Search Results for "IoT Security Challenges"
Find videos related to your search query. Browse through our collection of videos matching "IoT Security Challenges". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "IoT Security Challenges"
50 results found

0:16
🔐 Call for Papers: IoT Security & Privacy | Publish in Computers, Materials & Continua 🚀#shorts #iot
Cyber Sage
4 views

2:21
What is Internet of Thing (IOT) | How It Works | (IOT) Explained
Techno Gibran
15 views

0:15
IOT Product Development with Programming as syllabus book MOBILE APPLICATION DEVELOPMENT FOR IOT
hightecheasypublishing
15 views

0:16
IOT Home Automation #arduino #project #iot #technology #ytshorts #ideas
XiLiR Technologies
536.0K views

6:14
Swachh bharat dustbin with wet & dry notifications Over IoT| IEEE Projects Hyderabad | Iot Projects
Cloud Technologies
110 views
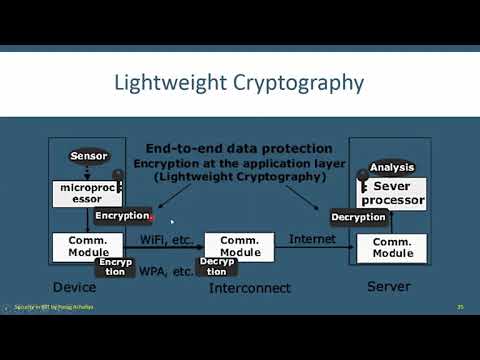
13:26
Lightweight Cryptography, Challenges in Designing IoT Applications
Parag Achaliya
7.5K views

24:37
Information Security Lec 05: Low, Moderate & High Security Levels | Computer Security Challenges
Tech CS&IT
2.2K views

1:38
Ethical Hacking and Cyber Security Full Course In Bangla | IoT, Cloud Security Course In Bangla
InfoSec BD
1.3K views

3:23
Security Sector in Mozambique: Requirements and Challenges to Manage a Security Company
MarcoPolis Country Reports
7 views
0:11
How to make IOT based Affordable Home Security System with message alert
The Neo Studios
156.9K views

34:53
Security implications of IOT in a 5G future (NCSC Cybersecurity Conference)
BSI Group
323 views
0:40
Post-Quantum Crypto: The Future of Industrial IoT Security!
computer science
29 views
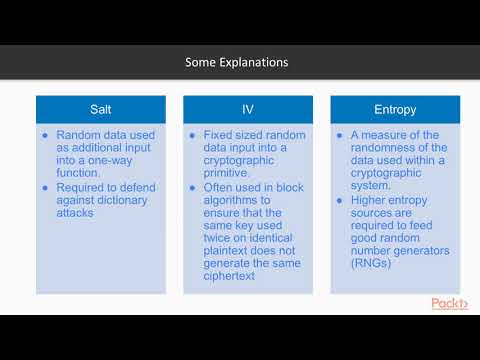
11:53
Security Engineering for the IoT: Fundamentals of Cryptography|packtpub.com
Packt
450 views
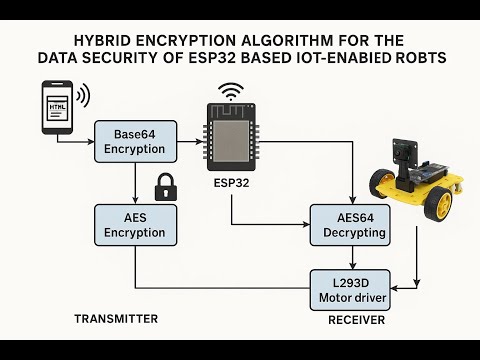
4:01
HVS-3272. Hybrid Encryption Algorithm for the Data Security of ESP32 Based IOT-Enabled Robots
HVS Technologies
184 views

3:36
What Is The Role Of Encryption In IoT Security? - Emerging Tech Insider
Emerging Tech Insider
30 views

0:39
Future Trends- Quantum, IoT, AI in Security
CyberGuard
1 views

0:36
mandurah security system, home cctv security systems mandurah, cctv security systems mandurah, mandurah security systems, cctv system mandurah
lockdownse
1 views

8:01
Web Security-Security Threats and their solution in hindi-Security Policy-computer network security
Unbeaten Learning
77.8K views

2:40
How can HSMs help with the biggest security challenges of post-quantum cryptography?
Utimaco
251 views

55:57
Obvious in Hindsight From Side Channel Attacks to the Security Challenges Ahead
IACR
2.6K views

0:14
The Challenges of Quantum Computing: Security and Quantum Cryptography
Dev Job Seekers
107 views

7:04
Post-Quantum Cryptography- Challenges, Advantages and the Impact on Data Security
WENNSecurity
58 views

9:29
Cryptography in Data Security: Key Aspects, Categories, Impacts, and Challenges
BDAS
214 views

1:04:43
Challenges and Opportunities from Quantum-Safe Cryptography - Tjerand Silde - NDC Security 2025
NDC Conferences
362 views

6:56
NETWORK SECURITY AND CRYPTOGRAPHY CHALLENGES AND TRENDS ON RECENT TECHNOLOGIES.
Chandana S
20 views

7:11
Network Security And Cryptography Challenges And Trends On Recent Technologies
Vanaja V Gowda
28 views

0:35
Cloud Security Challenges and How to Overcome Them | DigitDefence
pradmin DigitDefence
5 views

9:45
Understanding Cloud Security: Challenges and Solutions | Expert Analysis | Skillfloor
Skillfloor
11 views

0:36
PDF Wireless Networks and Security Issues Challenges and Research Trends EBook
OdisNathanialShehane
2 views

0:44
The Challenges of Cyber Security
Priest Rhian
3 views
9:42
The challenges of food security
Astro AWANI
2 views

11:21
Cyber Security and Related Challenges- Realcomm and 2024Sight
jimyoung_realcomm
7 views
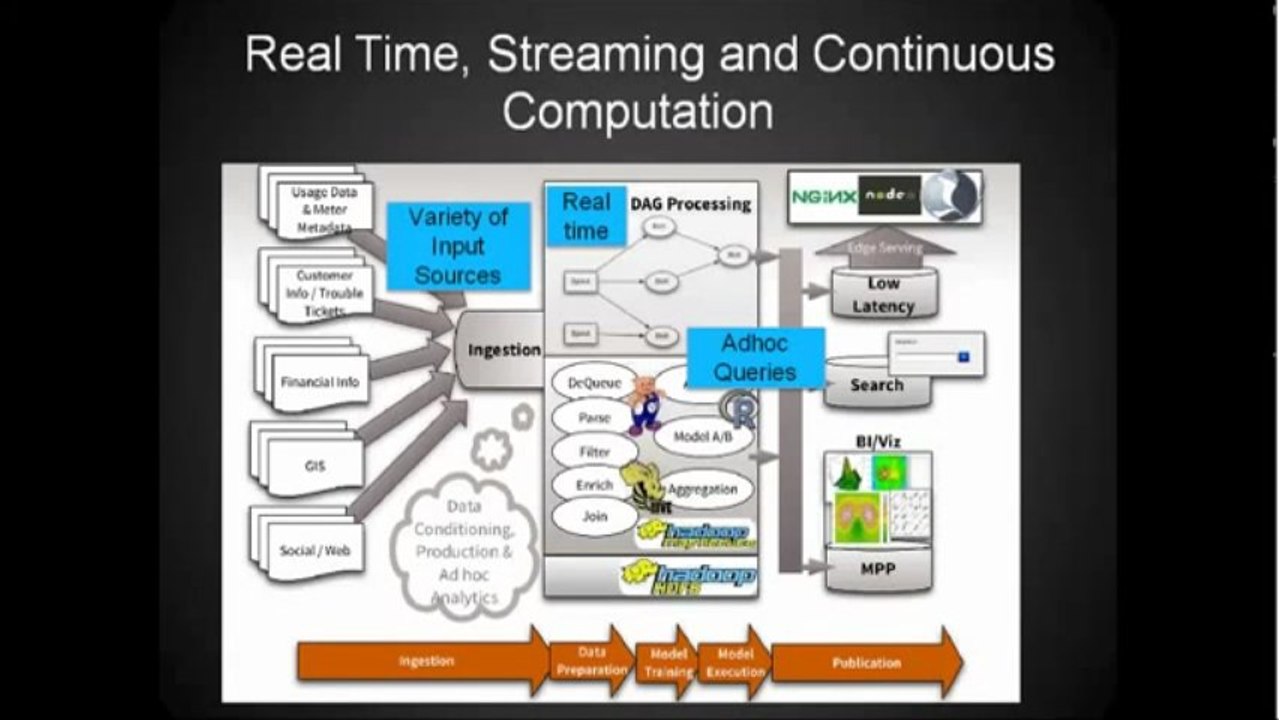
21:00
Big Data Security Challenges and Recommendations!
iviztech
35 views

2:18
Mobile World Congress: security challenges in a hyper-connected world
euronews (in English)
11 views

18:40
ICAP Information Security – Opportunities & Challenges 02
ICAP Pakistan
57 views

15:00
ICAP Information Security – Opportunities & Challenges 07
ICAP Pakistan
57 views

12:25
USENIX Security '24 - The Challenges of Bringing Cryptography from Research Papers to Products:...
USENIX
148 views

2:02
Manipur CRPF Attack: Addressing Security Challenges, Insights from CRPF IG | Oneindia News
Oneindia
491 views
1:01
How Do MOSFETs Work? #mosfet #electronics #IoT
Robonyx
2.3M views

0:39
Arduino Snake Game with 8x8 LED Matrix & Joystick | DIY Classic Game!#shorts #iot
IoT tech
4.2K views
3:01
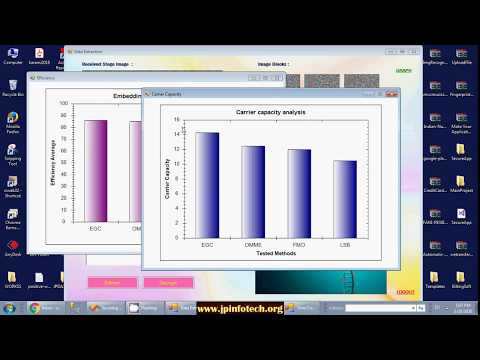
Securing Data in Internet of Things (IoT) Using Cryptography and Steganography Techniques | C#.net
JP INFOTECH PROJECTS
1.9K views

10:53
What is Cryptography? | Chapter-5 | Class-10 | Cryptography Explained | #cryptography #iot #olevel
Zed-King Institute
317 views

0:15
IOT Smart Parking, esp8266, Arduino | best Engineering Project ever #ideas #trending #innovation
XiLiR Technologies
964.7K views
23:15
Post-Quantum Cryptography in IoT world - Dr. Reza Azarderakhsh, PQSecure Technologies
Arm Research
581 views

10:52
Network Information Hiding, Chapter 10a (Introduction to CPS/IoT Steganography)
Steffen Wendzel
472 views

1:58
Allegro Cryptography Engine – ACE™ FIPS Validated Cryptography for IoT Applications
Allegro Software
110 views

34:39
Cryptography careers and IoT vulnerabilities | Cyber Work Podcast
Infosec
4.0K views

25:46
Understanding the role Cryptographic Keys in the IoT Secure World
Secure Thingz
2.7K views
9:12
10 Use Cases for AI Agents: IoT, RAG, & Disaster Response Explained
IBM Technology
128.1K views

28:30
IoT und sicherheit
DEB club
1 views
Page 1