Search Results for "Module LWE"
Find videos related to your search query. Browse through our collection of videos matching "Module LWE". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Module LWE"
50 results found

15:43
Post-Quantum Cryptography: Module Learning with Errors (Module-LWE) based Public Key Cryptosystem
Elucyda
2.8K views

10:06
Error: Cannot find module 'bcrypt' | Encrypt and Decrypt Data in Node.js with crypto module
Tech Forum
1.9K views

0:25
8x8 LED Matrix Module, Dot LED Matrix Module #shorts #ytshorts #shortvideo
Tech Craft And Hacks
1.8K views

57:46
Vinod Vaikuntanathan / Efficient Fully Homomorphic Encryption from (Standard) LWE 5
Mathnet Korea
363 views

29:57
Lecture 5. SIS/LWE and lattices (The Mathematics of Lattice-Based Cryptography)
Cryptography 101
1.4K views

2:26:01
Virtual Machine Reset Vulnerabilities; Subspace LWE; Cryptography Against Continuous Memory Attacks
Microsoft Research
314 views

59:35
Vinod Vaikuntanathan / Efficient Fully Homomorphic Encryption from (Standard) LWE 4
Mathnet Korea
244 views

28:01
Vinod Vaikuntanathan / Efficient Fully Homomorphic Encryption from (Standard) LWE 6 -1
Mathnet Korea
110 views
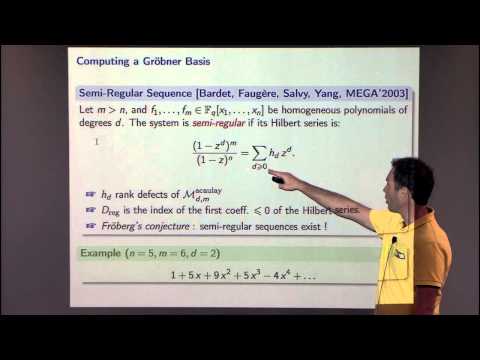
37:16
Algebraic Algorithms for LWE
Simons Institute for the Theory of Computing
926 views

1:00:15
Vinod Vaikuntanathan / Efficient Fully Homomorphic Encryption from (Standard) LWE 3
Mathnet Korea
304 views

56:49
Lattice Attacks for Variants of LWE
Microsoft Research
2.2K views

5:57
Criptografia Pós-Quântica: Os Segredos do Learning with Errors (LWE) e a Segurança Digital do Futuro
IA Aplicada | Guilherme Favaron
71 views
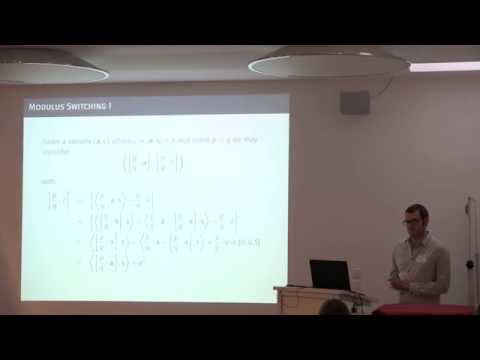
43:39
01 Albrecht on The BKW Algorithm and Variants for Solving LWE
ECRYPT
709 views

24:41
Lecture 3. Learning With Errors (LWE) Problem (The Mathematics of Lattice-Based Cryptography)
Cryptography 101
3.6K views

1:00:30
Vinod Vaikuntanathan / Efficient Fully Homomorphic Encryption from (Standard) LWE 6
Mathnet Korea
528 views

21:55
Predicate Encryption for Circuits from LWE
IACR
380 views

1:10:23
A Survey on Ring-LWE Cryptography
Microsoft Research
6.2K views

31:55
#44 Public Key Encryption from LWE | Part 1 | Quantum Algorithms & Cryptography
NPTEL-NOC IITM
1.1K views

10:50
Cryptography #Module 2 5
ECE SJBIT
18 views

1:14:00
TOC MODULE 1 BCS503 Theory of Computation | 22 Scheme VTU 5th SEM CSE
Afnan Marquee
68.0K views

9:44
IDEA - International Data Encryption Algorithm - Basic Structure (KTU CSE 409 Cryptography-Module 2)
KTU Computer Science Tutorials
6.0K views

32:17
TOC MODULE 2 BCS503 Theory of Computation | 22 Scheme VTU 5th SEM CSE
Afnan Marquee
32.1K views

1:11
Palo Alto Networks Network Security Fundamentals Module 3 Quiz Answers
Course Fry
385 views

18:08
Euler's Theorem With Examples in Modular Arithmetic|| B22mats101 module 4|Cryptography|Dr.Sujata T
MATHS FOR ALL
8.8K views

4:13
Symmetric and Asymmetric Encryption | Understanding Cryptography | Blockchain Basics - Module 1
Web3 Entirety
44 views

23:57
Advanced Encryption Standard(AES)-Mix Column Transformation- (KTU CSE 409 Cryptography-Module 2)
KTU Computer Science Tutorials
4.1K views

0:16
Multimodule in Jeti module bay
Eury
2.2K views

1:41
Module 5: What is asymmetric key encryption?
Simple Security
441 views

7:34
Security in Digital Image Processing:Importance of Digital Image Security: Module V,Lecture 5,EC703A
Dr. SANGITA ROY
28 views

34:49
Cryptography & Network Security - Unit1 -Introduction to Cryptography-Module 1 - 13-07-2020-Session4
Digital Class CSE 1
61 views

18:38
Information and Network Security , Module 1, Introduction
GNS S
173 views

4:53
NodeJs - Symmetric Encryption (Module Crypto)
Aman Kharbanda
12.1K views

4:04
18EC744 CRYPTOGRAPHY Module 5 Important Ques + Ans #vtu #importantquestions #engineering
Edu Star
43 views

20:10
Saber on ARM: CCA secure module lattice based key encapsulation on ARM
IACR
327 views

1:16:12
Free Short Course: Cryptography - Module 3 (without Q&A)
ITMastersCSU
817 views

0:11
How to generate electricity with a peltier module #project #experiment #tech #ytshort
The magic project
977.4K views

1:15
NodeJS : Module not found: Error: Can't resolve 'crypto' in
Hey Delphi
243 views

5:58
Module 4.9. Distribution of Secret Keys Using Public-Key Cryptography|S8 ECE | SECURE COMMUNICATION
bushara abdulrahim
2.6K views
2:34
CS 409 CNS module 1 Differential and linear cryptanalysis
Dept. of Computer Science & Engineering, CCE
8.2K views

23:11
INS Module 1 : Taxonomy of Cryptography & Cryptanalysis
Sumangala Biradar
1.7K views

16:58
Deterministic Finite Automata|LEC-7|Formal Languages andAutomata Theory, VTU syllabus module - 1
Vijaya Prasad Lectures
2.6K views

9:30
Analyse d'une Situation d'hygiène - Module 8 IFAS/IFAP - Aide Soignant & Auxiliaire de Puériculture
Objectif Soignant
18.0K views

3:36
Module 4.3 Requirements of Public key cryptosystems|S8 ECE|SECURE COMMUNICATION KTU|ECT434
bushara abdulrahim
2.4K views

4:51
Module 5: What is Kerberos?
Simple Security
46.8K views

10:28
Module 5.2 Message Authentication Functions
bushara abdulrahim
2.9K views

1:09:37
CompTIA Security+ Full Course for Beginners - Module 1 - Fundamental Security Concepts
BurningIceTech
31.3K views

0:46
Client Password Reset Module For WHMCS | Securely Reset Client Passwords with Ease | Modules Stack
Modules Stack
19 views

8:48
Security in Digital Image Processing : Steganography, Module V Lecture 8 EC 605C
Dr. SANGITA ROY
31 views
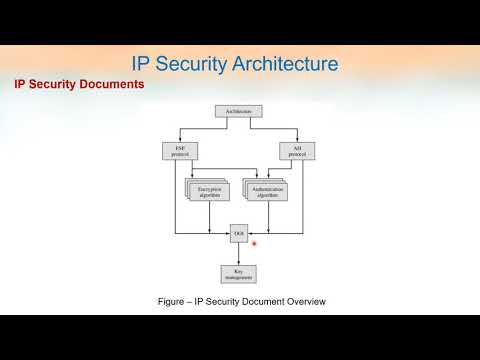
34:14
CNS module 5part 4 IP Security
Iris -jose
113 views
8:33
CS 409 CNS module 1 Introduction to Security
Dept. of Computer Science & Engineering, CCE
6.5K views