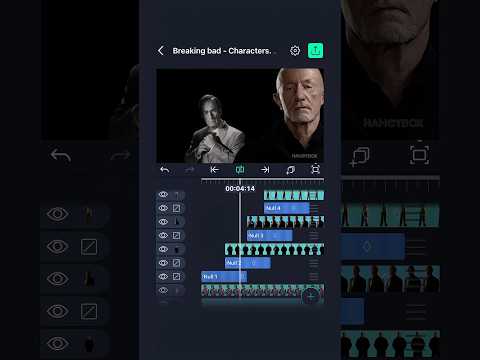
0:17
Null Control Like Ae In alight motion. | #alightmotiontutorial #breakingbad #editingtutorial
Hancybox
415.5K views

18:07
Identity Matrix, symmetric Matrix, Idempotent Matrix , Null Matrix. #NTA #NetEconomics #JRF #IES
ECON MATHS
1.0K views

7:14
Application of public key cryptography | Authentication | Confidentiality | Digital Signature
Chirag Bhalodia
22.5K views

31:22
23-IP Security (IPSec) Part 1 🔐 | Authentication Header Explained | Network Security
Sundeep Saradhi Kanthety
204.7K views

51:12
Authentication-1 : MSR VTU CNC
Rohit M
41 views

1:10:42
B Level - NMIS 5 Public Key Infrastructure & Message Authentication
Online Free Education
13 views

39:03
Covid Cryptography 6: Message Authentication Codes and Authenticated Encryption
MathMesh
122 views

12:55
Types of Message Authentication | Message Encryption | Part 1 | Network Security | Hindi Urdu
Ask Faizan
4.3K views

19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views

7:01
#40 Kerberos - Authentication Protocol, Working with diagram|CNS|
Trouble- Free
304.6K views

2:16:38
InfoSec L1 - Crypto 1 - Authentication
Maria Eichlseder
4.9K views

0:09
What is Authentication? #cybersecurity #learn #terms #cyber #security #tech
IT and Cyber Security Definitions
750 views

10:28
Module 5.2 Message Authentication Functions
bushara abdulrahim
2.9K views

20:53
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Chirag Bhalodia
33.5K views

31:30
AUTHENTICATION REQUIREMENTS_FUNCTIONS_MAC_HASH FUNCTION
IN TECH
333 views

14:09
Information Security Measures (Authentication, Digital Signature, Firewalls, Steganography)
5-Minute Lessons by Victor
973 views

1:05
Fast Authentication using Chameleon Hashing Key Chain
University of Glasgow Singapore
229 views

12:54
Authentication Functions | Cryptography and Network Security
Ekeeda
910 views

1:04:39
Message authentication and hash functions (part-1)
Keerthi Humsika K
58 views

16:37
Message Authentication using Hash Functions - Network Security
Lectures by Shreedarshan K
4.3K views

11:14
Authentication Methods - SY0-601 CompTIA Security+ : 2.4
Professor Messer
136.2K views

18:07
Lecture 23: Public key cryptography and authentication method Asymmetric Key Requirements
QZ Historia
41 views

1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views

1:04:18
Assumptions of Encryption and Authentication (ITS335, L04, Y15)
Steven Gordon
1.2K views

1:04:28
Cryptography and Network Security BCS072 Unit 3 One shot | Message Authentication Codes Unit 3 AKTU
EduShine Classes - Arman Ali
273 views

9:11
Security goals of Cryptography (Authentication, Integrity, confidentiality and, Repudiation) Hindi.
Helping Tutorials
12.1K views

1:19:10
Authentication with Symmetric Key Crypto and MACs (CSS322, L17, Y14)
Steven Gordon
1.5K views