Search Results for "Network Integrity"
Find videos related to your search query. Browse through our collection of videos matching "Network Integrity". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Network Integrity"
50 results found

0:06
Read Integrity Primitives for Secure Information Systems: Final RIPE Report of RACE Integrity
Chikovani 1981
1 views

2:31
{Integrity For All} Ephesians 320 and {Integrity For All}
Lisa Streeter
2 views

0:46
CIA TRIAD | INTEGRITY | AUTOMOTIVE CYBER SECURITY #ciatriad #automotivecybersecurity #integrity
UpSkill
206 views

2:14
No Integrity In Integrity Comission
CCNTV6
244 views

7:52
Security Goals - Confidentiality, Integrity and Availability - Cryptography and Network Security
Dr. Faheem Mushtaq
198 views

5:33
Network Security Goals :Confidentiality, Integrity, Availability |CIA Triad in Cryptography hindi
DK Technical Point 2.0
2.0K views

4:06
Security Goals in Cryptography Network Security | CIA Traid | Confidentiality Integrity Avalaibility
Techystudy Best Learning Online
240 views

23:56
What Is Network Security? | Introduction To Network Security | Network Security Tutorial|Simplilearn
Simplilearn
124.2K views

40:38
Cryptography in network (Network security basics) |Lecture 25| Data Communication & Computer Network
Mateen Yaqoob
58 views

1:55
Retina Network Security Scanner - Conficker Worm Serial - Retina Network Security Scanner - Conficker Wormretina network security scanner conficker worm (2015)
Jose Sanchez
2 views

6:33
What Is Network Marketing Network Marketing Explained! What Is Network Marketing Anyways
Most Popular Videos
1 views

11:37
What is Pi Network | Pi Network in Pakistan | Pi Network kya Hai | Pi Cryptocurrency Review in urdu
90s Mentor
25 views

14:06
CRYPTOGRAPHY AND NETWORK SECURITY NOTES | NETWORK SECURITY NOTES | NETWORK SECURITY
DIVVELA SRINIVASA RAO
382 views

6:02
Network Security Model | Network security model in cryptography | Network Security
Chirag Bhalodia
22.5K views

8:25
Cryptography and Network Security Unit 1- Part 5 | Network Security & Network Access Security Models
TN55 RLE
442 views

7:54
Network Marketing Nedir, Neden Network Marketing, Network Marketing Gerçeği
musaduman
3 views

45:59
01731, Network Steganography / Network Information Hiding, Chapter 7a Network-level Countermeasures)
Steffen Wendzel
812 views
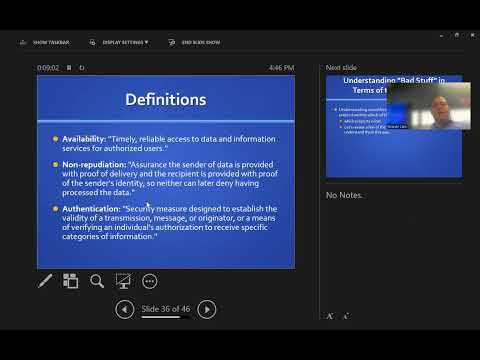
34:32
Cryptography Fundamentals: Confidentiality, Integrity, & Non-Repudiation Explained
Ricardo Calix
32 views
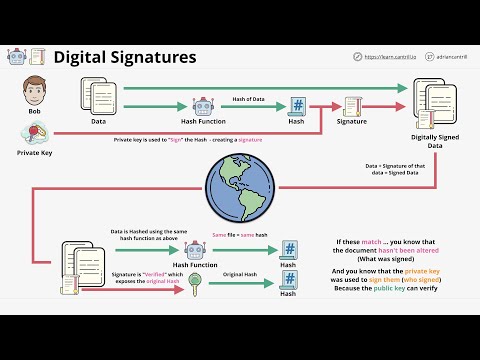
9:27
Digital Signatures - Data authenticity and integrity protection
LearnCantrill
20.2K views

6:32
Security Goals : Confidentiality,Integrity,Availability Explained in Hindi
5 Minutes Engineering
655.8K views

0:59
💻⚡️ AI vs Dark Computing 2.0 #Tech #Research #Adaptability #Capabilities #Integrity #Security Part 4
TEKTHRILL
6 views

0:32
Mastering Cybersecurity Confidentiality, Integrity, Availability Explained
Cyber Guardians
548 views
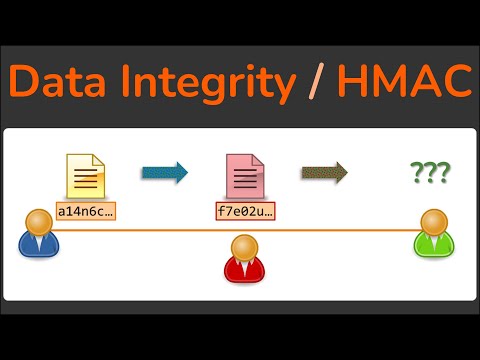
7:24
Data Integrity - How Hashing is used to ensure data isn't modified - HMAC - Cryptography
Practical Networking
77.9K views
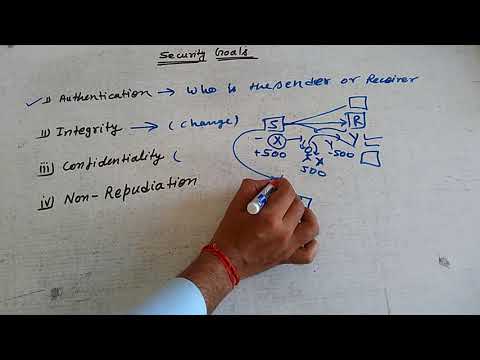
9:11
Security goals of Cryptography (Authentication, Integrity, confidentiality and, Repudiation) Hindi.
Helping Tutorials
12.1K views

12:34
Cybersecurity Architecture: Fundamentals of Confidentiality, Integrity, and Availability
IBM Technology
269.8K views

3:13
Brute-Force Attack on MAC - Cryptographic Hash and Integrity Protection
Ho Quang Ninh
727 views

9:27
CIA Properties | Confidentiality, Integrity, Availability with examples
Gate Smashers
207.4K views

4:20
🔍 Steganography Under Scrutiny File Integrity Verification with Hashing #Steganography #OSINT
Z.S Tech0.5
11 views

0:57
Removing a festival bracelet without altering it's integrity
One Stop 14th Amendment Audit Shop
188.7K views

15:26
Security Protocols: Lecture 2e (Cryptographic Hash Functions & Communication Integrity)
Antonis M
322 views

0:08
Read Managing with Integrity: Insights from America's CEOs Ebook Free
Hillebrand
0 views

2:18
UK's "Integrity Initiative"
teleSUR English
3 views
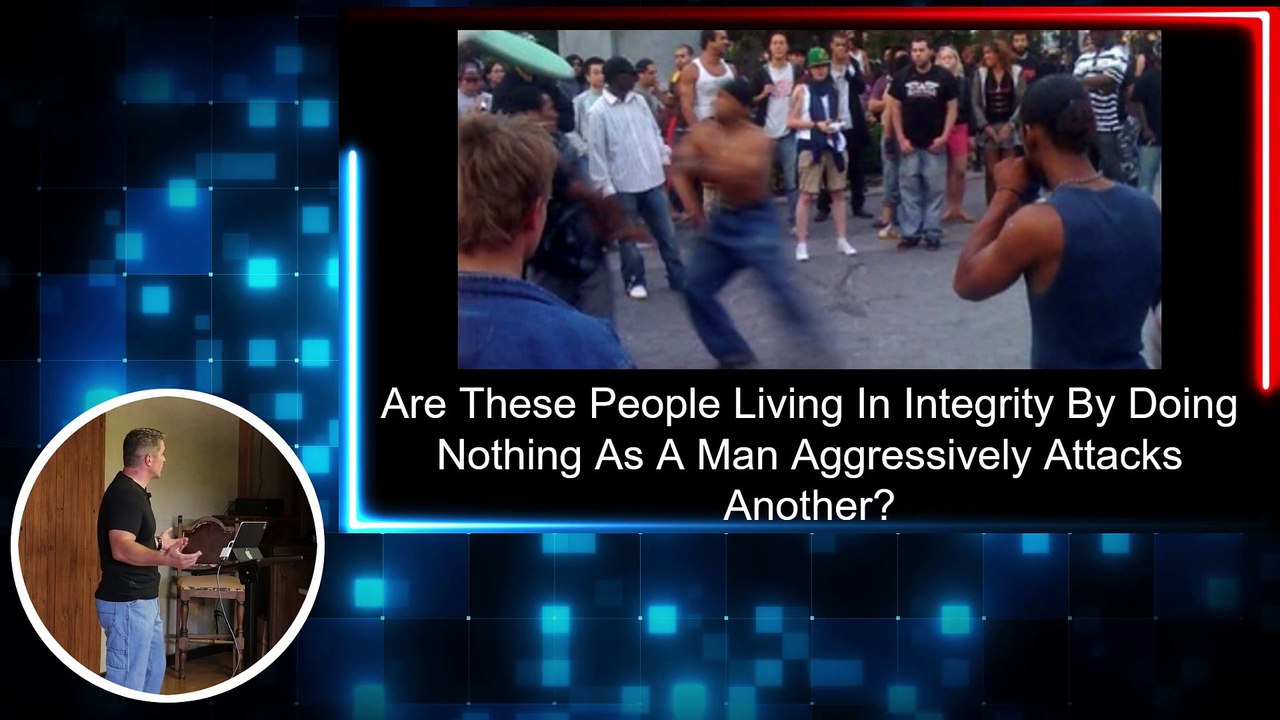
18:29
Building a Better Life: The Key Role of Integrity and Character
Mystics of Texas
0 views

8:25
Boot Integrity - SY0-601 CompTIA Security+ : 3.2
Professor Messer
117.1K views

13:41
Cryptography for Data Integrity & Digital Signature | Philippe Janson
Wandida, EPFL
1.2K views

0:33
Cryptography - Hashing for integrity checking | Answer the Questions Series #shorts #thm #tryhackme
CyberTodd
96 views

9:35
Message integrity in cryptography | message digest
Study Table
10.1K views

0:38
File Integrity Checker GUI | Scan Your Files with One Click 🔍
Esraa Codes
115 views

26:44
Message Integrity and Authentication
Computer Science Learning Videos
336 views

7:49
Integrity Attack
MSCODE
134 views

9:55
CIA Model | Confidentiality, Integrity, Availability, Authenticity and Non-Repudiation | Hindi
Cyberwings Security
70.2K views

2:29
Confidentiality, Integrity, Availability | Security Goals | In HINDI
5 Minutes Programming
550 views

0:58
🤖⚡️ AI's Quantum Field Theory Crisis #Physics #Capabilities #Integrity #Security #Innovation Part 3
TEKTHRILL
3 views

0:58
🤖⚡️ AI's Quantum Field Theory Crisis #Physics #Capabilities #Integrity #Security #Innovation Part 5
TEKTHRILL
1 views

0:47
🔍💔 AI's Last Quantum State #Physics #Exploration #Capability #Understanding #Research #Integrity P5
TEKTHRILL
1 views
0:58
🤖⚡️ AI's Quantum Field Theory Crisis #Physics #Capabilities #Integrity #Security #Innovation Part 2
TEKTHRILL
4 views
0:58
🤖⚡️ AI's Quantum Field Theory Crisis #Physics #Capabilities #Integrity #Security #Innovation Part 1
TEKTHRILL
12 views
0:47
🔍💔 AI's Last Quantum State #Physics #Exploration #Capability #Understanding #Research #Integrity P3
TEKTHRILL
3 views

4:18
cyber security goals- CIA confidentiality,integrity,availability in hindi | MCA/btech/bca/bsc it
Unbeaten Learning
90.6K views

3:42
Securing ISF Data: Encryption and Integrity Methods!
ISF Solution
6 views